
- Understanding Azure Deny Assignments
Return to AZ-104 Tutorial
The purpose of a deny assignment is to attach a set of deny actions to a user, group, or service principal at a particular scope similar to a role assignment, for denying access. The Azure Deny assignments are used to prevent users from doing particular Azure resource operations, even if a role assignment permits them access.

Overview of Azure Deny Assignments
In Azure, “deny assignments” are a type of access control feature that allows you to restrict access to certain resources in your Azure environment. Deny assignments are used to prevent specific users or groups from accessing a particular resource or resource group, even if they have been granted permission to do so through other means, such as an allow assignment.
Deny assignments work by specifying a set of deny rules that apply to a particular resource or resource group. These rules can be based on a variety of criteria, including user or group membership, IP address, or other attributes. When a user or group attempts to access a resource that is covered by a deny rule, the access request is automatically denied, regardless of any other permissions they may have.
Deny assignments can be useful in a variety of scenarios, such as when you need to restrict access to sensitive data or resources, or when you want to enforce compliance with regulatory requirements or company policies. They can also be used in conjunction with allow assignments to create a more fine-grained access control strategy.
One important thing to keep in mind when working with deny assignments is that they can be complex to manage and troubleshoot, particularly when you are dealing with multiple rules or overlapping permissions. It is therefore important to carefully plan your access control strategy and regularly review your deny assignments to ensure that they are still meeting your needs.
Steps to Create Deny Assignments
Here are the steps to create deny assignments in Azure:
- Identify the resource or resource group that you want to restrict access to.
- Navigate to the Access Control (IAM) tab for that resource or resource group in the Azure portal.
- Click the “Add” button to add a new role assignment.
- Select the role that you want to assign. This can be a built-in Azure role or a custom role that you have created.
- In the “Assign access to” section, select the user or group that you want to assign the role to. This can be a specific user or group, or you can use a service principal.
- In the “Add a condition” section, click “Add” to add a new deny assignment.
- Select the type of condition that you want to add. This can include things like IP address range, user or group membership, or specific tags.
- Specify the details of the condition, such as the IP address range or the name of the user or group.
- Click “Add” to add the deny assignment to the role assignment.
- Review the details of the role assignment and click “Create” to save the changes.
Once you have created the deny assignment, it will take effect immediately and users or groups that match the conditions of the deny rule will be prevented from accessing the specified resource or resource group. You can modify or remove the deny assignment at any time by navigating to the Access Control (IAM) tab for the resource or resource group and editing the role assignment.
All Principals
All Principals is a system-defined principal introduced to support deny assignments. The All Principal represents all users, groups, service principals, and managed identities in an Azure AD directory. Therefore, if the principal ID is a zero GUID 00000000-0000-0000-0000-000000000000 and the principal type is SystemDefined, then the principal represents all principals. Note, we can combine All Principals with ExcludePrincipals to deny all principals except some users.
Limitation of All Principals –
- Can be used only in Principals and cannot be used in ExcludePrincipals.
- Principals[i].Type must be set to SystemDefined.
Properties of Deny Assignments
| DenyAssignmentName | Yes | String | Displays name of the deny assignment. Such names must be unique for a given scope. |
| Description | No | String | The description of the deny assignment. |
| Permissions.Actions | At least one Actions or one DataActions | String[] | An array of strings that specify the management operations to which the deny assignment blocks access. |
| Permissions.NotActions | No | String[] | An array of strings that specify the management operations to exclude from the deny assignment. |
| Permissions.DataActions | At least one Actions or one DataActions | String[] | An array of strings that specify the data operations to which the deny assignment blocks access. |
| Permissions.NotDataActions | No | String[] | An array of strings that specify the data operations to exclude from the deny assignment. |
| Scope | No | String | A string that specifies the scope that the deny assignment applies to. |
| DoNotApplyToChildScopes | No | Boolean | Specifies whether the deny assignment applies to child scopes. Default value is false. |
| Principals[i].Id | Yes | String[] | An array of Azure AD principal object IDs (user, group, service principal, or managed identity) to which the deny assignment applies. Set to an empty GUID 00000000-0000-0000-0000-000000000000 to represent all principals. |
| Principals[i].Type | No | String[] | An array of object types represented by Principals[i].Id. Set to SystemDefined to represent all principals. |
| ExcludePrincipals[i].Id | No | String[] | An array of Azure AD principal object IDs (user, group, service principal, or managed identity) to which the deny assignment does not apply. |
| ExcludePrincipals[i].Type | No | String[] | An array of object types represented by ExcludePrincipals[i].Id. |
| IsSystemProtected | No | Boolean | Specifies whether this deny assignment was created by Azure and cannot be edited or deleted. Currently, all deny assignments are system protected. |

AZ-104 Exam Practice Questions
Question: You are a cloud administrator for a company and want to ensure that a specific group of users cannot create new resources in a specific resource group in Azure. Which Azure feature can you use to achieve this?
A) Azure Resource Locks
B) Azure Policy
C) Azure Role-Based Access Control (RBAC) with Deny Assignments
D) Azure Blueprint
Answer: C) Azure Role-Based Access Control (RBAC) with Deny Assignments. Deny Assignments allow you to block specific actions on a specific scope, such as a resource group, which is what is needed in this scenario.
