Understanding Potential Risks for Human Subjects Research

As part of their ethical duty to participants, all researchers are required to properly identify, minimize, and disclose any potential harm or discomforts that may come to participants. These harms and discomforts are labeled as “ risks, ” and should be minimized, according to the beneficence principle of the Belmont Report . Any risks that may potentially befall participants must be disclosed in the informed consent , and participants should be given the choice of whether or not to participate in research.
Additional risks may also be encountered in light of a catastrophic event (e.g., a natural disaster, epidemic, terrorist attack, pandemic, etc.). During these times, researchers with active protocols must review their study activities to identify and mitigate any new risk. For example, prior to the COVID-19 pandemic and depending on the topic, TC IRB typically considered in-person surveys with adults competent to consent as low risk. Under COVID-19 circumstances, however, studies with in-person components are now reviewed as higher risk, as person-to-person exposure is the most frequent route of transmission for infectious viruses. The IRB is required to assess the level of risk involved in a research study when making a determination for review requirements. Some items factoring into the IRB’s risk assessment include possible risk to a subject’s psychological wellbeing, or the risk to a subject if their confidentiality is compromised. The more risk involved in a study, the higher the level of review and the more human subject protections required by the IRB.

Examples of Potential Risks & Suggestions for Mitigation
Reviewing potential risks to participants requires a knowledge of various types of harm or discomfort that participants may encounter. The Teachers College research community is largely composed of behavioral and social researchers. The following examples and suggestions for minimizing risks are likely to be encountered in behavioral science research, though they may also extend to biomedical and other types of research as well.
Loss of Time : Researchers are required to include the estimated time of each study activity and the total time of completion on the informed consent (parent permission or assent form). Researchers should:
- Estimate study completion time based on pilot tests.
- Consider the reading level of participants (e.g., 3rd grade readers vs. post-secondary students) when calculating the time necessary to complete the study.
- Reasonably overestimate times to account for participants that may take longer.
- Prepare for potential time delays when using online software (e.g., Zoom ) or introducing new activities.
Traumatic Events: Recalling traumatic or distressing events can be uncomfortable, and in some cases, harmful to an individual. Traumatic events are defined as events that are shocking, scary, or dangerous (e.g., natural disasters, acts of violence, accidents, etc.). While it is not always possible to identify what types of questions may trigger participants, researchers should identify and disclose questions or activities pertaining to traumatic events. Researchers should:
- Disclose any topics, study activities, or questions that may be triggering in the informed consent. For example, if the study includes questions about a traumatic event (e.g., 9/11), provide a trigger warning such as “The next section will include questions that may be uncomfortable to you. This study is voluntary. You can choose to stop the study at any time or skip any question.”
- Monitor the participant during each study activity and after, if possible. While the participant may appear fine during a study, recalling traumatic events may lead to flashbacks, insomnia, trouble concentrating, or higher levels of anxiety, sadness, or anger for a prolonged period of time.
- Provide participants with a list of community resources, or offer free counseling services (if appropriate), should the need arise.
- Consider options such as recruiting a trained professional to be available to help debrief the participants if they start to experience symptoms of distress.
Unwanted Stimuli: Exposure to unwanted or distressing stimuli during a study’s activities may bring harm and discomfort. Participants should not be exposed to distressing stimuli (e.g., pornography, smoking, suicide) without first providing their clear consent. Researchers should:
- Know the risks associated with exposing participants to unwanted stimuli (e.g., increased sadness or irritability), and implement additional safeguards throughout their study, such as debriefing participants after the study activities are finished.
- Refrain from exposing high-risk groups to unwanted stimuli. For example, study activities including heavy drinking or intoxication should screen out recovering substance users.
Labeling: Participants unfamiliar with clinical terminology may begin to identify with disorders or personalities outlined in study measures. For example, someone taking a scale labeled “Depression Scale” may begin to identify as having depression without receiving a clinical diagnosis. Researchers should:
- Reduce participant confusion by appropriately and clearly naming scales or removing measure names altogether.
- Examine tiles of studies for potential bias and risk to participants.
Environmental Stimuli: Environmental stimuli, such as the research location, building layout, lighting, or external noise, is not always considered in the research design. However, some stimuli may be triggering for participants, and should be eliminated, if possible. Researchers should:
- Examine their research space for any environmental allergens or health issues, such as dust and flickering lights, prior to inviting participants.
- Remain mindful of possible food allergies (e.g., nuts, shellfish, gluten) when serving snacks or refreshments.
- Ensure that the space is safe, secure, hygienic , and, if applicable, private.
- Review the CDC's detailed instructions on how to clean and disinfect workspaces, along with their list of EPA-approved disinfectants .
Minor Emotional Risk: Typical common, but minor, risks include mental fatigue, embarrassment, discomfort, or frustration. Researchers should:
- Review their study activities from the perspective of the participant in order to determine if these emotions might be encountered. For example, a 5-minute survey on personal food preferences is unlikely to cause frustration. However, a study activity in which participants must solve complex mathematical equations in front of peers may cause embarrassment or frustration.
- Always disclose any anticipated distressing emotions in the consent form.
Participant Relationships: Putting strain on participants’ relationships (e.g., causing a fight between a dating couple) will likely cause harm or discomfort to a participant. Researchers should:
- Disclose study activities in the consent form that may cause relationship distress.
- Distinguish between study activities that may cause relationship distress (e.g., this study will examine household spending habits between partners) from unintentional relationship distress perpetuated in error by the researcher. In the latter’s case, the researcher should gauge the situation and take steps to ensure respect, participant autonomy, and care.
Exercise & Repetitive Movements : Studies involving exercise or movement have an inherent risk of physical injury to the participants. Researchers should:
- Disclose all activities at the beginning of the study that may cause physical discomfort.
- Evaluate or discuss the participants’ physical health and ability based on the study activity (e.g., able to lift 20 pounds without assistance).
- Gauge the health of the participant to engage in the activities. For example, does the participant have any underlying health conditions that might impact their ability to participate? (e.g., a study requiring intense cardio exertion might want to screen for asthmatic participants).
- Disclose health risks on the consent form.
Personal Information: A sking questions about private information such as income, health habits, illegal substance use, etc. may be distressing for participants. Inclusion of these types of questions should be clearly justified to the IRB. Researchers should:
- Clarify confidentiality policies.
- Disclose what identifiers may be disclosed, or are at risk of disclosure (e.g., during focus group sessions, researchers cannot guarantee confidentiality).
- Review Certificates of Confidentiality (CoC) for human subjects, if applicable.
Viral Illnesses, Spreads, or Pandemics: With the COVID-19 pandemic, person-to-person contact is the most frequent route of viral transmission. Researchers with in-person components in their study must evaluate study activities for points of contact. Exposure is at its highest when people are within approximately 6 feet of one another, and in close contact for 15 minutes or more. Shared spaces, equipment, and surfaces (e.g., office keyboards, writing utensils, etc.) can also be contaminated. To reduce the risk of infection, researchers should:
- Wash hands with soap and water for 20 seconds. If soap and water are not available, use a hand sanitizer that contains at least 60% alcohol.
- Avoid touching one’s face.
- Use face coverings when around other people.
- Cover coughs and sneezes.
- Throw used tissues in the trash.
- Practice social distancing, if possible.
- Clean and disinfect high-touch surfaces daily. This may include tables, doorknobs, light switches, countertops, handles, desks, phones, keyboards, toilets, faucets, and sinks.
- Restrict in-person interactions to ventilated areas, or outside when possible.
- Remain vigilant about taking the steps that reduce exposure.
Requirements for Mitigating Research Risks
When assessing risk and benefits in a study, the IRB can support researchers in determining if a risk is justifiable or should be removed. Generally, risks to participants must be minimized, and any risks in the study should be reasonable when compared to the benefits of the study.
The IRB also requires that each individual participant provides their informed consent. All consent must be documented and available for review if requested. If a participant is unable to provide their consent (e.g., a minor), their guardian must provide consent, and the participant’s assent should be sought. If a participant is likely to be vulnerable to coercion (e.g., prisoners, cognitively impaired persons, etc.), additional safeguards must be outlined in the IRB application. Additionally, researchers must justify the rationale for conducting their study with vulnerable populations as opposed to general populations (e.g., the study provides an intervention which fills a need for that specific population). For sample consent and application language, please visit our TC IRB Submission Document Templates & Samples guide.
In the informed consent, the privacy and confidentiality of the participants must be appropriately documented. TC IRB recommends that all data be de-identified prior to the start of analysis. Finally, the research plan must make provisions for the secure collection and monitoring of data (visit our Data Sharing, Requests, & Encryption for more information). TC IRB has worked closely with TC Information Technologies (IT) to support researchers working remotely with limited resources and technological capabilities. TC IT should be consulted as the first point of contact if data cannot be secured to the standards outlined in the data security plan.
For COVID-19 related information, risks, and preparation please visit here.
Institutional Review Board
Address: Russell Hall, Room 13
* Phone: 212-678-4105 * Email: [email protected]
Appointments are available by request . Make sure to have your IRB protocol number (e.g., 19-011) available. If you are unable to access any of the downloadable resources, please contact OASID via email [email protected] .

Institutional Review Board Office of Research
Risks and Benefits of Research
The IRB is responsible for evaluating the potential risks and weighing the probability of the risk occurring and the magnitude of harm that may result. It must then judge whether the anticipated benefit, either of new knowledge or of improved health for the research subjects, justifies inviting any person to undertake the risks. The IRB cannot approve research in which the risks are judged unreasonable in relation to the anticipated benefits.
In This Section
What is the requirement.
- How Do I Comply With the Requirement?
Ethical Considerations
Risk guidance, benefits guidance, definitions.
45 CFR 46.111 (a) (1) Risks to subjects are minimized:
(i) By using procedures that are consistent with sound research design and that do not unnecessarily expose subjects to risk, and
(ii) Whenever appropriate, by using procedures already being performed on the subjects for diagnostic or treatment purposes.
(2) Risks to subjects are reasonable in relation to anticipated benefits, if any, to subjects, and the importance of the knowledge that may reasonably be expected to result. In evaluating risks and benefits, the IRB should consider only those risks and benefits that may result from the research (as distinguished from risks and benefits of therapies subjects would receive even if not participating in the research). The IRB should not consider possible long-range effects of applying knowledge gained in the research ( e.g., the possible effects of the research on public policy) as among those research risks that fall within the purview of its responsibility.
How do I Comply With the Requirement?
Initial review application.
You will be asked to select all procedures that will be conducted for research purposes as directed by the study protocol:
- Analysis of information or specimens collected for reasons other than this project (medical records, student records, research records collected for another study, analysis of left-over specimens, etc.)
- Non-invasive procedures to collect information or specimens (interviews, questionnaires, observation, vitals, oral swabs, urine collection, etc.)
- Collection of blood by finger stick, heel stick, ear stick, or venipuncture
- Use of xrays or microwaves
- With the exception of collection of blood by finger stick, heel stick, ear stick, or venipuncture, collection of information or specimens when the collection requires penetration of tissue (tissue biopsy, implantation of a device, etc.)
- Use of medical drugs or devices in a manner already approved by the FDA
- Use of medical drugs or devices in a manner not approved by the FDA
Your selection will assist in routing the application for the appropriate level of review.
Research Protocol
Describe the known risks related to participation in research. Describe any actions taken to minimize risk. Clearly state which procedures are being done specifically for research purposes and which are done as standard of care or normal practice.
Describe any anticipated benefits the research subjects may receive from participation in the research. For minimal risk research, there is no requirement of direct benefit to research subjects; it is acceptable to state that there is no anticipated benefit to subjects. When research is greater than minimal risk, the anticipated benefits must justify the known risks. Please note that compensation for participation in research may not be listed as a benefit.
Consent Documents
Describe the known risks and anticipated benefits in laypersons terms. List all risks and benefits that are described in the research protocol.
When making this determination in research with adult populations, the IRB weighs the risks to participants against the anticipated benefits (either direct or indirect) of the research. When vulnerable subjects take part, the regulations place limits on the extent of risk permitted. Children may only participate in greater than minimal risk research when there is a prospect for direct benefit. The IRB will:
- Identify and compare the risks associated with the research from the risks of therapies or alternatives to participation in research.
- Determine that the risks will be minimized.
- Identify the anticipated benefits to be derived from the research.
- Determine that the risks are reasonable in relation to be benefits to subjects, if any, and the importance of the knowledge to be gained.
- Verify research participants will be provided with an accurate and fair description (during the consent process) of the risks and/or the anticipated benefits.
In human subject research, research is categorized into in two categories:
- Minimal risk; or
- Greater than minimal risk
Research is considered minimal risk when the risks of the research are not greater than those experienced in regular daily life. Researchers are responsible for identifying any possible risks of the research and minimizing risks to subjects whenever possible. Some common types of risks are:
- Economic risks : Payment by subjects for procedures not otherwise required, loss of wages or other income and any other financial costs, such as damage to a subject’s employability, as a consequence of participation in the research.
- Loss of Confidentiality : In all research involving human subjects, confidentiality of identifiable information is presumed and must be maintained unless the investigator obtains the express permission of the subject to do otherwise. Subjects have the right to be protected against injury or illegal invasions of their privacy and to preservation of their personal dignity. The more sensitive the research material, the greater the care that must be exercised in obtaining, handling, and storing data. In order to minimize the risk for loss of confidentiality, investigators should only collect personal information that is absolutely essential to the research activity. If personal data must be collected, it should be coded as early in the activity as possible and securely stored so that only the investigator and authorized staff may access it. Identities of individual subjects must never be released without the express consent of the subject. In addition, if an investigator wishes to use data for a purpose other than the one for which it was originally collected and the data are still identifiable (e.g. a code list for the data still exists), the investigator may need to obtain consent from the subjects for the new use of the data.
- Legal risks : Legal risks exist when the research methods are such that the subject or others will be liable for a violation of the law, either by revealing that the subject or others have or will engage in conduct for which the subject or others may be criminally or civilly liable, or by requiring activities for which the subject or others may be criminally or civilly liable.
- Physical risks : Physical risks include physical discomfort, pain, injury, illness or disease brought about by the methods and procedures of the research. A physical risk may result from the involvement of physical stimuli such as noise, electric shock, heat, cold, electric magnetic or gravitational fields, etc. Engaging a subject in a social situation which could involve violence may also create a physical risk.
- Psychological risks : The potential for negative affective states such as anxiety, depression, guilt, shock and loss of self-esteem and altered behavior. Sensory deprivation, sleep deprivation, use of hypnosis, deception or mental stresses are examples of psychological risks.
- Social risks : The potential for alterations in relationships with others that are to the disadvantage of the subject, including embarrassment, loss of respect of others, labeling a subject in a way that will have negative consequences, or in some way diminishing those opportunities and powers a person has by virtue of relationships with others.
Strategies for Minimizing Risks
Eliminating risks.
Risks are eliminated by limiting research procedures or data collection to those that are necessary for the research. Some examples:
- Recording data without identifiers.
- Collecting the minimum data necessary for the research.
- Performing only procedures that are necessary to achieve the study objectives.
- Collecting the fewest specimens with the least volume necessary.
When risks cannot be eliminated, there are often opportunities to decrease the risk to research subjects. Some examples:
- Use of existing records or specimens.
- Use of a blood-drawing IV instead of separate venipunctures for a PK study.
- Obtaining a certificate of Confidentiality to minimize the likely of forced disclosure of sensitive materials.
- Coding data and samples to conceal identifiers.
- Using REDCap to secure data that includes PHI .
- Limiting access to research data.
Combining research procedures with clinical care
If procedures can be timed to take place at the same time as a clinically indicated procedure or if clinical test results can be used instead of repeating the measurements, the risks are often greatly reduced. Some examples:
- Timing research blood draws, X-rays or other procedures to occur at the same time as clinical procedures.
- Limiting research MRI, PET, CT or other scans, to those having a clinically indicated study, particularly when sedation or general anesthesia is required.
Nancy King has defined three types of benefit that may occur in the context of clinical research ( J Law Med Ethics. 2000 Winter;28(4):332-43 )
Direct Benefit: A benefit arising from receiving the intervention being studied.
Indirect Benefits
- Collateral Benefit is a benefit arising from being a subject, even if one does not receive the experimental intervention (for example, a free physical exam and testing, free medical care and other extras, or the personal gratification of altruism).
- Aspirational Benefit is a benefit to society and or future patients, which arises from the results of the study.
Research with a direct benefit
Any study that involves an intervention could have an anticipated direct benefit. In these studies, participants may receive some intervention (medical, behavioral, or other), that they would not otherwise receive. The purpose of the research is typically to test the effectiveness of the intervention. When describing the anticipated benefits of research in the consent document, it is important that researchers make subjects aware that the benefits of the intervention are not known, and that the research is being conducted to evaluate the effectiveness of the intervention. Whenever possible, the researcher should provide any known information about the probability and magnitude of the anticipated benefit.
Research with an indirect benefit
When research does not involve an intervention there is little opportunity for direct benefit. When the risks of the research are no greater than those encountered in the everyday life, there is no requirement for direct benefit. When the research risks are greater than minimal risk, then the researcher must provide justification that explains how the anticipated benefits of the research justify the risks to the subjects.
- Benefit is a valued or desired outcome; an advantage.
- Minimal Risk means the probability and magnitude of harm or discomfort anticipated in the research are not greater, in and of themselves, than those ordinarily encountered in daily life or during the performance of routine physical or psychological examinations or tests.
- Glossary of Lay Terminology
- Consent Form Sample Pregnancy Risk Language
- Consent Form Sample Risk Language
IRB Quick Links