Question: You have an Azure subscription that is used by multiple departments in your organization. You want to ensure that one particular department cannot deploy resources with a specific tag. Which Azure feature can you use to achieve this?
B) Azure Policy with Deny Assignments
C) Azure Role-Based Access Control (RBAC)
Answer: B) Azure Policy with Deny Assignments. Azure Policy allows you to define and enforce policies that can help you meet organizational or regulatory compliance goals. Deny Assignments can be used in conjunction with policies to prevent certain actions, such as deploying resources with a specific tag.
Question: You are a security analyst for a company and need to ensure that all virtual machines in your Azure environment are encrypted using Azure Disk Encryption. However, you want to make sure that the owner of a virtual machine can still access the disk if necessary. Which Azure feature can you use to achieve this?
D) Azure Deny Assignments
Answer: D) Azure Deny Assignments. Deny Assignments can be used to prevent unauthorized access to virtual machine disks while still allowing the owner to access them. By creating a Deny Assignment that denies the “Microsoft.Compute/virtualMachines/encrypt/action” action for everyone except the owner of the virtual machine, only the owner can encrypt or decrypt the virtual machine disk, but others are denied access.
Question: You are a cloud administrator for a company and need to ensure that certain users cannot access a particular Azure resource. Which Azure feature can you use to achieve this?
Answer: C) Azure Role-Based Access Control (RBAC) with Deny Assignments. Deny Assignments can be used in conjunction with RBAC to prevent certain users from accessing a particular Azure resource by denying the “Microsoft.Authorization/*/read” action for the group of users.
Question: You have a critical Azure resource that should never be deleted accidentally. Which Azure feature can you use to prevent deletion of this resource?
Answer: A) Azure Resource Locks. Resource Locks allow you to lock a resource to prevent accidental deletion or modification. By applying a lock to the critical Azure resource, it cannot be deleted accidentally, even by authorized users.
Reference: Microsoft Documentation
Prepare for Assured Success
How to lock down a single confidential Resource Group in Azure
This is a short one, but something I couldn’t figure out without testing it first.
Let’s assume a scenario where a company has a single Azure subscription. They also then have a single Azure tenant (meaning, a single Azure AD). Within this Azure subscription, they’ve built services for years and now have more than 100 resource groups.
They’ve now built another service that requires 10 resource groups – for testing, production, QA, and all sorts of things. As this service is very different and will store confidential data, they have to lock down access to the service within the Azure subscription. Not even admins can peek at the databases or any of the services within the resource groups – unless granted access.
How do we configure this?
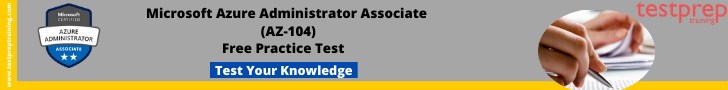
Let’s start by taking a look at one of those resource groups we need to lockdown. I have one resource group named azuresentinel , and it’s hosting my Azure Sentinel and relevant services for that. Checking under Access control (IAM) on Azure Portal, we can see the default permissions:
A few inherited permissions from the Azure Subscription level. One from a Management Group and a few settings at the root level.
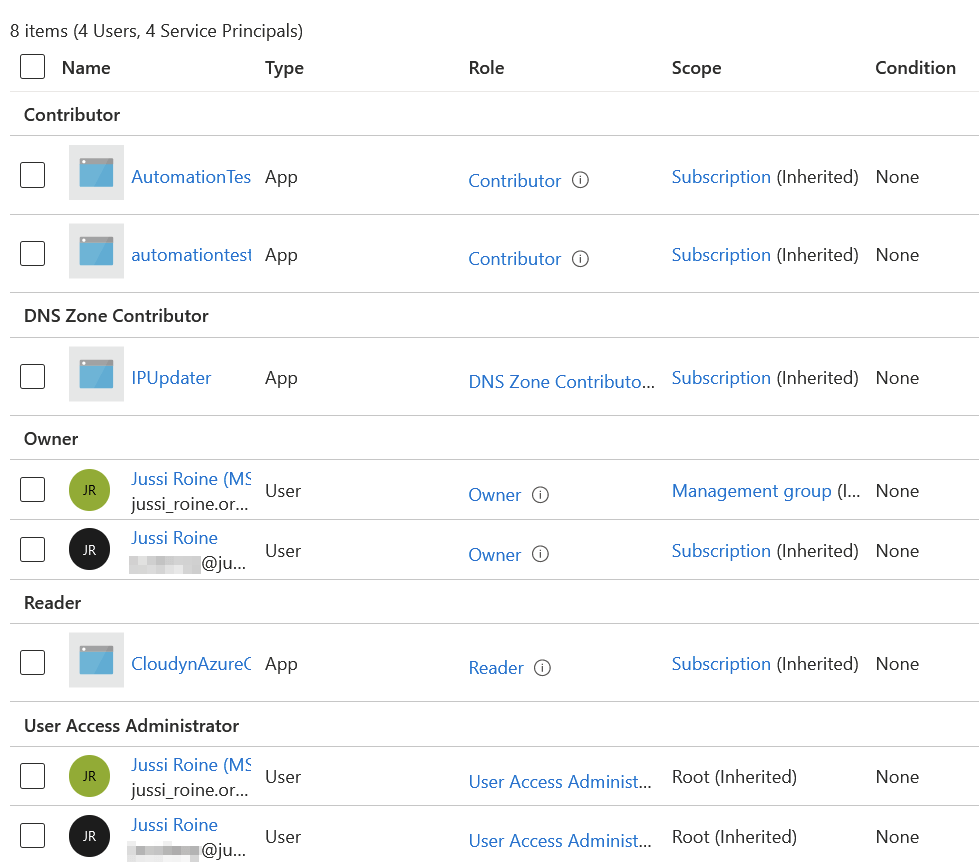
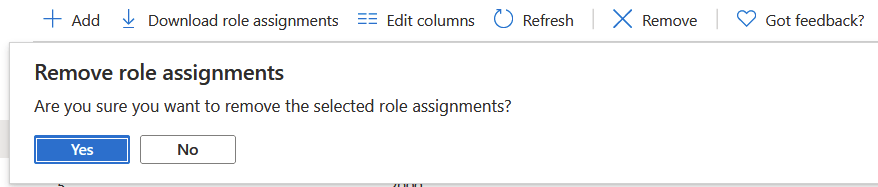
I want to remove the legacy Cloudyn account, which is no longer a useful service for me (the third from the bottom in the list). I select the Reader-level permissions and click on Remove in the top toolbar. Only to get this message:
Because the permission is inherited (from the Azure subscription, we only have one), the inheritance cannot be broken at a lower level, like a Resource Group.
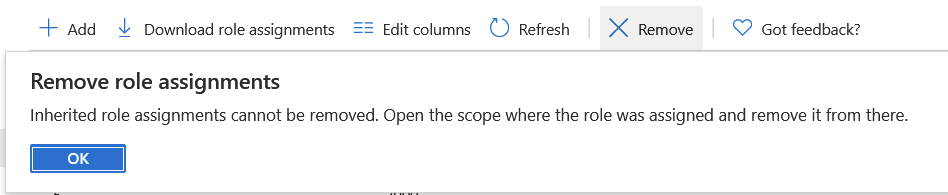
Let’s see on the Subscription level if I can tweak this permission higher up in the chain. By selecting the same account and access, I can remove it – at the subscription level:
But this takes away ALL access for said account, everywhere! I only want to remove access for one Resource Group.
Going back to the Resource Group > IAM view, I see there is another tab called Deny assignments . Perhaps I can create a classic Deny setting within a Resource Group to remove access for specific accounts.
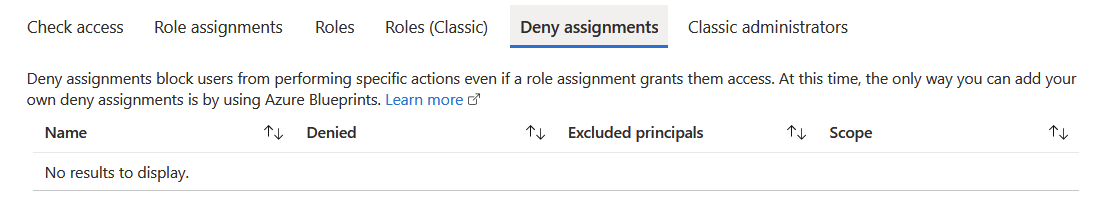
The description implies this would work. But it also cleverly states “ at this time “, as if some sort of an update is impending for this feature. Thus, the only option is to create a new Azure Blueprint, and assign that to the Resource Group.
Seems awfully clumsy – I just want to remove permissions for 10 users, but not for 2 other users within one Resource Group. And creating a Blueprint just for this feels overkill.
Taking a look at creating a Blueprint, it clearly states that I need to select a lock assignment . The guidance, which is found here , then lists the lock levels: don’t lock, read only (for RG), read only (non-RG) and do not delete. None of these remove permissions – they just allocate locks, via assignments, that users don’t accidentally remove something important.
Back to the drawing board
So, it seems impossible to remove permissions for users who have inherited access from the Subscription level. Removing their permissions at the Subscription level would mean they lose all access – and re-adding that might be tricky and time-consuming, especially for admins.
We can, of course, audit access to our confidential and protected RGs. But even then, it would be time-consuming to monitor whether or not someone lists all the resources in an RG, either by accident or on purpose.
Using Azure Blueprints seems to be the preferred Microsoft approach, but it isn’t tackling the issue – it’s simply adding another method for protecting for accidental deletions mostly. It seems impossible to lock down a single Resource Group unless locking down a whole Subscription by removing all accessible for everyone (and granting those permissions later at resource levels).
The solution? Provision a new Azure Subscription, and move your confidential Resource Groups there. Lockdown access at the Subscription level.
I found a few feedback items ( here , here ) on this very same challenge from recent years. But no other fix than to deploy Blueprints for locks.