Office of Research
- IRB-SBS Home
- Contact IRB-SBS
- IRB SBS Staff Directory
- IRB SBS Board Members
- About the IRB-SBS
- CITI Training
- Education Events
- Virginia IRB Consortium
- IRB-SBS Learning Shots
- HRPP Education & Training
- Student Support
- Access iProtocol
- Getting Started
- iProtocol Question Guide
- iProtocol Management
- Protocol Review Process
- Certificate of Confidentiality
- Deception and/or Withholding Information from a Participant
- Ethnographic Research
- IRB-SBS 101
- IRB-SBS Glossary
- Participant Pools
- Paying Participants
- Research in an Educational Setting
- Research in an International Setting and/or Location
- Risk-Sensitive Populations
- Student Researchers and Faculty Sponsors
- Study Funding and the IRB
Understanding Risk in Research
- Vulnerable Participants
- IRB-SBS PAM & Ed
- Federal Regulations
- Ethical Principals
- Partner Offices
- Determining Human Subjects Research
- Determining HSR or SBS

Assessing risk in a research study is one of the primary responsibilities of an IRB and one of its most controversial tasks. By nature, studying human beings is a complicated process because the subject matter itself is complicated. The level of risk can vary because of many factors including: the population included in the study, the situations encountered by the participants, and/ or the experience of the researcher or team. Two studies may appear similar but a few factors could make one inherently more risky than the other.
This section describes what a researcher needs to consider when developing a protocol as well as the risk analysis conducted by an IRB board member. This section does not cover ever scenario nor is it meant to be all inclusive; if you have a specific question about the risks in your study, please contact our office for further guidance.
Section Topics
The Essex website uses cookies. By continuing to browse the site you are consenting to their use. Please visit our cookie policy to find out which cookies we use and why. View cookie policy.
Research risk assessment
It's the responsibility of the principal investigators (PI) and researchers to identify reasonably foreseeable risks associated with their research and control the risks so far as is reasonably practicable.
All participants and research assistants have the right to expect protection from physical, psychological, social, legal and economic harm at all times during an investigation. Certain research may also present reputational, legal and / or economic risks to the University.
As part of the ethical approval process for research involving human participants you are required to identify potential risks associated with your research and the action you will take to mitigate risk. You may be asked to submit your risk assessment.
The risk assessment process is a careful examination of what could cause harm, who/what could be harmed and how. It will help you to determine what risk control measures are needed and whether you are doing enough.
Risk assessment responsibility
The PI and researchers need to take responsibility for all assessments associated with their projects. Occasionally you may need research workers or students to risk assess an aspect of the work and you will need to check the assessments are adequate and sign them off.
Risk assessors need to be competent and you’ll need to ensure they have adequate training and resource to do the assessments. There is risk assessment training available and help and advice help and advice help and advice from your Health and Safety adviser and safety specialists (for health and safety risks), or the REO Research Governance team for other risks. In some cases, the hazards are so unique to the research that the PI and their team might be the only people who know the work well enough to make valid judgements about the risk and justify their conclusions.
Risk assessment process
The risk assessment process is a careful examination of what could cause harm, who/what could be harmed and how. It will help you to determine what risk control measures are needed and whether you are doing enough.
To simplify the process you can use the health and safety risk assessment templates, risk estimation tool and guidance for all risks associated with your research project. Please refer to the research risk estimation guidance under how to carry out a risk assessment below to assist you.
Research risks
Typical risks that need to be considered as part of research ethics are:
- Social risks: disclosures that could affect participants standing in the community, in their family, and their job.
- Legal risks: activities that could result in the participant, researchers and / or University committing an offence; activities that might lead to a participant disclosing criminal activity to a researcher which would necessitate reporting to enforcement authorities; activities that could result in a civil claim for compensation.
- Economic harm: financial harm to participant, researcher and / or University through disclosure or other event.
- Reputational risk: damage to public perception of University or the University/researchers’ reputation in the eyes of funders, the research community and / or the general public.
- Safeguarding risks: Risk to young people, vulnerable adults and / or researcher from improper behaviour, abuse or exploitation. Risk to researcher of being in a comprising situation, in which there might be accusations of improper behaviour.
- Health and safety risks: risks of harm to health, physical injury or psychological harm to participants or the researcher. Further information on health and safety risks is given below.
Health and safety risks
The potential hazards and risks in research can be many and varied. You will need to be competent and familiar with the work or know where to obtain expert advice to ensure you have identified reasonably foreseeable risks. Here are some common research hazards and risks:
- Location hazards Location hazards Location hazards and risks are associated with where the research is carried out. For example: fire; visiting or working in participant’s homes; working in remote locations and in high crime areas; overseas travel; hot, cold or extreme weather conditions; working on or by water. Also hazardous work locations, such as construction sites, confined spaces, roofs or laboratories. For overseas travel, you will need to check country / city specific information, travel health requirements and consider emergency arrangements as part of your research planning, by following the University’s overseas travel health and safety standard .
- Activity hazards Activity hazards Activity hazards and risks associated with the tasks carried out. For example: potentially mentally harmful activities; distressing and stressful work and content; driving; tripping, or slipping; falling from height; physically demanding work; lifting, carrying, pushing and pulling loads; night time and weekend working.
- Machinery and equipment Machinery and equipment Machinery and equipment . For example: ergonomic hazards, including computer workstations and equipment; contact with electricity; contact with moving, rotating, ejecting or cutting parts in machinery and instruments; accidental release of energy from machines and instruments.
- Chemicals and other hazardous substances . The use, production, storage, waste, transportation and accidental release of chemicals and hazardous substances; flammable, dangerous and explosive substances; asphyxiating gases; allergens; biological agents, blood and blood products. You’ll need to gather information about the amount, frequency and duration of exposure and carry out a COSHH or DSEAR assessment which will inform whether you may need health surveillance for yourself and / or your research participants.
- Physical agents Physical agents Physical agents . For example: excessive noise exposure, hand-arm vibration and whole body vibration; ionising radiation; lasers; artificial optical radiation and electromagnetic fields. You’ll need to gather information about the amount, frequency and duration of exposure inform whether you may need health surveillance for yourself and / or your research participants.
When to carry out a risk assessment
Carrying out initial risk assessments as part of the planning process will help you identify whether existing resources and facilities are adequate to ensure risk control, or if the project needs to be altered accordingly. It will also help you to identify potential costs that need to be considered as part of the funding bid.
Once the project is approved, research specific risk assessments need to be carried out before work starts.
The research may need ethical approval if there is significant risk to participants, researchers or the University.
How to carry out a risk assessment
The University standard on risk assessments provides guidance, tips on getting it right, as well as resources and the forms to help you produce suitable and sufficient risk assessments and must be used.
- Risk assessment template (.dotx)
- Flow chart to research risk assessment (.pdf)
- Research risk assessment: Risk estimation tool (.pdf)
- Example of a Social Science research risk assessment (.pdf)
Refer to carrying out a risk assessment carrying out a risk assessment carrying out a risk assessment for step by step guidance.
Risk assessments must relate to the actual work and must be monitored by the PI. If there are significant changes to the activities, locations, equipment or substances used, the risk assessment will need to reviewed, updated and the old version archived. Risk assessments should also consider the end of projects, arrangements for waste disposal, equipment, controlled area decommission and emergencies.
Things to consider:
- The risks may be specialist in nature or general. Information can found from legislation, sector guidance, safety data sheets, manufacturers equipment information, research documents, forums and health and safety professionals.
- Practical research might involve less well-known hazards. Do you or your team have the expertise to assess the risk adequately? Do you know who to go to for expert advice?
- The capabilities, training, knowledge, skills and experience of the project team members. Are they competent or are there gaps?
- In fast changing research environments, is there a need to carry out dynamic risk assessments? Are they understood and recorded?
- The right personal protective equipment for the hazards identified and training in how to use it.
- Specific Occupational Health vaccinations, health surveillance and screening requirements identified and undertaken. With physical agents and substances you’ll need to make an informed decision about the amount, frequency and duration of exposure. If you need help with this contact Health and Safety.
- Associated activities: storage, transport/travel, cleaning, maintenance, foreseeable emergencies (eg spillages), decommissioning and disposal.
- The safe design, testing and maintenance of the facilities and equipment.
- Planned and preventative maintenance of general plant and specialist equipment.
These risk assessments relate to the actual work and must be monitored by the PI. If there are significant changes to the activities, locations, equipment or substances used, the risk assessment will need to reviewed, updated and the old version archived. Risk assessments should also consider the end of projects, arrangements for waste disposal, equipment and controlled area decommission and emergencies.
Training
If you would like training on completing a risk assessment, please book onto our Risk Assessment Essentials course via HR Organiser. If you are unable to access this, please email [email protected]
- Carrying out a risk assessment Carrying out a risk assessment Carrying out a risk assessment
- People especially at risk People especially at risk People especially at risk
- IOSH/USHA/UCEA guidance on managing health and safety in research (.pdf)
- Research governance: Ethical approval

- For enquiries contact your Student Services Hub
- University of Essex
- Wivenhoe Park
- Colchester CO4 3SQ
- Accessibility
- Privacy and Cookie Policy
Our systems are now restored following recent technical disruption, and we’re working hard to catch up on publishing. We apologise for the inconvenience caused. Find out more: https://www.cambridge.org/universitypress/about-us/news-and-blogs/cambridge-university-press-publishing-update-following-technical-disruption
We use cookies to distinguish you from other users and to provide you with a better experience on our websites. Close this message to accept cookies or find out how to manage your cookie settings .
Login Alert

- > Manual for Research Ethics Committees
- > Risk assessment for research participants

Book contents
- Frontmatter
- Editorial board
- Acknowledgements
- List of contributors
- Introduction
- 1 The ethics of clinical research
- 2 Research ethics committees and the law
- 3 The regulation of medical research: a historical overview
- 4 The regulation of medical research in the UK
- 5 Observational and epidemiological research
- 6 Social survey research
- 7 Approaching qualitative research
- 8 Complementary and alternative medicine: challenges for research ethics committees
- 9 The ethical review of student research in the context of the governance arrangements for research ethics committees
- 10 The ethics of genetic research
- 11 Research or audit?
- 12 Randomised controlled trials
- 13 Determining the study size
- 14 Risk assessment for research participants
- 15 Absorbed radiation in patient and volunteer studies submitted to the ethical committee: a memorandum
- 16 A guide to the use of radioactive materials and radiological procedures for research purposes
- 17 Indemnity in medical research
- 18 The prevention and management of fraud and misconduct: the role of the LREC
- 19 Understanding clinical trials: a model for providing information to potential participants
- 20 The law relating to consent
- 21 Writing information for potential research participants
- 22 The law relating to confidentiality
- 23 Research involving vulnerable participants: some ethical issues
- 24 The ethics of research related to healthcare in developing countries
14 - Risk assessment for research participants
Published online by Cambridge University Press: 08 January 2010
This chapter tries to provide a way by which research participants can assess the risks of being involved in a particular research project. At the heart of the process will be the balance and a judgement made by the individual between the perceived benefits of the research and the possible risks.
Uncertainty is a key word in the assessment of risk. It should also be noted that any potential benefits may not be for the person taking part in the research, but for subsequent patients and/or populations. By definition, carrying out research means that the outcome is not known and thus potential benefits and risks not known. If they were clear, the procedure, treatment, intervention, would be classified as good practice, not research, as the risks would have been already assessed. It is thus difficult to assess the risks of taking part in a research project as much is unknown. This section can only give an indication of the terms and language used and the kinds of issues which might be considered by people before taking part in a research project.
Some definitions
Before considering some of the possible categories of risk, it is worth being clear about what certain terms mean.
(a) A hazard is any set of circumstances that may have harmful consequences.
(b) The risk is the probability of the hazard causing an adverse effect.
Thus a hazard, such as a drug, is not a risk until it is administered. The risk, the probability of an adverse effect occurring, will depend on various factors including the nature of the drug itself, the dose, the condition of the patient, and many others.
Access options
Save book to kindle.
To save this book to your Kindle, first ensure [email protected] is added to your Approved Personal Document E-mail List under your Personal Document Settings on the Manage Your Content and Devices page of your Amazon account. Then enter the ‘name’ part of your Kindle email address below. Find out more about saving to your Kindle .
Note you can select to save to either the @free.kindle.com or @kindle.com variations. ‘@free.kindle.com’ emails are free but can only be saved to your device when it is connected to wi-fi. ‘@kindle.com’ emails can be delivered even when you are not connected to wi-fi, but note that service fees apply.
Find out more about the Kindle Personal Document Service .
- Risk assessment for research participants
- By Kenneth Calman
- Edited by Sue Eckstein , King's College London
- Book: Manual for Research Ethics Committees
- Online publication: 08 January 2010
- Chapter DOI: https://doi.org/10.1017/CBO9780511550089.016
Save book to Dropbox
To save content items to your account, please confirm that you agree to abide by our usage policies. If this is the first time you use this feature, you will be asked to authorise Cambridge Core to connect with your account. Find out more about saving content to Dropbox .
Save book to Google Drive
To save content items to your account, please confirm that you agree to abide by our usage policies. If this is the first time you use this feature, you will be asked to authorise Cambridge Core to connect with your account. Find out more about saving content to Google Drive .