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications You must be signed in to change notification settings
deny-assignments.md
Latest commit, file metadata and controls.
| title | description | author | manager | ms.service | ms.topic | ms.date | ms.author | ms.reviewer |
|---|---|---|---|---|---|---|---|---|
List Azure deny assignments
Similar to a role assignment, a deny assignment attaches a set of deny actions to a user, group, or service principal at a particular scope for the purpose of denying access. Deny assignments block users from performing specific Azure resource actions even if a role assignment grants them access.
This article describes how to list deny assignments.
You can't directly create your own deny assignments. Deny assignments are created and managed by Azure.
How deny assignments are created
Deny assignments are created and managed by Azure to protect resources. You can't directly create your own deny assignments. However, you can specify deny settings when creating a deployment stack, which creates a deny assignment that is owned by the deployment stack resources. Deployment stacks is currently in preview. For more information, see Protect managed resources against deletion .
Compare role assignments and deny assignments
Deny assignments follow a similar pattern as role assignments, but also have some differences.
| Capability | Role assignment | Deny assignment |
|---|---|---|
| Grant access | ✅ | |
| Deny access | ✅ | |
| Can be directly created | ✅ | |
| Apply at a scope | ✅ | ✅ |
| Exclude principals | ✅ | |
| Prevent inheritance to child scopes | ✅ | |
| Apply to assignments | ✅ |
Deny assignment properties
A deny assignment has the following properties:
[!div class="mx-tableFixed"] Property Required Type Description DenyAssignmentName Yes String The display name of the deny assignment. Names must be unique for a given scope. Description No String The description of the deny assignment. Permissions.Actions At least one Actions or one DataActions String[] An array of strings that specify the control plane actions to which the deny assignment blocks access. Permissions.NotActions No String[] An array of strings that specify the control plane action to exclude from the deny assignment. Permissions.DataActions At least one Actions or one DataActions String[] An array of strings that specify the data plane actions to which the deny assignment blocks access. Permissions.NotDataActions No String[] An array of strings that specify the data plane actions to exclude from the deny assignment. Scope No String A string that specifies the scope that the deny assignment applies to. DoNotApplyToChildScopes No Boolean Specifies whether the deny assignment applies to child scopes. Default value is false. Principals[i].Id Yes String[] An array of Microsoft Entra principal object IDs (user, group, service principal, or managed identity) to which the deny assignment applies. Set to an empty GUID 00000000-0000-0000-0000-000000000000 to represent all principals. Principals[i].Type No String[] An array of object types represented by Principals[i].Id. Set to SystemDefined to represent all principals. ExcludePrincipals[i].Id No String[] An array of Microsoft Entra principal object IDs (user, group, service principal, or managed identity) to which the deny assignment does not apply. ExcludePrincipals[i].Type No String[] An array of object types represented by ExcludePrincipals[i].Id. IsSystemProtected No Boolean Specifies whether this deny assignment was created by Azure and cannot be edited or deleted. Currently, all deny assignments are system protected.
The All Principals principal
To support deny assignments, a system-defined principal named All Principals has been introduced. This principal represents all users, groups, service principals, and managed identities in a Microsoft Entra directory. If the principal ID is a zero GUID 00000000-0000-0000-0000-000000000000 and the principal type is SystemDefined , the principal represents all principals. In Azure PowerShell output, All Principals looks like the following:
All Principals can be combined with ExcludePrincipals to deny all principals except some users. All Principals has the following constraints:
- Can be used only in Principals and cannot be used in ExcludePrincipals .
- Principals[i].Type must be set to SystemDefined .
List deny assignments
Follow these steps to list deny assignments.
You can't directly create your own deny assignments. Deny assignments are created and managed by Azure. For more information, see Protect managed resources against deletion .
Azure portal
Prerequisites.
To get information about a deny assignment, you must have:
- Microsoft.Authorization/denyAssignments/read permission, which is included in most Azure built-in roles .
List deny assignments in the Azure portal
Follow these steps to list deny assignments at the subscription or management group scope.
In the Azure portal, open the selected scope, such as resource group or subscription.
Select Access control (IAM) .
Select the Deny assignments tab (or select the View button on the View deny assignments tile).
If there are any deny assignments at this scope or inherited to this scope, they'll be listed.
:::image type="content" source="./media/deny-assignments/access-control-deny-assignments.png" alt-text="Screenshot of Access control (IAM) page and Deny assignments tab that lists deny assignments at the selected scope." lightbox="./media/deny-assignments/access-control-deny-assignments.png":::
To display additional columns, select Edit Columns .
:::image type="content" source="./media/deny-assignments/deny-assignments-columns.png" alt-text="Screenshot of deny assignments columns pane that shows how to add columns to list of deny assignments." lightbox="./media/deny-assignments/deny-assignments-columns.png":::
| Column | Description |
|---|---|
| Name of the deny assignment. | |
| User, group, system-defined group, or service principal. | |
| Name of the security principal that is included in the deny assignment. | |
| Unique identifier for the deny assignment. | |
| Whether there are security principals that are excluded from the deny assignment. | |
| Whether the deny assignment is inherited to subscopes. | |
| Whether the deny assignment is managed by Azure. Currently, always Yes. | |
| Management group, subscription, resource group, or resource. |
Add a checkmark to any of the enabled items and then select OK to display the selected columns.
List details about a deny assignment
Follow these steps to list additional details about a deny assignment.
Open the Deny assignments pane as described in the previous section.
Select the deny assignment name to open the Users page.
:::image type="content" source="./media/deny-assignments/deny-assignment-users.png" alt-text="Screenshot of Users page for a deny assignment that lists the applies to and excludes." lightbox="./media/deny-assignments/deny-assignment-users.png":::
The Users page includes the following two sections.
| Deny setting | Description |
|---|---|
| Security principals that the deny assignment applies to. | |
| Security principals that are excluded from the deny assignment. |
System-Defined Principal represents all users, groups, service principals, and managed identities in an Azure AD directory.
To see a list of the permissions that are denied, select Denied Permissions .
:::image type="content" source="./media/deny-assignments/deny-assignment-denied-permissions.png" alt-text="Screenshot of Denied Permissions page for a deny assignment that lists the permissions that are denied." lightbox="./media/deny-assignments/deny-assignment-denied-permissions.png":::
| Action type | Description |
|---|---|
| Denied control plane actions. | |
| Control plane actions excluded from denied control plane actions. | |
| Denied data plane actions. | |
| Data plane actions excluded from denied data plane actions. |
For the example shown in the previous screenshot, the following are the effective permissions:
- All storage actions on the data plane are denied except for compute actions.
To see the properties for a deny assignment, select Properties .
:::image type="content" source="./media/deny-assignments/deny-assignment-properties.png" alt-text="Screenshot of Properties page for a deny assignment that lists the properties." lightbox="./media/deny-assignments/deny-assignment-properties.png":::
On the Properties page, you can see the deny assignment name, ID, description, and scope. The Does not apply to children switch indicates whether the deny assignment is inherited to subscopes. The System protected switch indicates whether this deny assignment is managed by Azure. Currently, this is Yes in all cases.
Azure PowerShell
- Microsoft.Authorization/denyAssignments/read permission, which is included in most Azure built-in roles
- PowerShell in Azure Cloud Shell or Azure PowerShell
List all deny assignments
To list all deny assignments for the current subscription, use Get-AzDenyAssignment .
List deny assignments at a resource group scope
To list all deny assignments at a resource group scope, use Get-AzDenyAssignment .
List deny assignments at a subscription scope
To list all deny assignments at a subscription scope, use Get-AzDenyAssignment . To get the subscription ID, you can find it on the Subscriptions page in the Azure portal or you can use Get-AzSubscription .
You must use the following version:
- 2018-07-01-preview or later
- 2022-04-01 is the first stable version

List a single deny assignment
To list a single deny assignment, use the Deny Assignments - Get REST API.
Start with the following request:
Within the URI, replace {scope} with the scope for which you want to list the deny assignments.
[!div class="mx-tableFixed"] Scope Type subscriptions/{subscriptionId} Subscription subscriptions/{subscriptionId}/resourceGroups/myresourcegroup1 Resource group subscriptions/{subscriptionId}/resourceGroups/myresourcegroup1/providers/Microsoft.Web/sites/mysite1 Resource
Replace {deny-assignment-id} with the deny assignment identifier you want to retrieve.
List multiple deny assignments
To list multiple deny assignments, use the Deny Assignments - List REST API.
Start with one of the following requests:
With optional parameters:
Replace {filter} with the condition that you want to apply to filter the deny assignment list.
[!div class="mx-tableFixed"] Filter Description (no filter) Lists all deny assignments at, above, and below the specified scope. $filter=atScope() Lists deny assignments for only the specified scope and above. Does not include the deny assignments at subscopes. $filter=assignedTo('{objectId}') Lists deny assignments for the specified user or service principal. If the user is a member of a group that has a deny assignment, that deny assignment is also listed. This filter is transitive for groups which means that if the user is a member of a group and that group is a member of another group that has a deny assignment, that deny assignment is also listed. This filter only accepts an object ID for a user or a service principal. You cannot pass an object ID for a group. $filter=atScope()+and+assignedTo('{objectId}') Lists deny assignments for the specified user or service principal and at the specified scope. $filter=denyAssignmentName+eq+'{deny-assignment-name}' Lists deny assignments with the specified name. $filter=principalId+eq+'{objectId}' Lists deny assignments for the specified user, group, or service principal.
List deny assignments at the root scope (/)
Elevate your access as described in Elevate access to manage all Azure subscriptions and management groups .
Use the following request:
Replace {filter} with the condition that you want to apply to filter the deny assignment list. A filter is required.
[!div class="mx-tableFixed"] Filter Description $filter=atScope() List deny assignments for only the root scope. Does not include the deny assignments at subscopes. $filter=denyAssignmentName+eq+'{deny-assignment-name}' List deny assignments with the specified name.
Remove elevated access.
- Deployment stacks
Get the Reddit app
Join us in discord here: https://aka.ms/azurediscord.
Deny Assignments ? or Resource Lock?
Hello! If I'm a global admin for all subscriptions in a tenant, what's the best way to quickly make a resource (virtual Machine) read only? eg. if I stop it, it remains stopped or it cannot be altered (unless someone is a global admin) so no deletions, etc...? Was thinking of resource lock but would the better way be a deny assignment? If so, what would I set it to if I want it to be a Role instead of a specific member/person?