Assessing Risks and Benefits
The IRB is responsible for evaluating the potential risks and weighing the probability of the risk occurring and the magnitude of harm that may result. It must then judge whether the anticipated benefit, either of new knowledge or of improved health for the research subjects, justifies inviting any person to undertake the risks.
Per DHHS and FDA regulations ( 45 CFR 46.111 and 21 CFR 56.111 ) two of the required criteria for granting IRB approval of research are:
- Risks to subjects are minimized by using procedures which are consistent with sound research design and which do not unnecessarily expose subjects to risk, and whenever appropriate, by using procedures already being performed on the subjects for diagnostic or treatment purposes.
- Risks to subjects are reasonable in relation to anticipated benefits, if any, to subjects, and the importance of the knowledge that may reasonably be expected to result. In evaluating risks and benefits, the IRB Committee will consider only those risks and benefits that may result from the research, as distinguished from risks and benefits of therapies subjects would receive even if not participating in the research.
- Benefit A valued or desired outcome; an advantage.
- Risk The probability of harm or injury (physical, psychological, social, or economic) occurring as a result of participation in a research study. Both the probability and magnitude of possible harm may vary from minimal to significant. Federal regulations define only "minimal risk."
- Minimal Risk A risk is minimal where the probability and magnitude of harm or discomfort anticipated in the proposed research are not greater, in and of themselves, than those ordinarily encountered in daily lives of the general population or during the performance of routine physical or psychological examinations or tests.
- Minimal Risk for Research involving Prisoners The definition of minimal risk for research involving prisoners differs somewhat from that given for non-institutionalized adults. Minimal risk is in this case is defined as, "the probability and magnitude of physical or psychological harm that is normally encountered in the daily lives, or in the routine medical, dental or psychological examinations of healthy persons."
There are two sources of confusion in the assessment of risks and benefits. One arises from the language employed in the discussion:
- "Risk" is a word expressing probabilities;
- "Benefits" is a word expressing a fact or state of affairs.
It is more accurate to speak as if both were in the realm of probability: i.e., risks and expected or anticipated benefits. Confusion also may arise because "risks" can refer to two quite different things:
- those chances that specific individuals are willing to undertake for some desired goal; or
- the conditions that make a situation harmful to a subject.
Researchers should provide detailed information in the IRB application about potential risks and benefits associated with the research, and provide information about the probability, magnitude and potential harms associated with each risk.
The IRB cannot approve research in which the risks are judged unreasonable in relation to the anticipated benefits. The IRB must:
- As applicable, evaluate the available clinical and nonclinical information on an investigational product to determine if the data is adequate to support the proposed clinical trial;
- Determine that the risks will be minimized to the extent possible [see below];
- Identify the probable benefits to be derived from the research;
- Determine that the risks are reasonable in relation to be benefits to subjects , if any, and the importance of the knowledge to be gained; and
- Assure that potential subjects will be provided with an accurate and fair description (during consent) of the risks or discomforts and the anticipated benefits.
The risks to which research subjects may be exposed have been classified as physical, psychological, social, and economic .
- Physical Harms Medical research often involves exposure to minor pain, discomfort, or injury from invasive medical procedures, or harm from possible side effects of drugs. All of these should be considered "risks" for purposes of IRB review. Some of the adverse effects that result from medical procedures or drugs can be permanent, but most are transient. Procedures commonly used in medical research usually result in no more than minor discomfort (e.g., temporary dizziness, the pain associated with venipuncture).Some medical research is designed only to measure more carefully the effects of therapeutic or diagnostic procedures applied in the course of caring for an illness. Such research may not entail any significant risks beyond those presented by medically indicated interventions. On the other hand, research designed to evaluate new drugs or procedures may present more than minimal risk, and, on occasion, can cause serious or disabling injuries.
- Psychological Harms Participation in research may result in undesired changes in thought processes and emotion (e.g., episodes of depression, confusion, or hallucination resulting from drugs, feelings of stress, guilt, and loss of self-esteem). These changes may be transitory, recurrent, or permanent. Most psychological risks are minimal or transitory, but some research has the potential for causing serious psychological harm.Stress and feelings of guilt or embarrassment may arise simply from thinking or talking about one's own behavior or attitudes on sensitive topics such as drug use, sexual preferences, selfishness, and violence. These feelings may be aroused when the subject is being interviewed or filling out a questionnaire. Stress may also be induced when the researchers manipulate the subjects' environment - as when "emergencies" or fake "assaults" are staged to observe how passersby respond. More frequently, however, is the possibility of psychological harm when behavioral research involves an element of deception.
- Is the invasion of privacy involved acceptable in light of the subjects' reasonable expectations of privacy in the situation under study;
- Is the research question of sufficient importance to justify the intrusion?
- The IRB must also consider whether the research design could be modified so that the study can be conducted without invading the privacy of the subjects.
- Note: Breach of confidentiality is sometimes confused with invasion of privacy, but it is really a different risk. Invasion of privacy concerns access to a person's body or behavior without consent; confidentiality of data concerns safeguarding information that has been given voluntarily by one person to another.
- Some research requires the use of a subject's hospital, school, or employment records. Access to such records for legitimate research purposes is generally acceptable, as long as the researcher protects the confidentiality of that information. However, it is important to recognize that a breach of confidentiality may result in psychological harm to individuals (in the form of embarrassment, guilt, stress, and so forth) or in social harm (see below).
- Social and Economic Harms Some invasions of privacy and breaches of confidentiality may result in embarrassment within one's business or social group, loss of employment, or criminal prosecution. Areas of particular sensitivity are information regarding alcohol or drug abuse, mental illness, illegal activities, and sexual behavior. Some social and behavioral research may yield information about individuals that could "label" or "stigmatize" the subjects. (e.g., as actual or potential delinquents or schizophrenics). Confidentiality safeguards must be strong in these instances. Participation in research may result in additional actual costs to individuals. Any anticipated costs to research participants should be described to prospective subjects during the consent process.
- Provide complete information in the protocol regarding the experimental design and the scientific rationale underlying the proposed research, including the results of previous animal and human studies.
- Assemble a research team with sufficient expertise and experience to conduct the research.
- Ensure that the projected sample size is sufficient to yield useful results.
- Collect data from standard-of-care procedures to avoid unnecessary risk, particularly for invasive or risky procedures (e.g., spinal taps, cardiac catheterization).
- Incorporate adequate safeguards into the research design such as an appropriate data safety monitoring plan, the presence of trained personnel who can respond to emergencies, and procedures to protect the confidentiality of the data (e.g., encryption, codes, and passwords).
351. Research Risks
Updated June 7, 2024
Research Risk Defined
Federal regulations at 45 CFR 46.102 item (j), define minimal risk as "... the probability and magnitude of harm or discomfort anticipated in the research are not greater in and of themselves than those ordinarily encountered in daily life or during the performance of routine physical or psychological examinations or tests." For example, the risk of drawing a small amount of blood from a healthy individual for research purposes is no greater than the risk of doing so as part of routine physical examination. Risks to participants should be reasonable in relation to potential benefits, if any, to participants, and the importance of the knowledge that may reasonably be expected to result. Risks to participants should be minimized by using procedures that are consistent with sound research design and do not unnecessarily expose participants to risk.
Determinations of greater than minimal risk are deduced from the definition for minimal risk.
Research risk can refer to:
- The chances that individuals are willing to undertake for some desired goal; or
- Conditions that make a situation dangerous per se .
The IRB must evaluate risk. The IRB should consider whether the anticipated benefit, either of new knowledge or of improved health for participants, justifies inviting any person to undertake the risks. The IRB should not approve research if risks are unreasonable in relation to anticipated benefits. IRB reviewers should be diligent to focus only on the risks associated with the protocol that are directly related to the research. Risks associated with the standard of care procedures that may provide the framework for the research should not factor into the risk classification. In evaluating risks and benefits, the IRB should consider only those risks and benefits that may result from the research.
Effect of Risk Magnitude and Probability on Level of Risk
Once the risks associated with the research have been identified, the process of categorizing the risks as minimal or greater than minimal may begin. Two characteristics influence the nature of the risk: 1) the probability of harm; 2) the magnitude of harm. The magnitude of harm can be related to the severity, duration and reversibility of a potential harm. The IRB reviewer should consider both the likelihood and magnitude of harm and whether they are greater than those encountered in daily life or during routine physical or psychological examinations.
In determining if research risk is minimal or greater than minimal, Principal Investigators (PIs) and the IRB must consider both the magnitude and probability of harm that may result from a risk. For example:
- Research that involves risk that is high in both magnitude and probability of harm likely constitutes greater than minimal risk.
- Research that involves risk that is neither high in magnitude nor probability of harm likely is minimal risk.
The degree of magnitude/probability, what the magnitude/probability may mean to participants, and type of risk bear consideration require more careful assessment. For example:
- Research that involves risk with a high magnitude and low probability of harm may be considered greater than minimal risk due to high magnitude or minimal risk due to low probability. Consider level of risk for research with a risk probability of 1 in 10,000 participants, when risk is blindness compared to when risk is severe stomach pain.
- Research that involves risk with a low in magnitude and high in probability of harm may be considered minimal risk due to the low magnitude or greater than minimal risk due to high probability. Consider level of risk for research with a probability that 1 in 10,000 compared to 1 in 5 participants will experience minor anxiety.
Regulatory Requirements for Research Risk
The federal regulations for IRB criteria for approval of research include two requirements related to research risk:
At §46.111 item (a)(1), the regulations specify risks must be minimized and that research should not unnecessarily expose participants to risk. Suggestions for minimizing risk include using:
- Sound research design and
- Procedures already being performed on participants for other purposes (when appropriate).
At §46.111 (a)(2), the regulations specify risks must be reasonable in relation to anticipated benefits to participants (if any) and to the importance of the knowledge that may be reasonably expected to result. In this regard, the regulations clarify that the IRB must consider:
- Only those risks and benefits that may result from the research and not risks/benefits that may result from care or treatment participants would receive if not participating in the research; and
- Possible long-range effects of applying the knowledge gained (e.g., effects of the research results on public policy).
Some of the basic and additional requirements for informed consent specify requirements for disclosure of risk to participants. The regulations at §46.116 require investigators to:
- Disclose reasonably foreseeable risks or discomforts to prospective participants before involving them in the research, under item (b)(2);
- For greater than minimal risk research, describe compensation or treatment when these will be available if injury occurs and whom to contact, or informing participants that no such compensation/treatment will be available, under item (b)(6); and
- When appropriate, state that a particular treatment or procedure may involve risks to the participant (or to the embryo or fetus, if the participant is or may become pregnant) which are currently unforeseeable, under item (c)(1).
The regulations also require additional safeguards for research involving vulnerable populations. For more information, see IRB policy for pregnant women/fetuses; prisoners; children; adults with impaired decision-making capacity; and persons who may be economically or educationally disadvantaged.
Identification and Assessment of Research Risk
In identifying risks, investigators and the IRB should consider only those risks that may be reasonably expected to occur as the result of the research . The IRB reviewer then assesses whether the risk to participants is reasonable in relation to the anticipated benefits to participants, if any, and the importance of the knowledge that may reasonably be expected to result. The IRB should not base risk determinations on risks associated with therapies or procedures participants would experience even if not participating in the research. However, participants should be informed of risks associated with procedures provided during or associated with the research, even if provided as standard-of-care.
To identify risks, it may be useful to consider categories of risks. The following is not meant to be definitive. It simply provides a framework for assessing risk.
(See IRB policy for risks related to participant privacy or data confidentiality.)
Harms from Research Design
- In designs involving random assignment, participants may not be assigned to the group that receives the more efficacious treatment.
- Participants assigned to the group receiving placebo may be at risk because their usual treatment may have been suspended during research participation, and they are not receiving an (albeit experimental) alternative).
- Participants in double-masked studies (i.e., neither participants nor researchers know group assignment) take the risk that information necessary for their care may not be readily available when needed.
- Lack of resources necessary to protect research participants. Such resources include staffing and personnel, in terms of availability, number, expertise, and experience; psychological, social, or medical services, including counseling or social support services that may be required because of research participation; psychological, social, or medical monitoring, ancillary care, equipment needed to protect participants, and resources for participant communication, such as language translation services.
Harms from Lack of Resources Necessary to Protect Research Participants
- Such resources include staffing and personnel, in terms of availability, number, expertise, and experience; psychological, social, or medical services, including counseling or social support services that may be required because of research participation; psychological, social, or medical monitoring, ancillary care, equipment needed to protect participants, and resources for participant communication, such as language translation services.
Physical Harms
More common to medical or biological research than to social, behavioral, or educational research, physical harms include exposure to
- Pain, discomfort, or injury from invasive medical procedures or device research;
- Dizziness or fainting; or
- Harm from side effects of drugs or devices.
Physical discomforts associated with prolonged fasting for a research procedure must also be considered.
When assessing physical harms, the IRB must determine if the research risks are greater than those associated with medically indicated interventions. Research designed to evaluate new drugs or procedures may present more than minimal risk and may include unforeseen risks to participants or fetuses in pregnant women, or mutagenic effects.
Psychological Harms
Psychological harms may result from undesirable changes in thoughts and emotions ( e.g ., depression, confusion, anxiety, guilt, or loss of self-esteem). These changes may be transitory, recurrent, or permanent. The duration affects the magnitude of harm.
Stress and feelings of guilt or embarrassment may arise from thinking or talking about one's own behavior or attitudes on sensitive topics such as drug use, sexual preferences, selfishness, and violence. Researchers may manipulate participants' environments to induce stress.
IRBs must also consider the possibility of psychological harm when behavioral research involves deception, particularly if the deception includes false feedback to participants about their own performance. When incomplete disclosure or deception is used, debriefing participants after their participation may minimize risk of psychological harm.
Social and Economic Harms
Some research may result in embarrassment within one's business or social group, loss of employment, or criminal prosecution. Research may yield information that could "label" or "stigmatize" participants. Areas of sensitivity include research involving alcohol and drug abuse, mental illness, illegal activities, and sexual behavior.
Researchers and the IRB must be acutely aware of negative repercussions that may result from breaches of privacy or confidentiality related to participation in a specific research study. Plans for follow-up contact in such studies requires special precautions to minimize unauthorized disclosure.
Minimizing Risks
As noted previously, federal regulations require that risks are minimized (i.e., reduced or managed).
Investigators and the IRB must determine that, to the degree possible, precautions, safeguards, and alternatives have been incorporated into the research activity to:
- Limit the severity or duration of harms (i.e., magnitude of harm) and
- Reduce the likelihood harms will occur (i.e., probability of harm).
Risks may be minimized by ensuring PIs possess the requisite competence in the area being studied and have the resources necessary to safely conduct the research.
To evaluate whether other, less risky methods might yield the desirable results, IRBs assess information about the scientific rationale and experimental design underlying the proposed research and the statistical basis for the investigation.
IRBs compare effects of the experimental treatment or of receiving no treatment at all to effects of treatments that might be administered in ordinary practice.
IRBs consider whether harmful effects can be adequately detected, prevented, or treated; and whether the risks and complications of underlying diseases may be unnecessarily exacerbated by the research.
IRBs must evaluate whether the research design will yield useful data. When the sample size is too small to yield valid conclusions or a hypothesis is imprecisely formulated, participants may be exposed to risk without sufficient justification.
Investigators must be cognizant of potential conflicts that may result from serving dual roles. For example, an investigator's eagerness for a participant to continue in a research project to amass more data may conflict with their responsibility as the treating physician to discontinue a therapy that is not helpful or may be harmful. (See IRB policy for inherently influential recruitment situations for more information and examples about conflicting researcher roles.)
Risk is minimized by incorporating adequate safeguards into research design wherever possible. Safeguards may include:
- Obtaining data from procedures performed for diagnosis or treatment instead of performing separate tests/procedures for the research;
- Excluding individuals or population groups when a specific characteristic may make participants more vulnerable to risks of a drug or procedure;
- Routinely monitoring data for patterns or problems, or to ensure a trial doesn't continue after reliable results have been obtained;
- Ensuring trained personnel are present to respond to emergencies;
- Including a mechanism to inform participants or others about an individual's involvement and treatment in a study involving single or double-blinding (e.g., giving participants a card or bracelet identifying someone who is available to break the code when necessary); and
- Coding data to protect confidentiality.
- An explanation as to whether any medical treatments are available if injury occurs. If medical treatments are available if injury occurs, what they consist of, or where further information may be obtained.
- An explanation of the consequences of a participant’s decision to withdraw from the research.
- A statement that the treatment or procedure may involve risks to the participant which are currently unforeseeable.

Home / Resources / ISACA Journal / Issues / 2021 / Volume 2 / Risk Assessment and Analysis Methods
Risk assessment and analysis methods: qualitative and quantitative.

A risk assessment determines the likelihood, consequences and tolerances of possible incidents. “Risk assessment is an inherent part of a broader risk management strategy to introduce control measures to eliminate or reduce any potential risk- related consequences.” 1 The main purpose of risk assessment is to avoid negative consequences related to risk or to evaluate possible opportunities.
It is the combined effort of:
- “…[I]dentifying and analyzing possible future events that could adversely affect individuals, assets, processes and/or the environment (i.e.,risk analysis)”
- “…[M]aking judgments about managing and tolerating risk on the basis of a risk analysis while considering influencing factors (i.e., risk evaluation)” 2
Relationships between assets, processes, threats, vulnerabilities and other factors are analyzed in the risk assessment approach. There are many methods available, but quantitative and qualitative analysis are the most widely known and used classifications. In general, the methodology chosen at the beginning of the decision-making process should be able to produce a quantitative explanation about the impact of the risk and security issues along with the identification of risk and formation of a risk register. There should also be qualitative statements that explain the importance and suitability of controls and security measures to minimize these risk areas. 3
In general, the risk management life cycle includes seven main processes that support and complement each other ( figure 1 ):
- Determine the risk context and scope, then design the risk management strategy.
- Choose the responsible and related partners, identify the risk and prepare the risk registers.
- Perform qualitative risk analysis and select the risk that needs detailed analysis.
- Perform quantitative risk analysis on the selected risk.
- Plan the responses and determine controls for the risk that falls outside the risk appetite.
- Implement risk responses and chosen controls.
- Monitor risk improvements and residual risk.