By continuing, you agree to our User Agreement and acknowledge that you understand the Privacy Policy .
Enter the 6-digit code from your authenticator app
You’ve set up two-factor authentication for this account.
Enter a 6-digit backup code
Create your username and password.
Reddit is anonymous, so your username is what you’ll go by here. Choose wisely—because once you get a name, you can’t change it.
Reset your password
Enter your email address or username and we’ll send you a link to reset your password
Check your inbox
An email with a link to reset your password was sent to the email address associated with your account
Choose a Reddit account to continue
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Understand resource locking in Azure Blueprints
- 4 contributors
On July 11, 2026, Blueprints (Preview) will be deprecated. Migrate your existing blueprint definitions and assignments to Template Specs and Deployment Stacks . Blueprint artifacts are to be converted to ARM JSON templates or Bicep files used to define deployment stacks. To learn how to author an artifact as an ARM resource, see:
- Deployments
The creation of consistent environments at scale is only truly valuable if there's a mechanism to maintain that consistency. This article explains how resource locking works in Azure Blueprints. To see an example of resource locking and application of deny assignments , see the protecting new resources tutorial.
Resource locks deployed by Azure Blueprints are only applied to non-extension resources deployed by the blueprint assignment. Existing resources, such as those in resource groups that already exist, don't have locks added to them.
Locking modes and states
Locking Mode applies to the blueprint assignment and it has three options: Don't Lock , Read Only , or Do Not Delete . The locking mode is configured during artifact deployment during a blueprint assignment. A different locking mode can be set by updating the blueprint assignment. Locking modes, however, can't be changed outside of Azure Blueprints.
Resources created by artifacts in a blueprint assignment have four states: Not Locked , Read Only , Cannot Edit / Delete , or Cannot Delete . Each artifact type can be in the Not Locked state. The following table can be used to determine the state of a resource:
| Mode | Artifact Resource Type | State | Description |
|---|---|---|---|
| Don't Lock | * | Not Locked | Resources aren't protected by Azure Blueprints. This state is also used for resources added to a or resource group artifact from outside a blueprint assignment. |
| Read Only | Resource group | Cannot Edit / Delete | The resource group is read only and all its properties, except for tags, can't be modified. resources can be added, moved, changed, or deleted from this resource group. |
| Read Only | Non-resource group | Read Only | Except for tags, the resource remains unalterable and cannot be deleted or modified. |
| Do Not Delete | * | Cannot Delete | The resources can be altered, but can't be deleted. resources can be added, moved, changed, or deleted from this resource group. |
Overriding locking states
It's typically possible for someone with appropriate Azure role-based access control (Azure RBAC) on the subscription, such as the 'Owner' role, to be allowed to alter or delete any resource. This access isn't the case when Azure Blueprints applies locking as part of a deployed assignment. If the assignment was set with the Read Only or Do Not Delete option, not even the subscription owner can perform the blocked action on the protected resource.
This security measure protects the consistency of the defined blueprint and the environment it was designed to create from accidental or programmatic deletion or alteration.
Assign at management group
The only option to prevent subscription owners from removing a blueprint assignment is to assign the blueprint to a management group. In this scenario, only Owners of the management group have the permissions needed to remove the blueprint assignment.
To assign the blueprint to a management group instead of a subscription, the REST API call changes to look like this:
The management group defined by {assignmentMG} must be either within the management group hierarchy or be the same management group where the blueprint definition is saved.
The request body of the blueprint assignment looks like this:
The key difference in this request body and one being assigned to a subscription is the properties.scope property. This required property must be set to the subscription that the blueprint assignment applies to. The subscription must be a direct child of the management group hierarchy where the blueprint assignment is stored.
A blueprint assigned to management group scope still operates as a subscription level blueprint assignment. The only difference is where the blueprint assignment is stored to prevent subscription owners from removing the assignment and associated locks.
Removing locking states
If it becomes necessary to modify or delete a resource protected by an assignment, there are two ways to do so.
- Updating the blueprint assignment to a locking mode of Don't Lock
- Delete the blueprint assignment
When the assignment is removed, the locks created by Azure Blueprints are removed. However, the resource is left behind and would need to be deleted through normal means.
How blueprint locks work
An Azure RBAC deny assignments deny action is applied to artifact resources during assignment of a blueprint if the assignment selected the Read Only or Do Not Delete option. The deny action is added by the managed identity of the blueprint assignment and can only be removed from the artifact resources by the same managed identity. This security measure enforces the locking mechanism and prevents removing the blueprint lock outside Azure Blueprints.
The deny assignment properties of each mode are as follows:
| Mode | Permissions.Actions | Permissions.NotActions | Principals[i].Type | ExcludePrincipals[i].Id | DoNotApplyToChildScopes |
|---|---|---|---|---|---|
| Read Only | | SystemDefined (Everyone) | blueprint assignment and user-defined in | Resource group - ; Resource - | |
| Do Not Delete | | SystemDefined (Everyone) | blueprint assignment and user-defined in | Resource group - ; Resource - |
Azure Resource Manager caches role assignment details for up to 30 minutes. As a result, deny assignments deny action's on blueprint resources may not immediately be in full effect. During this period of time, it might be possible to delete a resource intended to be protected by blueprint locks.
Exclude a principal from a deny assignment
In some design or security scenarios, it may be necessary to exclude a principal from the deny assignment the blueprint assignment creates. This step is done in REST API by adding up to five values to the excludedPrincipals array in the locks property when creating the assignment . The following assignment definition is an example of a request body that includes excludedPrincipals :
Exclude an action from a deny assignment
Similar to excluding a principal on a deny assignment in a blueprint assignment, you can exclude specific Azure resource provider operations . Within the properties.locks block, in the same place that excludedPrincipals is, an excludedActions can be added:
While excludedPrincipals must be explicit, excludedActions entries can make use of * for wildcard matching of resource provider operations.
- Follow the protect new resources tutorial.
- Learn about the blueprint lifecycle .
- Understand how to use static and dynamic parameters .
- Learn to customize the blueprint sequencing order .
- Learn how to update existing assignments .
- Resolve issues during the assignment of a blueprint with general troubleshooting .
Was this page helpful?
Additional resources
- Stack Overflow for Teams Where developers & technologists share private knowledge with coworkers
- Advertising & Talent Reach devs & technologists worldwide about your product, service or employer brand
- OverflowAI GenAI features for Teams
- OverflowAPI Train & fine-tune LLMs
- Labs The future of collective knowledge sharing
- About the company Visit the blog
Collectives™ on Stack Overflow
Find centralized, trusted content and collaborate around the technologies you use most.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Get early access and see previews of new features.
Deny Assignment in Azure Databricks - how do I get around this to access storage container?
The client """ has permission to perform action 'Microsoft.Storage/storageAccounts/listKeys/action' on scope '/my/storage/account'; however, the access is denied because of the deny assignment with name 'System deny assignment created by Azure Databricks .....'
What do I need to do to resolve this issue. I successfully loaded a file to the storage container but cannot access it from a python notebook. Here's the error from the notebook.
"shaded.databricks.org.apache.hadoop.fs.azure.AzureException: hadoop_azure_shaded.com.microsoft.azure.storage.StorageException: Server failed to authenticate the request. Make sure the value of Authorization header is formed correctly including the signature."
It appears the "Deny assignment" issue above is the cause? How can I resolve it. Appreciate your help.
I was expecting to be able to access file from a python notebook with "%fs ls /mnt/...." but the command failed.
- azure-databricks
- Are you trying to mount a storage account that is created together with Azure Databricks workspace? Can you post exact error - what I see - it doesn't mention deny assignment – Alex Ott Commented Sep 25, 2023 at 11:05
I encountered the same error while reading a file from an ADLS account, as shown below:

The error is related to authorization. To resolve the issue, I followed the procedure below:
I mounted the ADLS account with Access Key authorization. To obtain the Access Key of the ADLS account, go to the Storage account, click on Access Keys, then click the Show button and copy the Access Key, as shown below:

I used the following code to mount the ADLS account:

I accessed the file from the ADLS account using the code below:
The data was retrieved, as shown below:

- Thanks - In my case the file is already loaded and mounted and I am trying to access it but getting the stated errors. – Baba Commented Sep 25, 2023 at 16:31
- could you please provide the code which you used to mount ADLS account? – Bhavani Commented Sep 26, 2023 at 6:29
Your Answer
Reminder: Answers generated by artificial intelligence tools are not allowed on Stack Overflow. Learn more
Sign up or log in
Post as a guest.
Required, but never shown
By clicking “Post Your Answer”, you agree to our terms of service and acknowledge you have read our privacy policy .
Not the answer you're looking for? Browse other questions tagged azure-databricks or ask your own question .
- The Overflow Blog
- The evolution of full stack engineers
- One of the best ways to get value for AI coding tools: generating tests
- Featured on Meta
- Bringing clarity to status tag usage on meta sites
- Join Stack Overflow’s CEO and me for the first Stack IRL Community Event in...
- Feedback requested: How do you use tag hover descriptions for curating and do...
- Staging Ground Reviewer Motivation
- What does a new user need in a homepage experience on Stack Overflow?
Hot Network Questions
- What is the purpose of long plastic sleeve tubes around connections in appliances?
- Big Transition of Binary Counting in perspective of IEEE754 floating point
- A journal has published an AI-generated article under my name. What to do?
- If a friend hands me a marijuana edible then dies of a heart attack am I guilty of felony murder?
- Are there epistemic vices?
- Disable encryption on wireguard
- Key fob frequency filter design
- Can flood basalt eruptions start in historical timescales?
- Overstaying knowing I have a new Schengen visa
- Is there mathematical significance to the LaGuardia floor tiles?
- Could they free up a docking port on ISS by undocking the emergency vehicle and letting it float next to the station for a little while
- When should I put a biasing resistor - op-amps
- Remove spaces from the 3rd line onwards in a file on linux
- What sci-fi show was Ernie watching in the show My Three Sons?
- 4/4 time change to 6/8 time
- Fantasy book about humans and gnomes entering one another's worlds
- How are you supposed to trust SSO popups in desktop and mobile applications?
- Practice test paper answers all seem incorrect, but provider insists they are ... what am i missing?