Qualitative and Quantitative Risk Analysis Techniques
Different techniques can be used to evaluate and prioritize risk. Depending on how well the risk is known, and if it can be evaluated and prioritized in a timely manner, it may be possible to reduce the possible negative effects or increase the possible positive effects and take advantage of the opportunities. 4 “Quantitative risk analysis tries to assign objective numerical or measurable values” regardless of the components of the risk assessment and to the assessment of potential loss. Conversely, “a qualitative risk analysis is scenario-based.” 5
Qualitative Risk The purpose of qualitative risk analysis is to identify the risk that needs detail analysis and the necessary controls and actions based on the risk’s effect and impact on objectives. 6 In qualitative risk analysis, two simple methods are well known and easily applied to risk: 7
- Keep It Super Simple (KISS) —This method can be used on narrow-framed or small projects where unnecessary complexity should be avoided and the assessment can be made easily by teams that lack maturity in assessing risk. This one-dimensional technique involves rating risk on a basic scale, such as very high/high/medium/low/very.
- Probability/Impact —This method can be used on larger, more complex issues with multilateral teams that have experience with risk assessments. This two-dimensional technique is used to rate probability and impact. Probability is the likelihood that a risk will occur. The impact is the consequence or effect of the risk, normally associated with impact to schedule, cost, scope and quality. Rate probability and impact using a scale such as 1 to 10 or 1 to 5, where the risk score equals the probability multiplied by the impact.
Qualitative risk analysis can generally be performed on all business risk. The qualitative approach is used to quickly identify risk areas related to normal business functions. The evaluation can assess whether peoples’ concerns about their jobs are related to these risk areas. Then, the quantitative approach assists on relevant risk scenarios, to offer more detailed information for decision-making. 8 Before making critical decisions or completing complex tasks, quantitative risk analysis provides more objective information and accurate data than qualitative analysis. Although quantitative analysis is more objective, it should be noted that there is still an estimate or inference. Wise risk managers consider other factors in the decision-making process. 9
Although a qualitative risk analysis is the first choice in terms of ease of application, a quantitative risk analysis may be necessary. After qualitative analysis, quantitative analysis can also be applied. However, if qualitative analysis results are sufficient, there is no need to do a quantitative analysis of each risk.
Quantitative Risk A quantitative risk analysis is another analysis of high-priority and/or high-impact risk, where a numerical or quantitative rating is given to develop a probabilistic assessment of business-related issues. In addition, quantitative risk analysis for all projects or issues/processes operated with a project management approach has a more limited use, depending on the type of project, project risk and the availability of data to be used for quantitative analysis. 10
The purpose of a quantitative risk analysis is to translate the probability and impact of a risk into a measurable quantity. 11 A quantitative analysis: 12
- “Quantifies the possible outcomes for the business issues and assesses the probability of achieving specific business objectives”
- “Provides a quantitative approach to making decisions when there is uncertainty”
- “Creates realistic and achievable cost, schedule or scope targets”
Consider using quantitative risk analysis for: 13
- “Business situations that require schedule and budget control planning”
- “Large, complex issues/projects that require go/no go decisions”
- “Business processes or issues where upper management wants more detail about the probability of completing on schedule and within budget”
The advantages of using quantitative risk analysis include: 14
- Objectivity in the assessment
- Powerful selling tool to management
- Direct projection of cost/benefit
- Flexibility to meet the needs of specific situations
- Flexibility to fit the needs of specific industries
- Much less prone to arouse disagreements during management review
- Analysis is often derived from some irrefutable facts
THE MOST COMMON PROBLEM IN QUANTITATIVE ASSESSMENT IS THAT THERE IS NOT ENOUGH DATA TO BE ANALYZED.
To conduct a quantitative risk analysis on a business process or project, high-quality data, a definite business plan, a well-developed project model and a prioritized list of business/project risk are necessary. Quantitative risk assessment is based on realistic and measurable data to calculate the impact values that the risk will create with the probability of occurrence. This assessment focuses on mathematical and statistical bases and can “express the risk values in monetary terms, which makes its results useful outside the context of the assessment (loss of money is understandable for any business unit). 15 The most common problem in quantitative assessment is that there is not enough data to be analyzed. There also can be challenges in revealing the subject of the evaluation with numerical values or the number of relevant variables is too high. This makes risk analysis technically difficult.
There are several tools and techniques that can be used in quantitative risk analysis. Those tools and techniques include: 16
- Heuristic methods —Experience-based or expert- based techniques to estimate contingency
- Three-point estimate —A technique that uses the optimistic, most likely and pessimistic values to determine the best estimate
- Decision tree analysis —A diagram that shows the implications of choosing various alternatives
- Expected monetary value (EMV) —A method used to establish the contingency reserves for a project or business process budget and schedule
- Monte Carlo analysis —A technique that uses optimistic, most likely and pessimistic estimates to determine the business cost and project completion dates
- Sensitivity analysis —A technique used to determine the risk that has the greatest impact on a project or business process
- Fault tree analysis (FTA) and failure modes and effects analysis (FMEA) —The analysis of a structured diagram that identifies elements that can cause system failure
There are also some basic (target, estimated or calculated) values used in quantitative risk assessment. Single loss expectancy (SLE) represents the money or value expected to be lost if the incident occurs one time, and an annual rate of occurrence (ARO) is how many times in a one-year interval the incident is expected to occur. The annual loss expectancy (ALE) can be used to justify the cost of applying countermeasures to protect an asset or a process. That money/value is expected to be lost in one year considering SLE and ARO. This value can be calculated by multiplying the SLE with the ARO. 17 For quantitative risk assessment, this is the risk value. 18
USING BOTH APPROACHES CAN IMPROVE PROCESS EFFICIENCY AND HELP ACHIEVE DESIRED SECURITY LEVELS.
By relying on factual and measurable data, the main benefits of quantitative risk assessment are the presentation of very precise results about risk value and the maximum investment that would make risk treatment worthwhile and profitable for the organization. For quantitative cost-benefit analysis, ALE is a calculation that helps an organization to determine the expected monetary loss for an asset or investment due to the related risk over a single year.
For example, calculating the ALE for a virtualization system investment includes the following:
- Virtualization system hardware value: US$1 million (SLE for HW)
- Virtualization system management software value: US$250,000 (SLE for SW)
- Vendor statistics inform that a system catastrophic failure (due to software or hardware) occurs one time every 10 years (ARO = 1/10 = 0.1)
- ALE for HW = 1M * 1 = US$100,000
- ALE for SW = 250K * 0.1 = US$25,000
In this case, the organization has an annual risk of suffering a loss of US$100,000 for hardware or US$25,000 for software individually in the event of the loss of its virtualization system. Any implemented control (e.g., backup, disaster recovery, fault tolerance system) that costs less than these values would be profitable.
Some risk assessment requires complicated parameters. More examples can be derived according to the following “step-by-step breakdown of the quantitative risk analysis”: 19
- Conduct a risk assessment and vulnerability study to determine the risk factors.
- Determine the exposure factor (EF), which is the percentage of asset loss caused by the identified threat.
- Based on the risk factors determined in the value of tangible or intangible assets under risk, determine the SLE, which equals the asset value multiplied by the exposure factor.
- Evaluate the historical background and business culture of the institution in terms of reporting security incidents and losses (adjustment factor).
- Estimate the ARO for each risk factor.
- Determine the countermeasures required to overcome each risk factor.
- Add a ranking number from one to 10 for quantifying severity (with 10 being the most severe) as a size correction factor for the risk estimate obtained from company risk profile.
- Determine the ALE for each risk factor. Note that the ARO for the ALE after countermeasure implementation may not always be equal to zero. ALE (corrected) equals ALE (table) times adjustment factor times size correction.
- Calculate an appropriate cost/benefit analysis by finding the differences before and after the implementation of countermeasures for ALE.
- Determine the return on investment (ROI) based on the cost/benefit analysis using internal rate of return (IRR).
- Present a summary of the results to management for review.
Using both approaches can improve process efficiency and help achieve desired security levels. In the risk assessment process, it is relatively easy to determine whether to use a quantitative or a qualitative approach. Qualitative risk assessment is quick to implement due to the lack of mathematical dependence and measurements and can be performed easily. Organizations also benefit from the employees who are experienced in asset/processes; however, they may also bring biases in determining probability and impact. Overall, combining qualitative and quantitative approaches with good assessment planning and appropriate modeling may be the best alternative for a risk assessment process ( figure 2 ). 20

Qualitative risk analysis is quick but subjective. On the other hand, quantitative risk analysis is optional and objective and has more detail, contingency reserves and go/no-go decisions, but it takes more time and is more complex. Quantitative data are difficult to collect, and quality data are prohibitively expensive. Although the effect of mathematical operations on quantitative data are reliable, the accuracy of the data is not guaranteed as a result of being numerical only. Data that are difficult to collect or whose accuracy is suspect can lead to inaccurate results in terms of value. In that case, business units cannot provide successful protection or may make false-risk treatment decisions and waste resources without specifying actions to reduce or eliminate risk. In the qualitative approach, subjectivity is considered part of the process and can provide more flexibility in interpretation than an assessment based on quantitative data. 21 For a quick and easy risk assessment, qualitative assessment is what 99 percent of organizations use. However, for critical security issues, it makes sense to invest time and money into quantitative risk assessment. 22 By adopting a combined approach, considering the information and time response needed, with data and knowledge available, it is possible to enhance the effectiveness and efficiency of the risk assessment process and conform to the organization’s requirements.
1 ISACA ® , CRISC Review Manual, 6 th Edition , USA, 2015, https://store.isaca.org/s/store#/store/browse/detail/a2S4w000004Ko8ZEAS 2 Ibid. 3 Schmittling, R.; A. Munns; “Performing a Security Risk Assessment,” ISACA ® Journal , vol. 1, 2010, https://www.isaca.org/resources/isaca-journal/issues 4 Bansal,; "Differentiating Quantitative Risk and Qualitative Risk Analysis,” iZenBridge,12 February 2019, https://www.izenbridge.com/blog/differentiating-quantitative-risk-analysis-and-qualitative-risk-analysis/ 5 Tan, D.; Quantitative Risk Analysis Step-By-Step , SANS Institute Information Security Reading Room, December 2020, https://www.sans.org/reading-room/whitepapers/auditing/quantitative-risk-analysis-step-by-step-849 6 Op cit Bansal 7 Hall, H.; “Evaluating Risks Using Qualitative Risk Analysis,” Project Risk Coach, https://projectriskcoach.com/evaluating-risks-using-qualitative-risk-analysis/ 8 Leal, R.; “Qualitative vs. Quantitative Risk Assessments in Information Security: Differences and Similarities,” 27001 Academy, 6 March 2017, https://advisera.com/27001academy/blog/2017/03/06/qualitative-vs-quantitative-risk-assessments-in-information-security/ 9 Op cit Hall 10 Goodrich, B.; “Qualitative Risk Analysis vs. Quantitative Risk Analysis,” PM Learning Solutions, https://www.pmlearningsolutions.com/blog/qualitative-risk-analysis-vs-quantitative-risk-analysis-pmp-concept-1 11 Meyer, W. ; “Quantifying Risk: Measuring the Invisible,” PMI Global Congress 2015—EMEA, London, England, 10 October 2015, https://www.pmi.org/learning/library/quantitative-risk-assessment-methods-9929 12 Op cit Goodrich 13 Op cit Hall 14 Op cit Tan 15 Op cit Leal 16 Op cit Hall 17 Tierney, M.; “Quantitative Risk Analysis: Annual Loss Expectancy," Netwrix Blog, 24 July 2020, https://blog.netwrix.com/2020/07/24/annual-loss-expectancy-and-quantitative-risk-analysis 18 Op cit Leal 19 Op cit Tan 20 Op cit Leal 21 ISACA ® , Conductin g a n IT Security Risk Assessment, USA, 2020, https://store.isaca.org/s/store#/store/browse/detail/a2S4w000004KoZeEAK 22 Op cit Leal
Volkan Evrin, CISA, CRISC, COBIT 2019 Foundation, CDPSE, CEHv9, ISO 27001-22301-20000 LA
Has more than 20 years of professional experience in information and technology (I&T) focus areas including information systems and security, governance, risk, privacy, compliance, and audit. He has held executive roles on the management of teams and the implementation of projects such as information systems, enterprise applications, free software, in-house software development, network architectures, vulnerability analysis and penetration testing, informatics law, Internet services, and web technologies. He is also a part-time instructor at Bilkent University in Turkey; an APMG Accredited Trainer for CISA, CRISC and COBIT 2019 Foundation; and a trainer for other I&T-related subjects. He can be reached at [email protected] .
The Essentials of Effective Project Risk Assessments
By Kate Eby | September 19, 2022
- Share on Facebook
- Share on LinkedIn
Link copied
Performing risk assessments is vital to a project’s success. We’ve gathered tips from experts on doing effective risk assessments and compiled a free, downloadable risk assessment starter kit.
Included on this page, you’ll find details on the five primary elements of risk , a comprehensive step-by-step process for assessing risk , tips on creating a risk assessment report , and editable templates and checklists to help you perform your own risk assessments.
What Is a Project Risk Assessment?
A project risk assessment is a formal effort to identify and analyze risks that a project faces. First, teams identify all possible project risks. Next, they determine the likelihood and potential impact of each risk.
During a project risk assessment, teams analyze both positive and negative risks. Negative risks are events that can derail a project or significantly hurt its chances of success. Negative risks become more dangerous when teams haven’t identified them or created a plan to deal with them.
A project risk assessment also looks at positive risks. Also called opportunities, positive risks are events that stand to benefit the project or organization. Your project team should assess those risks so they can seize on opportunities when they arise.
Your team will want to perform a project risk assessment before the project begins. They should also continually monitor for risks and update the assessment throughout the life of the project.
Some experts use the term project risk analysis to describe a project risk assessment. However, a risk analysis typically refers to the more detailed analysis of a single risk within your broader risk assessment. For expert tips and information, see this comprehensive guide to performing a project risk analysis.
Project risk assessments are an important part of project risk management. Learn more from experts about best practices in this article on project risk management . For even more tips and resources, see this guide to creating a project risk management plan .
How Do You Assess Risk in a Project?
Teams begin project risk assessments by brainstorming possible project risks. Avoid missing important risks by reviewing events from similar past projects. Finally, analyze each risk to understand its time frame, probability, factors, and impact.
Your team should also gather input from stakeholders and others who might have thoughts on possible risks.
In general terms, consider these five important elements when analyzing risks:
- Risk Event: Identify circumstances or events that might have an impact on your project.
- Risk Time Frame: Determine when these events are most likely to happen. This might mean when they happen in the lifecycle of a project or during a sales season or calendar year.
- Probability: Estimate the likelihood of an event happening.
- Impact: Determine the impact on the project and your organization if the event happens.
- Factors: Determine the events that might happen before a risk event or that might trigger the event.
Project Risk Assessment Tools
Project leaders can use various tools and methodologies to help measure risks. One option is a failure mode and effects analysis. Other options include a finite element analysis or a factor analysis and information risk.
These are some common risk assessment tools:
- Process Steps: Identify all steps in a process.
- Potential Problems: Identify what could go wrong with each step.
- Problem Sources: Identify the causes of the problem.
- Potential Consequences: Identify the consequences of the problem or failure.
- Solutions: Identify ways to prevent the problem from happening.
- Finite Element Analysis (FEA): This is a computerized method for simulating and analyzing the forces on a structure and the ways that a structure could break. The method can account for many, sometimes thousands, of elements. Computer analysis then determines how each of those elements works and how often the elements won’t work. The analysis for each element is then added together to determine all possible failures and the rate of failure for the entire product.
- Factor Analysis of Information Risk (FAIR): This framework helps teams analyze risks to information data or cybersecurity risk.
How to Conduct a Project Risk Assessment
The project manager and team members will want to continually perform risk assessments for a project. Doing good risk assessments involves a number of steps. These steps include identifying all possible risks and assessing the probability of each.
Most importantly, team members must fully explore and assess all possible risks, including risks that at first might not be obvious.

“The best thing that a risk assessment process can do for any project, over time, is to be a way of bringing unrecognized assumptions to light,” says Mike Wills , a certified mentor and coach and an assistant professor at Embry-Riddle Aeronautical University’s College of Business. “We carry so many assumptions without realizing how they constrain our thinking.”
Steps in a Project Risk Assessment
Experts recommend several important steps in an effective project risk assessment. These steps include identifying potential risks, assessing their possible impact, and formulating a plan to prevent or respond to those risks.
Here are 10 important steps in a project risk assessment:
Step 1: Identify Potential Risks
Bring your team together to identify all potential risks to your project. Here are some common ways to help identify risks, with tips from experts:
- Review Documents: Review all documents associated with the project.
- Consider Industry-Specific Risks: Use risk prompt lists for your industry. Risk prompt lists are broad categories of risks, such as environmental or legal, that can occur in a project.
- Revisit Previous Projects: Use checklists from similar projects your organization has done in the past.

- “What I like to do for specific types of projects is put together a checklist, a taxonomy of old risks that you've identified in other projects from lessons learned,” says Wendy Romeu, President and CEO of Alluvionic . “Say you have a software development program. You would pull up your template that includes all the risks that you realized in other projects and go through that list of questions. Then you would ask: ‘Do these risks apply to our project?’ That's kind of a starting point.” “You do that with your core project team,” Romeu says, “and it gets their juices flowing.” Learn more about properly assessing lessons learned at the end of a project in this comprehensive guide to project management lessons learned .
- Consult Experts: Conduct interviews with experts within and, in some cases, outside your organization.
- Brainstorm: Brainstorm ideas with your team. “The best scenario, which doesn't usually happen, is the whole team comes together and identifies the risks,” says Romeu.
- Stick to Major Risks: Don’t try to identify an unrealistic or unwieldy number of risks. “You want to identify possible risks, but you want to keep the numbers manageable,” says Wills. “The more risks you identify, the longer you spend analyzing them. And the longer you’re in analysis, the fewer decisions you make.”
- Look for Positive Risks: Identify both positive risks and negative ones. It’s easy to forget that risks aren’t all negative. There can be unexpected positive events as well. Some people call these opportunities , but in a risk assessment, experts call them positive risks.

- “A risk is a future event that has a likelihood of occurrence and an impact,” says Alan Zucker, founding principal of Project Management Essentials , who has more than two decades of experience managing projects in Fortune 100 companies. “Risks can both be opportunities — good things — and threats. Most people, when they think about risk assessment, they always think about the negatives. I really try to stress on people to think about the opportunities as well.” Opportunities, or positive risks, might include your team doing great work on a project and a client wanting the team to do more work. Positive risks might include a project moving forward more quickly than planned or costing less money than planned. You’ll want to know how to respond in those situations, Zucker says. Learn more about project risk identification and find more tips from experts in this guide to project risk identification .
Step 2: Determine the Probability of Each Risk
After your team has identified possible risks, you will want to determine the probability of each risk happening. Your team can make educated guesses using some of the same methods it used to identify those risks.
Determine the probability of each identified risk with these tactics:
- Brainstorm with your team.
- Interview experts.
- Review similar past projects.
- Review other projects in the same industry.
Step 3: Determine the Impact of Each Risk
Your team will then determine the impact of each risk should it occur. Would the risk stop the project entirely or stop the development of a product? Or would the risk occurring have a relatively minor impact?
Assessing impact is important because if it’s a positive risk, Romeu says, “You want to make sure you’re doing the things to make it happen. Whereas if it's a high risk and a negative situation, you want to do the things to make sure it doesn't happen.”
There are two ways to measure impact: qualitative and quantitative. “Are we going to do just a qualitative risk assessment, where we're talking about the likelihood and the probability or the urgency of that risk?” asks Zucker. “Or are we going to do a quantitative risk assessment, where we're putting a dollar figure or a time figure to those risks?”
Most often, a team will analyze and measure risk based on qualitative impact. The team will analyze risk based on a qualitative description of what could happen, such as a project being delayed or failing. The team may judge that impact as significant but won’t put a dollar figure on it.
A quantitative risk assessment, on the other hand, estimates the impact in numbers, often measured in dollars or profits lost, should a risk happen. “Typically, for most projects, we don’t do a quantitative risk assessment,” Zucker says. “It’s usually when we’re doing engineering projects or big, federal projects. That’s where we're doing the quantitative.”
Step 4: Determine the Risk Score of Each Event
Once your team assesses possible risks, along with the risk probability and impact, it’s time to determine a risk score for each potential event. This score allows your organization to understand the risks that need the most attention.
Often, teams will use a simple risk matrix to determine that risk score. Your team will assign a score based on the probability of each risk event. It will then assign a second score based on the impact that event would have on the organization. Those two figures multiplied will give you each event or risk a risk score.
Zucker says he prefers to assign the numbers 1, 5, and 10 — for low, medium, and high — to both the likelihood of an event happening and its impact. In that scenario, an event with a low likelihood of happening (level of 1) and low impact (level of 1) would have a total risk score of 1 (1 multiplied by 1). An event with a high likelihood of happening (level of 10) and a large impact (level of 10) would have a total risk score of 100.
Zucker says he prefers using those numbers because a scale as small as one to three doesn't convey the importance of high-probability and high-impact risks. “A nine doesn't feel that bad,” he says. “But if it's 100, it's like, ‘Whoa, I really need to worry about that thing.’”
While these risk matrices use numbers, they are not really quantitative. Your teams are making qualitative judgments on events and assigning a rough score. In some cases, however, teams can determine a quantitative risk score.
Your team might determine, based on past projects or other information, that an event has a 10 percent chance of happening. For example, if that event will diminish your manufacturing plant’s production capacity by 50 percent for one month, your team might determine that it will cost your company $400,000. In that case, the risk would have a risk score of $40,000.
At the same time, another event might have a 40 percent chance of happening. Your team might determine the cost to the business would be $10,000. In that case, the risk score is $4,000.
“Just simple counts start to give you a quantifiable way of looking at risk,” says Wills. “A risk that is going to delay 10 percent of your production capacity is a different kind of risk than one that will delay 50 percent of it. Because you have a number, you can gather real operational data for a week or two and see how things support the argument. You can start to compare apples to apples, not apples to fish.”
Wills adds, “Humans, being very optimistic and terrible at predicting the future, will say, ‘Oh, I don't think it'll happen very often.’ Quantitative techniques help to get you away from this gambler fallacy kind of approach. They can make or break your argument to a stakeholder that says, ‘I've looked at this, and I can explain mechanically, count by the numbers like an accountant, what's going on and what might go wrong.’”
Step 5: Understand Your Risk Tolerance
As your team considers risks, it must understand the organization’s risk tolerance. Your team should know what kinds of risks that organizational leaders and stakeholders are willing to take to see a project through.
Understanding that tolerance will also help your team decide how and where to invest time and resources in order to prevent certain negative events.
Step 6: Decide How to Prioritize Risks
Once your team has determined the risk score for each risk, it will see which potential risks need the most attention. These are risks that are high impact and that your organization will want to work hard to prevent.
“You want to attack the ones that are high impact and high likelihood first,” says Romeu.
“Some projects are just so vital to what you do and how you do it that you cannot tolerate the risk of derailment or major failure,” says Wills. “So you're willing to spend money, time, and effort to contain that risk. On other projects, you're taking a flier. You're willing to lose a little money, lose a little effort.”
“You have to decide, based on your project, based on your organization, the markets you're in, is that an ‘oh my gosh, it's gonna keep me up every night’ kind of strategic risk? Or is it one you can deal with?” he says.
Step 7: Develop Risk Response Strategies
Once your team has assessed all possible risks and ranked them by importance, you will want to dive deeper into risk response strategies. That plan should include ways to respond to both positive and negative risks.
These are the main strategies for responding to threats or negative risks:
- Mitigate: These are actions you will take to reduce the likelihood of a risk event happening or that will reduce the impact if it does happen. “For example, if you’re building a datacenter, we might have backup power generators to mitigate the likelihood or the impact of a power loss,” says Zucker. You can learn more, including more tips from experts, about project risk mitigation .
- Avoid: If a certain action, new product, or new service carries an unacceptably high risk, you might want to avoid it entirely.
- Transfer: The most common way that organizations transfer risk is by buying insurance. A common example is fire insurance for a building. Another is cybersecurity insurance that would cover your company in the event of a data breach. An additional option is to transfer certain risks to other companies that can do the work and assume its risks for your company. “It could be if you didn't want to have the risk of running a datacenter anymore, you transfer that risk to Jeff Bezos (Amazon Web Services) or to Google or whoever,” Zucker says.
These are the main strategies for responding to opportunities or positive risks:
- Share: Your company might partner with another company to work together on achieving an opportunity, and then share in the benefits.
- Exploit: Your company and team work hard to make sure an event happens because it will benefit your company.
- Enhance: Your company works to improve the likelihood of something happening, with the understanding that it might not happen.
These are the main strategies for responding to both threats and opportunities, or negative and positive risks:
- Accept: Your company simply accepts that a risk might happen but continues on because the benefits of the action are significant. “You're not ignoring the risks, but you're saying, ‘I can't do anything practical about them,’” says Wills. “So they're there. But I'm not going to spend gray matter driving myself crazy thinking about them.”
- Escalate: This is when a project manager sees a risk as exceptionally high, impactful, and beyond their purview. The project manager should then escalate information about the risk to company leaders. They can then help decide what needs to happen. “Some project managers seem almost fearful about communicating risks to organization leaders,” Romeu says. “It drives me nuts. It's about communicating at the right level to the right people. At the executive level, it’s about communicating what risks are happening and what the impact of those risks are. If they happen, everybody knows what the plan is. And people aren't taken by surprise.”
Step 8: Monitor Your Risk Plans
Your team will want to understand how viable your organization’s risk plans are. That means you might want to monitor how they might work or how to test them.
A common example might be all-hands desktop exercises on a disaster plan. For example, how will a hospital respond to a power failure or earthquake? It’s like a fire drill, Zucker says. “Did we have a plan? Do people know what to do when the risk event occurs?”

Step 9: Perform Risk Assessments Continually
Your team will want to continually assess risks to the project. This step should happen throughout your project, from project planning to execution to closeout.
Zucker explains that the biggest mistake teams tend to make with project risk assessment: “People think it's a one-and-done event. They say, ‘I’ve put together my risk register, we’ve filed it into the documents that we needed to file, and I'm not worrying about it.’ I think that is probably the most common issue: that people don't keep it up. They don't think about it.”
Not thinking about how risks change and evolve throughout a project means project leaders won’t be ready for something when it happens. That’s why doing continual risk assessment as a primary part of risk management is vital, says Wills.
“Risk management is a process that should start before you start doing that activity. As you have that second dream about doing that project, start thinking about risk management,” he says. “And when you have completely retired that thing — you've shut down the business, you've pensioned everybody off, you’re clipping your coupons and working on your backstroke — that's when you're done with risk management. It's just a living, breathing, ongoing thing.”
Experts say project managers must learn to develop a sense for always assessing and monitoring risk. “As a PM, you should, in every single meeting you have, listen for risks,” Romeu says. “A technical person might say, ‘Well, this is going to be difficult because of X or Y or Z.’ That's a risk. They don't understand that's a risk, but as a PM, you should be aware of that.”
Step 10: Identify Lessons Learned
After your project is finished, your team should come together to identify the lessons learned during the project. Create a lessons learned document for future use. Include information about project risks in the discussion and the final document.
By keeping track of risks in a lessons learned document, you allow future leaders of similar projects to learn from your successes and failures. As a result, they can better understand the risks that could affect their project.
“Those lessons learned should feed back into the system — back into that original risk checklist,” Romeu says. “So the next software development project knows to look at these risks that you found.”
How to Write a Project Risk Assessment Report
Teams will often track risks in an online document that is accessible to all team members and organization leaders. Sometimes, a project manager will also create a separate project risk assessment report for top leaders or stakeholders.
Here are some tips for creating that report:
- Find an Appropriate Template for Your Organization, Industry, and Project: You can find a number of templates that will help guide you in creating a risk assessment report. Find a project risk assessment report template in our project risk assessment starter kit.
- Consider Your Audience: As you create the report, remember your audience. For example, a report for a technical team will be more detailed than a report for the CEO of your company. Some more detailed reports for project team members might include a full list of risks, which would be 100 or more. “But don't show executives that list; they will lose their mind,” says Romeu.
Project Risk Assessment Starter Kit
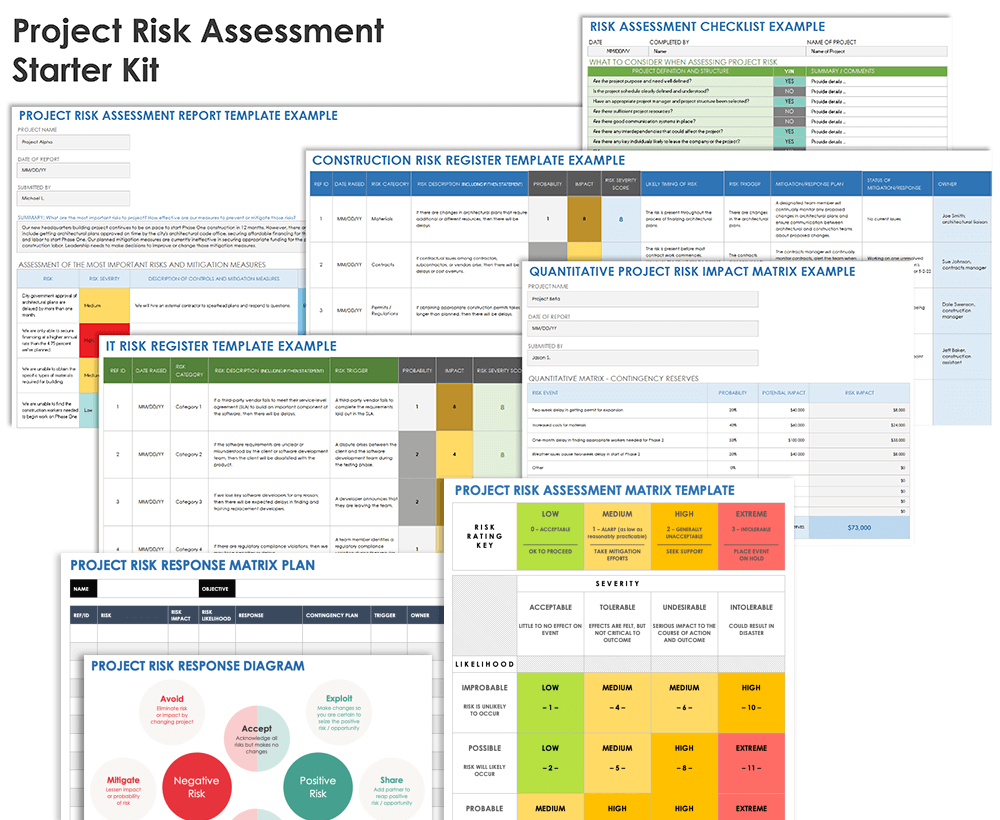
Download Project Risk Assessment Starter Kit
This starter kit includes a checklist on assessing possible project risks, a risk register template, a template for a risk impact matrix, a quantitative risk impact matrix, a project risk assessment report template, and a project risk response table. The kit will help your team better understand how to assess and continually monitor risks to a project.
In this kit, you’ll find:
- A risk assessment checklist PDF document and Microsoft Word to help you identify potential risks for your project. The checklist included in the starter kit is based on a document from Alluvionic Project Management Services.
- A project risk register template for Microsoft Excel to help you identify, analyze, and track project risks.
- A project risk impact assessment matrix for Microsoft Excel to assess the probability and impact of various risks.
- A quantitative project risk impact matrix for Microsoft Excel to quantify the probability and impact of various risks.
- A project risk assessment report template for Microsoft Excel to help you communicate your risk assessment findings and risk mitigation plans to company leadership.
- A project risk response diagram PDF document and Microsoft Word to better understand how to respond to various positive and negative risks.
Expertly Assess and Manage Project Risks with Real-Time Work Management in Smartsheet
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.
Discover why over 90% of Fortune 100 companies trust Smartsheet to get work done.
- Product overview
- All features
- Latest feature release
- App integrations
- project icon Project management
- Project views
- Custom fields
- Status updates
- goal icon Goals and reporting
- Reporting dashboards
- asana-intelligence icon Asana AI
- workflow icon Workflows and automation
- portfolio icon Resource management
- Capacity planning
- Time tracking
- my-task icon Admin and security
- Admin console
- Permissions
- list icon Personal
- premium icon Starter
- briefcase icon Advanced
- Goal management
- Organizational planning
- Project intake
- Resource planning
- Product launches
- View all uses arrow-right icon
- Work management resources Discover best practices, watch webinars, get insights
- Customer stories See how the world's best organizations drive work innovation with Asana
- Help Center Get lots of tips, tricks, and advice to get the most from Asana
- Asana Academy Sign up for interactive courses and webinars to learn Asana
- Developers Learn more about building apps on the Asana platform
- Community programs Connect with and learn from Asana customers around the world
- Events Find out about upcoming events near you
- Partners Learn more about our partner programs
- Asana for nonprofits Get more information on our nonprofit discount program, and apply.
- Project plans
- Team goals & objectives
- Team continuity
- Meeting agenda
- View all templates arrow-right icon
- Project planning |
- 7 common project risks and how to preve ...
7 common project risks and how to prevent them

Analyzing risk is an important part of the project planning process. Having a clear sense of the project risks you face, can help you prevent or prepare for upcoming risks. In this article, learn about seven of the most common project risks. Then, empower your team to find solutions before these issues derail important initiatives.
As a project manager, knowing what could go wrong during your project can help you set your team members up for success. For example, what if project stakeholders propose a new app and you don’t consider the time and resources it will take to create it? When the app heads to the development team, the project is at risk of falling apart before it starts.
![risks in research project [inline illustration] 7 common project risks (infographic)](https://assets.asana.biz/transform/18a22dea-e864-4e6c-8864-0dc108e7823e/inline-project-planning-project-risks-1-2x?io=transform:fill,width:2560&format=webp)
1. Scope creep
Scope risk, also known as scope creep , occurs when the initial project objectives aren’t well-defined. It’s important to communicate your project roadmap with stakeholders from the beginning and hold firm to those parameters. If you don’t communicate your project scope effectively, stakeholders may try to change requirements mid-project.
How to mitigate scope creep: Creating clear project parameters from the start will strengthen your project scope. Agreeing upon the project scope and communicating that vision with stakeholders from the beginning will leave less room for scope creep. Scheduling regular progress check-ins can also ensure the project stays in line with the original project scope.
2. Low performance
Performance risk occurs when the project doesn’t perform as well as initially expected. While you can’t always identify the root cause of low performance, you can identify project risks that may lead to low performance and look for ways to prevent those risks. Examples of these risks include a time crunch and miscommunication among team members.
How to mitigate low performance: Anticipating potential performance risks early on in the planning process can help you prepare. Using project management software lets you follow your processes in real time, plan your project thoroughly, and promote open communication between team members.
3. High costs
Cost risk occurs when your project goes over the budget you initially set. Cost risk can occur because of unrealistic or lack of detailed budgeting in the project planning phase. For example, you may feel confident that your project will be completed under-budget. However, creating a detailed list of every project element and what they cost can help you anticipate project needs.
How to mitigate high costs: To mitigate cost risk, estimate each element of your project accurately and stick closely to your budget. The best way to stick to your budget is to create a project plan template to align on deliverables, scope, and schedule. When your project goes into development, consider scheduling regular check-ins to review your budget and how you’re pacing.
4. Time crunch
Time risk, also known as project schedule risk, is the risk that tasks in your project will take longer than expected. Delayed timelines might impact other things like your budget, delivery date, or overall performance. This is a common risk that you may run into as project manager. When you’re not doing the work yourself across lots of moving pieces, it’s easy to underestimate the time it’ll take team members to complete a project during the initial planning phase.
How to mitigate a time crunch: To mitigate time risk, a rule of thumb is to overestimate the time needed to complete tasks in the planning phase and build in time contingency. That way, you’ll have wiggle room for scheduling later on. You can also create a project schedule using a Timeline or Gantt chart . Having clarity into work, dependencies between work, and any delays can help project managers dynamically adapt to time risk as it crops up. Understanding your project lifecycle can also help you determine how long each task will take.
5. Stretched resources
Resource risk occurs if you don’t have enough resources to complete the project. Resources may include time, skills, money, or tools. As a project manager, you’re responsible for the procurement of resources for your team and communicating with your team about the status of resources. Resource allocation should happen early in the project planning process, typically 1-2 months before project execution, depending on project size.
How to mitigate stretched resources: The best way to mitigate resource risk is to create a resource allocation plan . A resource allocation plan makes the best use of team resources while maximizing resource impact and supporting team goals. When you know what resources you need from the beginning, you minimize the chance of running out of resources later.
6. Operational changes
Operational risk involves changes in company or team processes, like an unexpected shift in team roles, changes in management, or new processes that your team must adjust to. These things can create distractions, require adjustments in workflows, and may impact project timelines.
How to mitigate operational mishaps: You can’t predict or prevent all operational risks, but if you know a team shift or process change is coming, you can mitigate the effects of the transition. Make sure your team is prepared for the change and has time to adjust through team meetings, scheduling tools, or additional trainings.
7. Lack of clarity
Lack of clarity may come in the form of miscommunication from stakeholders, vague project scopes, or unclear deadlines. The result can be a lack of visibility due to siloed work, going over budget, falling behind project deadlines, changing project requirements, having to pivot project direction, or disappointing project outcomes.
How to mitigate lack of clarity: When planning your project, check and recheck your requirements to ensure everything is in place. Is everyone involved on the same page? Are developers prepared for the next phase? Is the scope clearly defined? It's also important to make sure project information is accessible to all. By keeping information in a central tool, you can ensure everyone stays updated as the project progresses.
How to use risk management to prepare your team
Risk management involves identifying what risk categories are most likely to affect your project and making a plan to mitigate those risks.
![risks in research project [inline illustration] How to use risk management to prepare your team (infographic)](https://assets.asana.biz/transform/38149ca9-6a23-46ea-a97d-42eb53dd9f26/inline-project-planning-project-risks-2-2x?io=transform:fill,width:2560&format=webp)
Project management tools make risk management easier because they allow you to organize your projects from start to finish. You can also use work management software to collaborate across teams, which will make the most common risks less likely.
Using the following four steps, you can anticipate risk and keep your projects running smoothly.
1. Risk identification
The first step in the risk analysis process is identifying risks you think could affect your project. We mentioned the seven most common risk events above, but other project risks could include contractor failure, unexpected life events, data transfer issues, shifting priorities, legal risk, market risk, and project deferral.
Ask yourself these questions below to begin the risk identification process:
What is the likelihood of this risk event?
What are the impact and severity if the risk occurs?
What is our risk response plan?
Given the likelihood and impact, what is the priority level?
Who owns this risk?
Once you have an answer to these questions, you’ll continue the risk management process through prioritization of risks, actionable solutions, and regular monitoring.
2. Determine the likelihood and impact
You can sort through your list of risks by determining which ones are most likely to occur. Placing the risks in order of likelihood will give you a better idea of which risks to prioritize as you prepare a plan of action.
Not only is the likelihood of occurrence important when prioritizing risks, but assessing the business impact of each risk matters as well. You should plan more carefully for the risks that have the potential to cause significant business impact.
3. Find solutions for each risk
Creating a game plan on how your team will deal with each risk is the goal when conducting risk assessments. Sorting risks based on likelihood and business impact will give you a starting point for finding solutions. Conducting a risk assessment will make your projects more successful because you can prevent risk along the way.
You can meet with relevant project stakeholders to proactively identify reasonable solutions for project risks that might be top of mind for them. Take a look at lessons learned from past projects to gauge how risks were handled.
4. Monitor your risk assessment regularly
Once you’ve developed your risk assessment, it’s important to monitor it regularly because circumstances can change. The likelihood of risk can shift and so can the business impact.
It’s also possible that new risks can come into play or risks that were once possible may become less likely. Monitoring your risk assessment regularly can make you feel the most prepared for uncertain events.
Project risk management tools
The right tools can make the risk assessment process easier because they allow you to analyze and prioritize risk. With real-time tracking and shared information in one place, everyone on your team can have instant access to project materials and you can monitor team progress.
Project management tools can also help your team develop strong project planning skills. Knowing your process and the project management phases can prevent risks before they occur.
Risk register
A risk register is the ultimate tool for identifying and prioritizing risk. A risk register should include the likelihood of each risk, the business impact, how you hope to prevent the risk, how you plan to respond to the risk if it occurs, and who will take action.
Below is an example of what a risk register might look like. The left side shows the type of risk followed by the likelihood of the risk, the level of business impact, the person responsible for taking action, and the mitigating action.
![risks in research project [List View] Example risk register project in Asana](https://assets.asana.biz/transform/aa7a1c85-5c6c-47e3-b8b3-e161bfb0f353/inline-project-management-risk-registry-3-2x-png?io=transform:fill,width:2560&format=webp)
After completing a risk register, you’ll have a living document to use when working through projects. You can reference this information as you encounter risks and use it to reduce long-term damage.
SWOT analysis
SWOT stands for strengths, weaknesses, opportunities, and threats. A SWOT analysis goes beyond identifying the risks for a project because it also identifies the strong points in your project. You can use your project’s strong points to stand out among competitors.
To complete a SWOT analysis, go through each letter of the acronym and ask questions like the ones below to uncover new ways to improve your project and prepare your team.
Strength: What do we do well?
Weakness: What could be improved?
Opportunity: What are our goals for the year?
Threat: Where are our competitors outperforming us?
After creating a SWOT analysis, you can feel confident moving forward with projects because you’ll have a better understanding of where you stand in relation to competitors. You’ll also know your strengths and weaknesses, which can help you improve future projects and mitigate risk.
Brainstorming
Brainstorming is a powerful way to come up with ideas, but its effectiveness can often get overlooked. When you have a team with different perspectives, brainstorming is a great way to spark creativity and assess risk.
Brainstorming is often the first step in creating a risk register because to identify risk, you must start somewhere. Learning new brainstorming techniques can help your team identify risk, keep your team agile, and potentially prevent risk from occurring.
Plan ahead to mitigate project risk
The project planning phase is the most important part of any project. You may think that the development phase is where the magic happens, but planning for your project is what prevents project risks and leads your team to success.
There are various types of project management software out there that allow you to automate processes, streamline communication, share information, and provide real-time tracking. With these tools in tow, you can transform your projects from good to great.
Related resources
7 steps to crafting a winning event proposal (with template)