- jq - ip addr show in tabular format
- Does a debt exist for a Parking Charge Notice?
- Best memory / storage solution for high read / write throughput application(s)?
- Inspector tells me that the electrician should have removed green screw from the panel
- Long table to fit in two pages
- Paying a parking fine when I don't trust the recipient

IMAGES
VIDEO
COMMENTS
Follow these steps to list deny assignments at the subscription or management group scope. In the Azure portal, open the selected scope, such as resource group or subscription. Select Access control (IAM). Select the Deny assignments tab (or select the View button on the View deny assignments tile).
1. You need to use the Azure Blueprints, you can't directly create your own deny assignments, deny assignments are created and managed by Azure, e.g. Azure Blueprints. The doc explains that: Deny assignments are created and managed by Azure to protect resources. For example, Azure Blueprints and Azure managed apps use deny assignments to ...
Deny assignments block users from performing specific Azure resource actions even if a role assignment grants them access. But you need add this protection in the blueprint definitions of resources created by an Azure Resource Manager template artifact, and the Blueprint resource lock is set during blueprint assignment.
Steps to Create Deny Assignments. Here are the steps to create deny assignments in Azure: Identify the resource or resource group that you want to restrict access to. Navigate to the Access Control (IAM) tab for that resource or resource group in the Azure portal. Click the "Add" button to add a new role assignment.
Going back to the Resource Group > IAM view, I see there is another tab called Deny assignments. Perhaps I can create a classic Deny setting within a Resource Group to remove access for specific accounts. The description implies this would work. But it also cleverly states "at this time", as if some sort of an update is impending for this ...
Deny Assignment; Deny assignments block users from performing specific Azure resource actions even if a role assignment grants them access. For example, if there is a deny assignment on the specific resource group, even the user who has a contributor role on the subscription, this user still will be blocked by the deny assignment. For the ...
Determines if the deny assignment applies to child scopes. Default value is false. properties.excludePrincipals Principal[] Array of principals to which the deny assignment does not apply. properties.isSystemProtected boolean Specifies whether this deny assignment was created by Azure and cannot be edited or deleted. properties.permissions
Note: If users have the required permissions, they can create exemption for their resources. Which make this policy ineffective for that resource. Custom Policy Definition creation . You can follow the steps below to create a custom policy: 1) From the Azure portal, access Azure policy, then definitions blade. 2) Create a new policy definition.
Deny assignments are created and managed by Azure to protect resources. You can't directly create your own deny assignments. However, you can specify deny settings when creating a deployment stack, which creates a deny assignment that is owned by the deployment stack resources. Deployment stacks is currently in preview.
Click the "Details" to check the compliance details. Scroll down on the compliance details page. Under the "Compliance details", there are one or more blocks for policy aliases defined in policy definition respectively. In this case shown above, the policy has to check the resource type (equals to storage account) and minimum TLS version.
Deny assignment modification to allow attach/detach of disks in azure databricks. 02-08-2024 08:29 PM. Our application does storage autoscaling on Azure. We would like to deploy our solution with Azure databricks. But even though the service principal associated with our application has the necessary roles and permissions to attach/detach a ...
Determines if the deny assignment applies to child scopes. Default value is false. properties.excludePrincipals Principal[] Array of principals to which the deny assignment does not apply. properties.isSystemProtected boolean Specifies whether this deny assignment was created by Azure and cannot be edited or deleted. properties.permissions
Azure policy seems like a terrible idea, you could do it, I wouldn't. Owner and User access administrator can remove the lock. This is most likely the best solution but a terrible one regardless The best course is not something anyone is capable of determining since no one knows your architecture design.
Determines if the deny assignment applies to child scopes. Default value is false. Array of principals to which the deny assignment does not apply. Specifies whether this deny assignment was created by Azure and cannot be edited or deleted. An array of permissions that are denied by the deny assignment.
Get the specified deny assignment. Get By Id: Gets a deny assignment by ID. List: Gets all deny assignments for the subscription. List For Resource: Gets deny assignments for a resource. List For Resource Group: Gets deny assignments for a resource group. List For Scope: Gets deny assignments for a scope.
Create a blueprint: First, create a blueprint that defines the desired state for your resources, including the "Deny Assignment" policy. This blueprint will be used to provision and manage your resources. Define a policy definition: In the Azure Policy service, define a policy definition that enforces the "Deny Assignment" for the resources.
Attempting to configure what Azure Role definitions Ids (roles) are allowed to be assigned, via role assignments, utilizing Azure Policy. The below policies all create with out error, but Azure role assignments are still possible for all roles despite this policy being created / assigned.
An Azure RBAC deny assignments deny action is applied to artifact resources during assignment of a blueprint if the ... This step is done in REST API by adding up to five values to the excludedPrincipals array in the locks property when creating the assignment. The following assignment definition is an example of a request body that ...
"shaded.databricks.org.apache.hadoop.fs.azure.AzureException: hadoop_azure_shaded.com.microsoft.azure.storage.StorageException: Server failed to authenticate the request. Make sure the value of Authorization header is formed correctly including the signature." It appears the "Deny assignment" issue above is the cause? How can I resolve it.