How Asana drives impactful product launches in 3 steps
How to streamline compliance management software with Asana

New site openings: How to reduce costs and delays
Search form
Research and innovation menu, research and innovation, risks to research participants.
The University of Oregon accepts as a basic principle that it has an ethical and moral obligation to safeguard the rights and welfare of all subjects involved in research, training, educational development and other activities where subjects are exposed to a risk that could be detrimental to their health or well-being. In those cases where risk may exist, even with informed consent, approval of a research project will be made only if the potential risks to the individual are outweighed by potential benefits. In evaluating risks and benefits, the CPHS/IRB shall not consider long-range effects of applying knowledge gained in the research as among those risks that fall within the CPHS/IRB's purview of responsibility.
The university shall be responsible for physical or psychological injury to human subjects attributable to university-sponsored research, development, and related activities, to the extent that the university may be found liable under federal and state laws. Therefore, the obligation of researchers to conduct activities in a manner and at such locations as will assure the proximity of adequate medical attention if warranted, and to provide appropriate referrals to subjects for adequate facilities and professional attention should subjects suffer physical, psychological or other injury, is of paramount importance when designing research involving human subjects.
The seriousness of a risk to subjects is a function of the magnitude of the harm and the probability of the harm. A risk may be serious or significant because it has a probability (even a low probability) of great harm (e.g., a low probability of death), or because it has a high probability of slight harm (e.g., a near certainty of physical discomfort or psychological distress).
The risks of participation in research may be part of the research design or may be a consequence of the research procedures, or both (e.g., the risks of an adverse reaction to an investigational drug are part of the research design, while the risk of hematoma from blood drawn in the research is not part of the design but a consequence of the research procedures). Risks may be a consequence of the methods of recording, maintaining, or reporting data, and they may be a consequence of methods of obtaining informed consent.
- Download PDF
- CME & MOC
- Share X Facebook Email LinkedIn
- Permissions
Accounting for Competing Risks in Clinical Research
- 1 Institute for Clinical Evaluative Sciences (ICES), Toronto, Ontario, Canada
- 2 Institute of Health Policy, Management and Evaluation, University of Toronto, Toronto, Ontario, Canada
- 3 Sunnybrook Research Institute, Toronto, Ontario, Canada
- 4 NHS Blood and Transplant, Bristol, United Kingdom
- 5 Department of Biomedical Data Sciences, Leiden University Medical Center, Leiden, the Netherlands
- Original Investigation Metformin or Sulfonylurea Use in Kidney Disease Christianne L. Roumie, MD, MPH; Jonathan Chipman, PhD; Jea Young Min, PharmD, MPH, PhD; Amber J. Hackstadt, PhD; Adriana M. Hung, MD, MPH; Robert A. Greevy Jr, PhD; Carlos G. Grijalva, MD, MPH; Tom Elasy, MD, MPH; Marie R. Griffin, MD, MPH JAMA
Survival analyses are statistical methods for the analysis of time-to-event outcomes. 1 An example is time from study entry to death. A competing risk is an event whose occurrence precludes the occurrence of the primary event of interest. In a study whose outcome is time to death due to cardiovascular causes, for instance, death due to a noncardiovascular cause is a competing risk. Conventional statistical methods for the analysis of survival data typically aim to estimate the probability of the event of interest over time or the effect of a risk factor or treatment on that probability or on the intensity with which events occur. These methods require modification in the presence of competing risks. A key feature of survival analysis is the ability to properly account for censoring, which occurs when the outcome event is not observed before the end of the study participant’s follow-up period.
Read More About
Austin PC , Ibrahim M , Putter H. Accounting for Competing Risks in Clinical Research. JAMA. 2024;331(24):2125–2126. doi:10.1001/jama.2024.4970
Manage citations:
© 2024
Artificial Intelligence Resource Center
Cardiology in JAMA : Read the Latest
Browse and subscribe to JAMA Network podcasts!
Others Also Liked
Select your interests.
Customize your JAMA Network experience by selecting one or more topics from the list below.
- Academic Medicine
- Acid Base, Electrolytes, Fluids
- Allergy and Clinical Immunology
- American Indian or Alaska Natives
- Anesthesiology
- Anticoagulation
- Art and Images in Psychiatry
- Artificial Intelligence
- Assisted Reproduction
- Bleeding and Transfusion
- Caring for the Critically Ill Patient
- Challenges in Clinical Electrocardiography
- Climate and Health
- Climate Change
- Clinical Challenge
- Clinical Decision Support
- Clinical Implications of Basic Neuroscience
- Clinical Pharmacy and Pharmacology
- Complementary and Alternative Medicine
- Consensus Statements
- Coronavirus (COVID-19)
- Critical Care Medicine
- Cultural Competency
- Dental Medicine
- Dermatology
- Diabetes and Endocrinology
- Diagnostic Test Interpretation
- Drug Development
- Electronic Health Records
- Emergency Medicine
- End of Life, Hospice, Palliative Care
- Environmental Health
- Equity, Diversity, and Inclusion
- Facial Plastic Surgery
- Gastroenterology and Hepatology
- Genetics and Genomics
- Genomics and Precision Health
- Global Health
- Guide to Statistics and Methods
- Hair Disorders
- Health Care Delivery Models
- Health Care Economics, Insurance, Payment
- Health Care Quality
- Health Care Reform
- Health Care Safety
- Health Care Workforce
- Health Disparities
- Health Inequities
- Health Policy
- Health Systems Science
- History of Medicine
- Hypertension
- Images in Neurology
- Implementation Science
- Infectious Diseases
- Innovations in Health Care Delivery
- JAMA Infographic
- Law and Medicine
- Leading Change
- Less is More
- LGBTQIA Medicine
- Lifestyle Behaviors
- Medical Coding
- Medical Devices and Equipment
- Medical Education
- Medical Education and Training
- Medical Journals and Publishing
- Mobile Health and Telemedicine
- Narrative Medicine
- Neuroscience and Psychiatry
- Notable Notes
- Nutrition, Obesity, Exercise
- Obstetrics and Gynecology
- Occupational Health
- Ophthalmology
- Orthopedics
- Otolaryngology
- Pain Medicine
- Palliative Care
- Pathology and Laboratory Medicine
- Patient Care
- Patient Information
- Performance Improvement
- Performance Measures
- Perioperative Care and Consultation
- Pharmacoeconomics
- Pharmacoepidemiology
- Pharmacogenetics
- Pharmacy and Clinical Pharmacology
- Physical Medicine and Rehabilitation
- Physical Therapy
- Physician Leadership
- Population Health
- Primary Care
- Professional Well-being
- Professionalism
- Psychiatry and Behavioral Health
- Public Health
- Pulmonary Medicine
- Regulatory Agencies
- Reproductive Health
- Research, Methods, Statistics
- Resuscitation
- Rheumatology
- Risk Management
- Scientific Discovery and the Future of Medicine
- Shared Decision Making and Communication
- Sleep Medicine
- Sports Medicine
- Stem Cell Transplantation
- Substance Use and Addiction Medicine
- Surgical Innovation
- Surgical Pearls
- Teachable Moment
- Technology and Finance
- The Art of JAMA
- The Arts and Medicine
- The Rational Clinical Examination
- Tobacco and e-Cigarettes
- Translational Medicine
- Trauma and Injury
- Treatment Adherence
- Ultrasonography
- Users' Guide to the Medical Literature
- Vaccination
- Venous Thromboembolism
- Veterans Health
- Women's Health
- Workflow and Process
- Wound Care, Infection, Healing
- Register for email alerts with links to free full-text articles
- Access PDFs of free articles
- Manage your interests
- Save searches and receive search alerts

APDA awards $2.6M to support Parkinson’s research projects
American Parkinson Disease Association increases funding by over 30%

by Margarida Maia, PhD | September 11, 2024
Share this article:

The American Parkinson Disease Association (APDA) has awarded a total of $2.6 million for the 2024-2025 funding year, to support a range of research projects that aim to advance understanding of Parkinson’s disease .
The nationwide grassroots network increased its funding package by more than 30% over last year, the nonprofit noted in a press release announcing the new research grant recipients.
Research areas range from brain changes behind cognitive impairment to genetic causes of Parkinson’s, to health disparities among underrepresented patient communities. Other projects will seek to discover new insights into how the neurodegenerative disease develops and can be treated.
“At APDA, we believe in the power of progress and the hope it brings to the Parkinson’s community,” said Leslie A. Chambers, the APDA’s president and CEO. “We are immensely proud to play a pivotal role in advancing these groundbreaking projects that might otherwise never take flight, and in doing so, we continue to bring hope to everyone impacted by Parkinson’s.”

Platform launched for sharing brain samples in Parkinson’s research
Apda funding aims to serve as catalyst for future larger grants.
Approximately 1 million people in the U.S. have Parkinson’s, with 90,000 new diagnoses each year, according to the APDA, which calls research essential for ultimately improving treatment. The nonprofit says its mission is to support new researchers with initial funding, helping them gather data to then secure further financial backing.
“By providing essential seed funding, we empower researchers to explore innovative ideas and gather critical pilot data. This early support often acts as a catalyst, enabling them to secure larger grants from prestigious institutions like the National Institutes of Health,” Chambers said.
One of APDA’s most prestigious awards is the George C. Cotzias Memorial Fellowship , given to a young neurologist for three years. This year’s awardee, William Zeiger, MD, PhD, of the University of California, Los Angeles, will use a mouse model of the disease to study how Parkinson’s impairs brain circuits involved in cognition. The award is $100,000 for each of the three years for salary and supporting research expenses.
With its Diversity in Parkinson’s Disease Research Grants, the APDA funds projects that address health disparities. Three awards were given this year to young investigators to advance their work:
- Ignacio Mata, PhD, of the Cleveland Clinic Foundation, is developing a machine-learning model to predict uncontrolled movements, a side effect of long-term treatment with levodopa , in Latino patients.
- Melissa Nirenberg, PhD, of the Bronx Veterans Medical Research Foundation in New York, will investigate how Parkinson’s manifests in Black and Hispanic former military service members .
- Danielle Shpiner, MD, of the Miller School of Medicine at the University of Miami, is working to improve care access for Hispanic patients.
A post-doctoral fellowship was been awarded to Andrew Monaghan, PhD, at Emory University in Atlanta, who is studying brain circuits involved in walking difficulties in people with Parkinson’s. At the University of Minnesota, Twin Cities, Yuxiao Ning, PhD, another post-doctoral fellowship awardee, will watch how the brain changes during deep brain stimulation — a surgical treatment for Parkinson’s.
Donghe Yang, PhD, of the Memorial Sloan Kettering Cancer Center in New York, also was awarded a post-doctoral fellowship. Yang will unravel how to develop dopaminergic neurons — the nerve cells that are lost in Parkinson’s — from stem cells.
Two other fellowships went to Brianne Rogers, PhD, of the HudsonAlpha Institute for Biotechnology in Huntsville, Alabam, and Carlos Soto-Faguás, PhD, of the Oregon Health and Science University. Both of these scientists will investigate genes and mutations involved in Parkinson’s.

Gene with scant role in Parkinson’s research helps flies to walk again
Over $1 million will go to nonprofit’s 9 centers for advanced research.
The APDA also funds innovative research into Parkinson’s being done by scientists at major academic institutions . This year, eight researchers were given such awards:
- Patricia Aguilar Calvo, PhD, of the University of Alabama at Birmingham
- Athanasios Alexandris, MD, from the Johns Hopkins University School of Medicine
- Saar Anis, MD, of the Cleveland Clinic Foundation
- Helen Hwang, MD, PhD, of the Washington University School of Medicine
- Francesca Magrinelli, MD, PhD, at the University College London Institute of Neurology
- Franchino Porciuncula, of Boston University
- Emily Rocha, PhD, from the University of Pittsburgh
- Mariangela Scarduzio, PhD, from the University of Alabama at Birmingham.
The nonprofit also continues to support its Centers for Advanced Research , which drive large research programs and late-stage clinical translation. This year, a new center was funded at Yale School of Medicine, adding to a list of eight other centers already funded by the APDA. Together the centers were awarded more than $1 million for 2024-2025.
We have an incredible responsibility to the Parkinson’s community to choose the research that shows the most promise for real progress, as well as a responsibility to our donors to make sure every dollar counts in the search for answers.
Rebecca Gilbert, MD, PhD, chief mission officer at APDA, noted that the organization’s scientific advisory board considered numerous “excellent” applications and “had to make tough choices” in making its funding awards.
“We have an incredible responsibility to the Parkinson’s community to choose the research that shows the most promise for real progress, as well as a responsibility to our donors to make sure every dollar counts in the search for answers,” Gilbert said.
Chambers noted that “this vital work is made possible by the support of our generous APDA donors .”
About the Author

Recent Posts
- Electroacupuncture reduced cellular signs of Parkinson’s in mouse model
- New panel of cell-based tests may help screen potential treatments
- How I’m changing my mindset to realize my full potential
- Companion app to be developed for Parkinson’s treatment Flexilev
- Scientists learn how to target ‘undruggable’ Parkinson’s enzymes
Recommended reading

Exploring some helpful Parkinson’s resources available online

Parkinson’s UK funding 2 research projects into risk, protective factors

Project seeking to enhance patients’ speech awarded 5-year NIH grant
Subscribe to our newsletter.
Get regular updates to your inbox.
- Study Protocol
- Open access
- Published: 09 September 2024
A multi-state evaluation of extreme risk protection orders: a research protocol
- April M. Zeoli 1 ,
- Amy Molocznik 2 ,
- Jennifer Paruk 3 ,
- Elise Omaki 2 ,
- Shannon Frattaroli 2 ,
- Marian E. Betz 4 ,
- Annette Christy 5 ,
- Reena Kapoor 6 ,
- Christopher Knoepke 7 ,
- Wenjuan Ma 8 ,
- Michael A. Norko 6 ,
- Veronica A. Pear 9 ,
- Ali Rowhani-Rahbar 10 ,
- Julia P. Schleimer 9 ,
- Jeffrey W. Swanson 11 &
- Garen J. Wintemute 9
Injury Epidemiology volume 11 , Article number: 49 ( 2024 ) Cite this article
65 Accesses
Metrics details
Extreme Risk Protection Orders (ERPOs) are civil court orders that prohibit firearm purchase and possession when someone is behaving dangerously and is at risk of harming themselves and/or others. As of June 2024, ERPOs are available in 21 states and the District of Columbia to prevent firearm violence. This paper describes the design and protocol of a six-state study of ERPO use.
The six states included are California, Colorado, Connecticut, Florida, Maryland, and Washington. During the 3-year project period (2020–2023), ERPO case files were obtained through public records requests or through agreements with agencies with access to these data in each state. A team of over four dozen research assistants from seven institutions coded 6628 ERPO cases, abstracting 80 variables per case under domains related to respondent characteristics, events and behaviors leading to ERPO petitions, petitioner types, and court outcomes. Research assistants received didactic training through an online learning management system that included virtual training modules, quizzes, practice coding exercises, and two virtual synchronous sessions. A protocol for gaining strong interrater reliability was used. Research assistants also learned strategies for reducing the risk of experiencing secondary trauma through the coding process, identifying its occurrence, and obtaining help.
Addressing firearm violence in the U.S. is a priority. Understanding ERPO use in these six states can inform implementation planning and ERPO uptake, including promising opportunities to enhance safety and prevent firearm-related injuries and deaths. By publishing this protocol, we offer detailed insight into the methods underlying the papers published from these data, and the process of managing data abstraction from ERPO case files across the multi-state and multi-institution teams involved. Such information may also inform future analyses of this data, and future replication efforts.
Registration
This protocol is registered on Open Science Framework ( https://osf.io/kv4fc/ ).
In 2022 in the United States, over 27,000 people died by firearm suicide and more than 20,000 people were killed as a result of interpersonal firearm violence resulting in 14.2/100,000 people dying from intentional firearm injuries that year (Centers for Disease Control and Prevention, National Center for Injury Prevention and Control 2023 ). Preventing firearm access by those identified to be at risk of harming themselves and/or others is a logical strategy to reduce firearm homicide, firearm suicide, and nonfatal firearm violence. One promising and innovative opportunity to address firearm violence, therefore, is with extreme risk protection order (ERPO) laws. ERPO laws, or “red flag laws” as they are often called in popular discourse, provide a civil court process to temporarily prohibit firearm purchase and possession by individuals who are behaving dangerously and are at risk of harming themselves or others. As of June 2024, 21 states and the District of Columbia have passed ERPO-style bills into law (Johns Hopkins Bloomberg School of Public Health 2024 ). ERPOs fill an important policy gap because some individuals at risk of harming themselves and/or others, are legally able to purchase and possess firearms and cannot otherwise be disarmed. Therefore, ERPOs provide a mechanism for preventing firearm access (and potentially firearm violence) when an individual who represents a credible threat of violence is known but is not prohibited from accessing firearms by other legal mechanisms.
Research on ERPOs and their use and outcomes is in its infancy. Multiple studies have described characteristics of ERPO respondents and risk behaviors detailed in the applications in a single state or county ERPO (Barnard et al. 2021 ; Frattaroli et al. 2020 ; Pear et al. 2022 ; Rowhani-Rahbar et al. 2020 ; Swanson et al. 2019 , 2017 ; Zeoli et al. 2021 ). Few studies have examined outcomes, and those that have generally focus on suicide outcomes, with findings suggestive of a reduction in suicide risk when ERPOs are used (Swanson et al. 2019 , 2017 ; Miller et al. 2024 ) and an association at the state-level between ERPO law enactment and a reduction in firearm suicides (Kivisto and Phalen 2018 ). To our knowledge, this is the first multi-state ERPO study.
Here we describe the protocol we used to conduct a six-state study of ERPO case files designed to characterize ERPO petitions, petitioners and respondents (individual parties in the ERPO petition), court outcomes, and identify whether ERPOs are associated with reductions in suicide across geographically, demographically, and politically diverse states. The protocol described in this manuscript details (1) how we accessed ERPO case files in six states; (2) an explanation of the process of standardizing data from official records across the six states; (3) guidance for training research assistants (RAs) and maintaining consistent data abstraction practices across a multi-state, multi-institution RA team; and (4) strategies for reducing and responding to secondary trauma risk experienced by RAs as a result of reading ERPO narratives, which can include graphic descriptions of violence and crises.
During the 3-year project period (2020–2023), we conducted a multi-state study (Zeoli et al. 2022 ) of ERPO use with data from six states (California, Colorado, Connecticut, Florida, Maryland, and Washington). We selected these states for three reasons. First, all are engaged in efforts to implement ERPOs, and those implementation efforts are either yielding a critical mass of ERPO petitions filed or an informative implementation context. Second, these states are geographically and politically diverse, which may impact implementation and use. Third, we were able to access ERPO case files in the selected states. While ERPO statutes differ in some ways across the six states (Smart et al. 2020 ), all share a general process that involves a petition, court hearing, and court decision about whether to temporarily prohibit the individual named in the order from purchasing and possessing firearms.
ERPO court records are publicly available for all study states except Maryland. In the five states where ERPO data are public, we requested ERPO court records through public records searches or through agencies with access to these data. For California and Washington, ERPO case numbers and non-public identifying information such as respondent name, county, and ERPO date and type were first obtained from the Department of Justice (DOJ) (for California) and the Administrative Office of the Courts (for Washington) through a special request; this information was then used to request the publicly available court records from individual local and county courts throughout the two states.
In Colorado, a local team member contacted each county court to request ERPO records. In Connecticut, the ERPO statute (Connecticut General Assembly 2023 ) specifically requires the court to give notice of the court order to the Department of Mental Health and Addiction Services, and it is through these court notices (that have been maintained since 2013) that the study team accessed the public records. In Florida, we obtained most of the case files through Florida’s secure Comprehensive Case Information System (CCIS), a centralized database of court case information, which streamlined the process of accessing these publicly available records. For a few counties, we obtained the publicly available case files directly from the County Clerks of Court.
In Maryland, at the time of the study, ERPO records were restricted to select entities named in the statute (Brown 2022 ). Working with the Maryland Attorney General’s Office, we requested and obtained ERPO case files from District Courts throughout the State.
It should be noted that ERPO court records are often paper documents and may not be digitally accessible. This is true for California, Maryland, and Washington. Accessing paper copies of ERPO case files in these three states required a significant amount of time and coordination to collect the documents and scan and upload them to secure, password protected file storage systems housed at the collaborating universities in each state. The study teams in Colorado, Connecticut, and Florida gained access to digital copies of case files.
We requested ERPO case files for the time period beginning at ERPO enactment in each state through June 30, 2020 (see Table 1 ) with the exception of Connecticut, where the law took effect in 1999 but full ERPO case reports were only available beginning January 1, 2013. For California, the request process differed slightly. We first obtained identifying information on ERPO respondents through California DOJ and used that information to request the publicly available case files. However, due to California DOJ’s process of overwriting respondents’ older orders with newer orders in the primary file every 3 weeks, it is possible that, in the early days of collecting California’s ERPO case files, we missed cases when an individual was a respondent to more than one ERPO action. Once the California team learned of the California DOJ process in mid-2019, we started requesting ERPO case numbers and respondent identifying information from the California DOJ every 21 days so that we would not miss any order data due to the data overwriting process.
This effectively means we were unable to get case-level data for California prior to mid-2019 and therefore cannot distinguish the number of cases filed. Instead, the California data reflects the number of respondents from ERPO enactment through June 30, 2020, and the number of respondents for whom we coded cases for that timeframe. Additionally, in California, we received few requested case files from the court for cases involving only emergency ERPOs (i.e., those not followed by a temporary or final order) because these orders are granted remotely while the petitioning officer is in the field. As a result, they are typically filed at the local police station or sheriff’s office rather than the courthouse.
We abstracted data from all cases received from each state except Florida. In Florida, the large number of case files received (n = 4695) exceeded our available coding resources; therefore, we abstracted data from a random sample of 50% of cases from all counties with greater than 10 ERPO case files based on the case counts by the Office of the State Court Administrator (OSCA). Fifteen Florida counties had a small number (< 10) of cases based on OSCA counts, and we coded all of those. In total, RAs abstracted data from 6,628 ERPO case files (see Table 1 ) under the 10 domains listed in Table 2 (e.g., criminal legal system; firearm access and possession; and court decisions).
Training and coding procedures
The research team included investigators from nine universities, with members located in each selected state and two additional states. Starting with data collection instruments from two prior ERPO studies (Frattaroli et al. 2020 ; Zeoli et al. 2021 ), we collectively developed the data abstraction instrument for the project by comparing the data elements included on each state’s ERPO petition form and the ERPO eligibility criteria listed in each state’s statute against the existing instruments. This process was lengthy due to the vast differences in ERPO petition forms between, and sometimes within, states. The Principal Investigator (PI) and Co-PI curated a list of common and state-specific candidate abstraction variables and shared it with the state PIs and their teams. After the initial draft of the instrument was created, the PI and Co-PI added, removed, edited, and adjusted the items as necessary given feedback from the research team. Through a series of discussions, the multi-state team refined and finalized the list of data elements that comprised the final data collection instrument.
The goal was to create an instrument that would capture the data needed to understand ERPO use. The final instrument had robust sections related to suicide and interpersonal violence risk, among others (see Appendix A in Supplementary material). For suicide risk, we distinguished among ideation, threats, plans, aborted attempts, and attempts where data were available to disambiguate them. For interpersonal violence risk, we abstracted data on threats and uses of violence, separately, with queries capturing the target of the violence or threat. For both suicide and interpersonal violence risk, we captured whether any of the acts or threats of violence involved a firearm. We also included a variable to specify whether these risk behaviors were part of the event that motivated someone to file an ERPO petition (termed the “precipitating event”). Other sections of the data collection instrument specified the risk context of the situation and captured information about substance use, mental health, criminal history, firearm possession or access, and whether a respondent brandished a firearm. Finally, we included sections about ERPO court processes, whether the ERPO was granted, and whether firearms were removed.
State PIs had the option of adding state-specific variables to the instrument and in Maryland, California, and Connecticut, the PIs did. After agreeing on a good working draft of the instrument, we developed training materials that defined each variable and provided examples of coded excerpts from case files and guidance for abstracting the data that the entire research team reviewed, refined, and approved. We then programmed the data collection instrument in Qualtrics, an online survey software program to which all sites had access. Each state PI was then asked to abstract data from a small number of ERPO petitions from their state to ensure suitability of the instrument (the Maryland team was not able to complete this task due to not yet having access to their state’s ERPO casefiles). Feedback was then incorporated into the instrument.
Each state PI staffed their teams according to their state’s volume of ERPO cases. Due to the differences among state’s ERPO petitions and associated forms within the case files, and the need to include RAs on the Institutional Review Board protocol used by their state PIs, we initially planned for each RA to abstract data only from the state they were hired to staff. In practice, some RAs worked across states to manage the variation in access to case files during the study period. Having RAs who were able to code across states allowed us to keep RAs continuously coding even when files were not available in their home states. Specifically, RAs for Maryland and Florida were combined and coded Florida case files while we waited for access to Maryland case files. When Florida was completed, the RAs moved to code Maryland cases. Importantly, RAs coded only one state at a time to avoid introducing errors associated with switching between state case files and differing forms. The project employed 59 RAs over 17 months to code the 6415 cases.
RAs completed didactic training created by the two project PIs via an online learning management system. The training, a mix of videos, readings, and quizzes, included information about ERPOs, the study aims, the data collection instrument and associated definitions, the process for abstracting data, and information about strategies to reduce the risk and impact of secondary trauma. RAs completed the virtual training modules and passed the quizzes before advancing to practice coding two ERPO case files. After coding two case files, RAs participated in two one-hour synchronous sessions hosted by the project PIs to reinforce the online training, give them an opportunity to ask questions, and to review and discuss the test case coding. Once RAs completed these steps, they were cleared by the PIs to code.
The state PIs then trained RAs cleared for coding in the specifics of each state’s case files and variables. The California team held synchronous training sessions until questions had been resolved and RAs felt comfortable proceeding. For Florida and Maryland, RAs attended two virtual synchronous training sessions, one for each state’s ERPO process. In Colorado, RAs were trained using synchronous training sessions and participated in standing biweekly meetings to discuss abstraction issues and element definitions. For Connecticut, the PI developed a state-specific coding manual instructing RAs where to find data elements in the case files. In Washington, RAs were trained using synchronous training sessions and participated in standing weekly meetings to discuss abstraction discrepancies and definitional disagreements.
When coding began in earnest, the process for reaching reliability differed slightly from state to state, depending on the number of RAs and number of cases to be coded. In Washington, for example, a total of 10% of cases were randomly sampled and coded by all RAs to ensure reliability and consistency. In Colorado, 10% of cases were randomly sampled to be double-coded. In Florida, which had the largest number of cases, coding proceeded one county at a time, and RAs double-coded cases until they graduated to single-coder status. For RAs to graduate, they needed to achieve at least a 0.80 inter-rater reliability score. New RAs and those whose scores were below the target were paired with primary RAs (who had reached the 0.80 threshold) until they, too, reached 0.80.
Data quality and maintaining fidelity to the coding procedures
Because RAs generally coded one state (with the exception of Florida and Maryland RAs), we were unable to quantitatively test reliability of coding between states. Our multiple coding training procedures in which all RAs participated were designed to help ensure consistency. However, due to differences in ERPO documents across states and the lengthy duration of our coding period, it was possible that variations in understanding of variable definitions might have developed among state teams. To combat this possibility, the PI and Co-PI instituted systems to maintain coding pace and consistency among RAs.
Weekly videoconference check-in meetings were implemented, with RAs required to attend at least one meeting each week. Online moderated group chats were used to allow RAs to ask questions as they arose, tagging team members to alert them to the question, enabling them to get answers relatively quickly. The California, Florida, and Maryland teams kept a running document of frequently asked questions that all RAs across states could access during coding. The meetings and group chats served as forums to reinforce training, the coding instrument definitions, troubleshoot coding of complex cases, share consensus with RAs about larger coding questions raised in the online group chats, and develop an inclusive and communicative team dynamic. The check-in meetings and online group chats reduced the number of RA questions needing to be elevated to the PI and Co-PI, maintaining coding pace and consistency.
Prevention and reduction of secondary trauma
Due to the sometimes detailed and graphic descriptions of crises and violence contained in ERPO case files, there was a risk that RAs would experience secondary trauma through reading them. Secondary trauma, also called vicarious trauma, are the effects of indirect exposure to trauma (McCann and Pearlman 1990 ). For example, researchers have reported experiencing physical and emotional symptoms (e.g., sleeplessness, an increased awareness of safety) when conducting research on violence and suicide (Mckenzie et al. 2017 ; Campbell 2002 ). To minimize the risk of secondary trauma, we instituted protocols to limit RA exposure to cases when needed. For example, the protocol dictated that if an RA decided they could not code a specific case, for any reason, that case was reassigned, no questions asked. By guaranteeing we would not ask for an explanation as to why an RA could not code a case, we allowed them to switch out a case without sharing what might be personal information they did not want to disclose to their supervisors. We also encouraged RAs to shift to completing other study tasks when they needed a break from the intensity of coding. In this way, RAs could request time off from coding case files and shift to completing other research-related tasks until they were ready to re-engage with coding. Additionally, at the weekly check-in meetings, space was held to discuss how RAs were handling the emotional and psychological aspects of coding ERPO case files, cultivating an inclusive and communicative environment where RAs would be comfortable sharing with each other. Importantly, PIs and other meeting leads often began the meetings by sharing what they found emotionally difficult in specific cases to set the tone for the meetings and demonstrate that it is normal to be bothered by the case narratives being read.
Furthermore, the online coding training course completed by all RAs included a module on recognizing signs that might indicate secondary trauma and information on what to do when experiencing such symptoms. A licensed clinical social worker on staff with one of the state teams was available to RAs at some RA meetings and on call for individual appointments, should an RA need it. While the social worker did not establish a therapeutic relationship with RAs, they listened, made suggestions and indicated when it might be necessary to seek other resources to help with the psychological load of coding. Additionally, each state team developed a list of available resources (mainly through their universities, for whom the RAs worked) to which RAs could refer. While this research focused on the possibility that RAs might experience vicarious trauma due to their role in reading and abstracting data from the ERPO casefiles, it is important to recognize that even the most seasoned researcher can experience vicarious trauma and benefit from the steps detailed here.
By coordinating data collection on ERPO cases across states, we efficiently achieved greater explanatory power through pooled analyses and direct comparisons than would be possible if we had examined ERPO use in each of these states independently. Analyzing the breadth of violence risks and contexts in which the risks occur in ERPO case files requires attention to detail and standard data collection protocols to be in place and followed. Considering ERPO petitions describe the ways in which the respondent is at risk of harming themselves and/or others, and therefore can contain graphic descriptions of violence and threats (including mass shooting threats, suicide attempts, and domestic violence) conducting research about ERPOs carries risks of secondary trauma. This account of our processes can inform future firearm violence prevention research by providing a reference for how to undertake similar projects in terms of data acquisition, coding, data quality, and strategies to promote health wellness among RAs.
The study used cross-sectional administrative data. Relying on administrative data meant that the processes described are for coding data reported in the case files only. We did not seek out information beyond what was provided (typically solely from the petitioner's perspective) through the ERPO case files. We note that the structure and level of information available in the case files varied across and within states, as well as between petitioner types (law enforcement or civilian). Comparisons of ERPO use across states requires consideration of this variability. In states where law enforcement officers are the only authorized petitioners, information reported about respondents and precipitating events followed a relatively uniform reporting style, although the narrative style of these reports meant that the content was not uniformly consistent in relation to the data points to be abstracted. Where civilians, mainly family members and intimate partners, were authorized to petition, the presentation and type of information included in the petitions varied more significantly.
To our knowledge, this study is the first of its kind to analyze a multi-state sample of ERPOs. The process of standardizing information and abstracting data across states consistently to describe state-level ERPO implementation and assess impacts of the law offers researchers some insight into what such an undertaking involves and provides a foundation on which to interpret findings reported from the six-state study.
Availability of data and materials
A limited dataset generated from ERPO case files will be available at ICPSR upon publication of research from the multi-state study.
Abbreviations
- Extreme risk protection order
Research assistant
Department of Justice
Comprehensive case information system
Principal investigator
Barnard LM, McCarthy M, Knoepke CE, Kaplan S, Engeln J, Betz ME. Colorado’s first year of extreme risk protection orders. Injury Epidemiol. 2021;8(1):59. https://doi.org/10.1186/s40621-021-00353-7 .
Article Google Scholar
Brown AG. Maryland Public Information Act Manual (7th ed.). Office of the Attorney General; 2022. https://www.marylandattorneygeneral.gov/Pages/OpenGov/piamanual.aspx . Accessed 5 May 2023.
Campbell R. Emotionally involved: the impact of researching rape. Routledge; 2002.
Google Scholar
Centers for Disease Control and Prevention, National Center for Injury Prevention and Control. Web-based Injury statistics query and reporting system (WISQARS). www.cdc.gov/injury/wisqars . Accessed 5 May 2023.
Connecticut General Assembly (2023). General statutes of Connecticut: chapter 529* division of state police. https://www.cga.ct.gov/current/pub/chap_529.htm#sec_29-38c . Accessed 5 Feb 2024.
Frattaroli S, Omaki E, Molocznik A, Allchin A, Hopkins R, Shanahan S, Levinson A. Extreme risk protection orders in King County, Washington: the epidemiology of dangerous behaviors and an intervention response. Injury Epidemiol. 2020;7(1):44–9. https://doi.org/10.1186/s40621-020-00270-1 .
Johns Hopkins Bloomberg School of Public Health. Extreme risk protection order: A tool to save lives. https://americanhealth.jhu.edu/implementERPO . Accessed 1 Apr 2024.
Kivisto AJ, Phalen PL. Effects of risk-based firearm seizure laws in Connecticut and Indiana on suicide rates, 1981–2015. Psychiatr Serv. 2018;69(8):855–62. https://doi.org/10.1176/appi.ps.201700250 .
Article PubMed Google Scholar
McCann IL, Pearlman LA. Vicarious traumatization: A framework for understanding the psychological effects of working with victims. J Trauma Stress. 1990;3(1):131–49. https://doi.org/10.1007/BF00975140 .
Mckenzie SK, Li C, Jenkin G, Collings S. Ethical considerations in sensitive suicide research reliant on non-clinical researchers. Res Eth. 2017;13(3–4):173–83. https://doi.org/10.1177/1747016116649996 .
Miller M, Zhang Y, Studdert DM, Swanson S. Updated estimate of the number of extreme risk protection orders needed to prevent 1 suicide. JAMA Netw Open. 2024;7(6):e2414864. https://doi.org/10.1001/jamanetworkopen.2024.14864 .
Article PubMed PubMed Central Google Scholar
Pear VA, Pallin R, Schleimer JP, Tomsich E, Kravitz-Wirtz N, Shev AB, Knoepke CE, Wintemute GJ. Gun violence restraining orders in California, 2016–2018: case details and respondent mortality. Inj Prev. 2022;28(5):465–71. https://doi.org/10.1136/injuryprev-2022-044544 .
Rowhani-Rahbar A, Bellenger MA, Gibb L, Chesnut H, Lowry-Schiller M, Gause E, Haviland MJ, Rivara FP. Extreme risk protection orders in Washington: a statewide descriptive study. Ann Intern Med. 2020;173(5):342–9. https://doi.org/10.7326/M20-0594 .
Smart R, Morral AR, Smucker S, Cherney S, Schell TL, Peterson S, Ahluwalia SC, Cefalu M, Xenakis L, Ramchand R, Roan Gresenz C. The science of gun policy: a critical synthesis of research evidence on the effects of gun policies in the United States. 2nd ed. Santa Monica, CA: RAND Corporation; 2020. https://www.rand.org/pubs/research_reports/RR2088-1.html . Accessed 11 May 2023.
Swanson JW, Norko MA, Lin HJ, Alanis-Hirsch K, Frisman LK, Baranoski MV, Easter MM, Robertson AG, Swartz MS, Bonnie RJ. Implementation and effectiveness of Connecticut’s risk-based gun removal law: Does it prevent suicides? Law Contemp Probl. 2017;80(2):179–208.
Swanson JW, Easter MM, Alanis-Hirsch K, Belden MC, Norko MA, Robertson AG, Parker GF. Indiana’s experience with a risk-based gun seizure law: criminal justice and suicide outcomes. J Am Acad Psychiatry Law. 2019;47:188–97.
PubMed Google Scholar
Zeoli AM, Paruk J, Branas CC, Carter PM, Cunningham R, Heinze J, Webster DW. Use of extreme risk protection orders to reduce gun violence in Oregon. Criminol Public Policy. 2021;20:243–61. https://doi.org/10.1111/1745-9133.12544 .
Zeoli AM, Frattaroli S, Barnard L, Bowen A, Christy A, Easter M, Kapoor R, Knoepke C, Ma W, Molocznik A, Norko M, Omaki E, Paruk JK, Pear VA, Rowhani-Rahbar A, Schleimer JP, Swanson JW, Wintemute GJ. Extreme risk protection orders in response to threats of multiple victim/mass shooting in six U.S. states: a descriptive study. Prev Med. 2022;1:10.
Download references
Acknowledgements
We would like to acknowledge and thank our many esteemed research assistants for their dedication and hard work on this project. We could not have done this important work without you!
This project was supported by a grant from the National Collaborative on Gun Violence Research. The funder had no role in the science of the project. The views expressed in this manuscript are the authors’ and do not necessarily reflect the view of the National Collaborative on Gun Violence Research. The views expressed do not represent the Connecticut Department of Mental Health & Addiction Services or Yale University.
Author information
Authors and affiliations.
Institute for Firearm Injury Prevention, School of Public Health, University of Michigan, 1415 Washington Heights, Ann Arbor, MI, 48109, USA
April M. Zeoli
The Johns Hopkins Bloomberg School of Public Health, 415 N. Washington, Baltimore, MD, 21205, USA
Amy Molocznik, Elise Omaki & Shannon Frattaroli
New Jersey Gun Violence Research Center, School of Public Health, Rutgers University, 683 Hoes Lane, Piscataway, NJ, 08854, USA
Jennifer Paruk
Department of Emergency Medicine, University of Colorado, 12505 E. 16th Ave, Aurora, CO, 80045, USA
Marian E. Betz
College of Behavioral and Community Sciences, University of South Florida, 4202 E. Fowler Avenue, Tampa, FL, 33612, USA
Annette Christy
Department of Mental Health and Addiction Services, School of Medicine, Yale University, 333 Cedar Street, New Haven, CT, 06510, USA
Reena Kapoor & Michael A. Norko
University of Colorado Anschutz Medical Campus, 13001 East 17th Place, Aurora, CO, 80045, USA
Christopher Knoepke
College of Social Science, Michigan State University, 509 East Circle Drive, East Lansing, MI, 48824, USA
Davis School of Medicine, University of California, 2315 Stockton Blvd., Sacramento, CA, 95817, USA
Veronica A. Pear, Julia P. Schleimer & Garen J. Wintemute
School of Public Health, University of Washington, 3980 15th Avenue NE, Box 351616, Seattle, WA, 98195, USA
Ali Rowhani-Rahbar
Duke University School of Medicine, 2400 Pratt Street, Box 102505, Durham, NC, 27705, USA
Jeffrey W. Swanson
You can also search for this author in PubMed Google Scholar
Contributions
AMZ performed study conceptualization, investigation, methodology, formal analysis, supervision, data curation, funding acquisition, and was a major contributor in writing and editing the manuscript. AM performed data curation, supervision, project administration, and wrote, reviewed and edited the manuscript. JP performed study investigation, data curation, supervision, project administration, and was a major contributor in writing and editing the manuscript. EO performed data curation, supervision, project administration, and was a major contributor in writing and editing the manuscript. SF performed study conceptualization, investigation, methodology, formal analysis, supervision, data curation, funding acquisition, and was a major contributor in writing and editing the manuscript. MEB performed study investigation, data curation, supervision, project administration, and was a major contributor in writing and editing the manuscript. AC performed study investigation, data curation, supervision, project administration, contributed resources, and was a major contributor in writing and editing the manuscript. RK performed study investigation, data curation, supervision, project administration, and was a major contributor in writing and editing the manuscript. CK performed study investigation, data curation, supervision, and was a major contributor in writing and editing the manuscript. WM performed study investigation, data curation, data analysis, and was a major contributor in writing and editing the manuscript. MN performed study investigation, data curation, supervision, project administration, and was a major contributor in writing and editing the manuscript. VAP performed study investigation, data curation, supervision, project administration, and was a major contributor in writing and editing the manuscript. ARR performed study investigation, data curation, supervision, project administration, and was a major contributor in writing and editing the manuscript. JWS performed study investigation, data curation, and was a major contributor in writing and editing the manuscript. JPS performed study investigation, data curation, and was a major contributor in writing and editing the manuscript. GJW performed study investigation, data curation, and was a major contributor in writing and editing the manuscript. All authors read and approved the final manuscript.
Corresponding author
Correspondence to April M. Zeoli .
Ethics declarations
Ethics approval.
This protocol was approved by the Institutional Review Boards at Michigan State University, Yale University, the Connecticut Department of Mental Health and Addiction Services, the Johns Hopkins Bloomberg School of Public Health, University of Colorado Denver Anschutz Medical Campus, Duke University Health System, University of South Florida, University of California Davis, and University of Washington. The authors certify that the study was performed in accordance with the ethical standards as laid down in the 1964 Declaration of Helsinki and its later amendments or comparable ethical standards.
Consent to participate
Not applicable.
Consent for publication
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Authors following Frattaroli are listed alphabetically.
Supplementary Information
Supplementary material 1., rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ . The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated in a credit line to the data.
Reprints and permissions
About this article
Cite this article.
Zeoli, A.M., Molocznik, A., Paruk, J. et al. A multi-state evaluation of extreme risk protection orders: a research protocol. Inj. Epidemiol. 11 , 49 (2024). https://doi.org/10.1186/s40621-024-00535-z
Download citation
Received : 06 June 2024
Accepted : 29 August 2024
Published : 09 September 2024
DOI : https://doi.org/10.1186/s40621-024-00535-z
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Data management
- Secondary trauma
- Data abstraction
Injury Epidemiology
ISSN: 2197-1714
- General enquiries: [email protected]

IMAGES
VIDEO
COMMENTS
Requirements for Mitigating Research Risks. When assessing risk and benefits in a study, the IRB can support researchers in determining if a risk is justifiable or should be removed. Generally, risks to participants must be minimized, and any risks in the study should be reasonable when compared to the benefits of the study.
The computed risk is situated on the highest level in risks map. A software system for evaluating risks in e-testing research project was also developed. The research was funded by the Ministry of ...
The IRB will: Identify and compare the risks associated with the research from the risks of therapies or alternatives to participation in research. Determine that the risks will be minimized. Identify the anticipated benefits to be derived from the research. Determine that the risks are reasonable in relation to be benefits to subjects, if any ...
Understanding Risk in Research. Assessing risk in a research study is one of the primary responsibilities of an IRB and one of its most controversial tasks. By nature, studying human beings is a complicated process because the subject matter itself is complicated. The level of risk can vary because of many factors including: the population ...
Risk in Human Subjects Research. Risk is the probability of harm or injury (physical, psychological, social, legal or economic) occurring because of participation in a research study. Both the probability and magnitude (severity) of a possible harm may vary from minimal to significant. The magnitude of potential harm is the summative measure of ...
To simplify the process you can use the health and safety risk assessment templates, risk estimation tool and guidance for all risks associated with your research project. Please refer to the research risk estimation guidance under how to carry out a risk assessment below to assist you. Research risks. Typical risks that need to be considered ...
Psychological risks. Psychological risks include the production of negative affective states such as anxiety, depression, guilt, shock and loss of self-esteem and altered behavior. Sensory deprivation, sleep deprivation, use of hypnosis, deception or mental stresses are examples of psychological risks. Social/Economic risks.
This chapter tries to provide a way by which research participants can assess the risks of being involved in a particular research project. At the heart of the process will be the balance and a judgement made by the individual between the perceived benefits of the research and the possible risks. Uncertainty is a key word in the assessment of risk.
Definitions. Benefit A valued or desired outcome; an advantage. Risk The probability of harm or injury (physical, psychological, social, or economic) occurring as a result of participation in a research study. Both the probability and magnitude of possible harm may vary from minimal to significant. Federal regulations define only "minimal risk."
High-risk, high-reward research can break down barriers and bring diverse teams together, but some researchers are not cut out for life on the edge. "There is a self-selection of those ...
According to Hertati, Widiyanti,Syafarudin and Safkaur (2020), crises are defined as periods of disruptions that occur unexpectedly that cause a negative impact on organisations or the world ...
Once the risks associated with the research have been identified, the process of categorizing the risks as minimal or greater than minimal may begin. Two characteristics influence the nature of the risk: 1) the probability of harm; 2) the magnitude of harm. The magnitude of harm can be related to the severity, duration and reversibility of a ...
While risks associated with participation may not be expected, most protocols carry some risk. Consider the following: Information risks (e.g., loss of privacy and/or breach of confidentiality). Psychological or emotional risks (e.g., fear, stress, confusion, guilt, loss of self-esteem, depression, triggering of past emotional experiences).
A risk assessment determines the likelihood, consequences and tolerances of possible incidents. "Risk assessment is an inherent part of a broader risk management strategy to introduce control measures to eliminate or reduce any potential risk- related consequences." 1 The main purpose of risk assessment is to avoid negative consequences related to risk or to evaluate possible opportunities.
In human subjects research, research is categorized into two categories: Minimal risk; or; Greater than minimal risk; Research is considered minimal risk when the risks of the research are not greater than those experienced in regular daily life. Researchers are responsible for identifying any possible risks of the research and minimizing risks to subjects whenever possible.
INTRODUCTION. A favorable risk-benefit ratio is one of the fundamental requirements for ethical research involving humans (World Medical Association Citation 2013; CIOMS Citation 2016; The National Commission for the Protection of Human Subjects of Biomedical and Behavioral Research Citation 1979).In practice, this entails that research ethics committees (RECs) have to ensure that "risks to ...
A project risk assessment is a formal effort to identify and analyze risks that a project faces. First, teams identify all possible project risks. Next, they determine the likelihood and potential impact of each risk. During a project risk assessment, teams analyze both positive and negative risks. Negative risks are events that can derail a ...
When you know the potential risks for each project, you can create reasonable project objectives and keep the team on track. In the guide below, we'll outline the seven most common project risks you may encounter when conducting risk assessments. Create a risk register template. 1. Scope creep.
A risk may be serious or significant because it has a probability (even a low probability) of great harm (e.g., a low probability of death), or because it has a high probability of slight harm (e.g., a near certainty of physical discomfort or psychological distress). The risks of participation in research may be part of the research design or ...
Two schools of risk analysis: A review of past research on project risk. Project Management Journal, 42(4), 5-18. Crossref. Google Scholar. Biographies. Stuart D. Green is a professor in the School of the Built Environment at the University of Reading, UK. He has a bachelor's degree from the University of Birmingham (UK), a master's ...
This JAMA Guide to Statistics and Methods article discusses accounting for competing risks in clinical research. [Skip to Navigation] Our website uses cookies to enhance your experience. ... An example is time from study entry to death. A competing risk is an event whose occurrence precludes the occurrence of the primary event of interest. In a ...
The nationwide grassroots network increased its funding package by more than 30% over last year, the nonprofit noted in a press release announcing the new research grant recipients. Research areas range from brain changes behind cognitive impairment to genetic causes of Parkinson's, to health disparities among underrepresented patient communities. . Other projects will seek to discover new ...
Background Extreme Risk Protection Orders (ERPOs) are civil court orders that prohibit firearm purchase and possession when someone is behaving dangerously and is at risk of harming themselves and/or others. As of June 2024, ERPOs are available in 21 states and the District of Columbia to prevent firearm violence. This paper describes the design and protocol of a six-state study of ERPO use ...