

Cyber Security Business Plan Template
Written by Dave Lavinsky

Over the past 20+ years, we have helped over 500 entrepreneurs and business owners create business plans to start and grow their cyber security companies.
If you’re unfamiliar with creating a cyber security business plan, you may think creating one will be a time-consuming and frustrating process. For most entrepreneurs it is, but for you, it won’t be since we’re here to help. We have the experience, resources, and knowledge to help you create a great business plan.
In this article, you will learn some background information on why business planning is important. Then, you will learn how to write a cyber security business plan step-by-step so you can create your plan today.
Download our Ultimate Business Plan Template here >
What is a Cyber Security Business Plan?
A business plan provides a snapshot of your cyber security business as it stands today, and lays out your growth plan for the next five years. It explains your business goals and your strategies for reaching them. It also includes market research to support your plans.
Why You Need a Business Plan for a Cyber Security Company
If you’re looking to start a cyber security business or grow your existing cyber security company, you need a business plan. A business plan will help you raise funding, if needed, and plan out the growth of your cyber security business to improve your chances of success. Your cyber security business plan is a living document that should be updated annually as your company grows and changes.
Sources of Funding for cyber security Businesses
With regard to funding, the main sources of funding for a cyber security business are personal savings, credit cards, bank loans, and angel investors. When it comes to bank loans, banks will want to review your business plan and gain confidence that you will be able to repay your loan and interest. To acquire this confidence, the loan officer will not only want to ensure that your financials are reasonable, but they will also want to see a professional plan. Such a plan will give them the confidence that you can successfully and professionally operate a business. Personal savings and bank loans are the most common funding paths for cyber security companies.
Finish Your Business Plan Today!
How to write a business plan for a cyber security business.
If you want to start a cyber security business or expand your current one, you need a business plan. The guide below details the necessary information for how to write each essential component of your cyber security business plan.
Executive Summary
Your executive summary provides an introduction to your business plan, but it is normally the last section you write because it provides a summary of each key section of your plan.
The goal of your executive summary is to quickly engage the reader. Explain to them the kind of cyber security business you are running and the status. For example, are you a startup, do you have a cyber security business that you would like to grow, or are you operating a chain of cyber security businesses?
Next, provide an overview of each of the subsequent sections of your plan.
- Give a brief overview of the cyber security industry.
- Discuss the type of cyber security business you are operating.
- Detail your direct competitors. Give an overview of your target customers.
- Provide a snapshot of your marketing strategy. Identify the key members of your team.
- Offer an overview of your financial plan.
Company Overview
In your company overview, you will detail the type of cyber security business you are operating.
For example, you might specialize in one of the following types of cyber security businesses:
- Remote security center services : This type of cyber security is focused on providing comprehensive security for networks and devices remotely from a main control center.
- Cloud security services . As more businesses turn to storage in cloud platforms, this type of service protects the data of clients from being utilized by others in that platform.
- Vulnerability scan & management: This service screens client devices and network systems remotely on a monthly maintenance basis.
- Endpoint security services: This service is dedicated to the mobile and end user devices in corporate offices; protection for computers is not included.
In addition to explaining the type of cyber security business you will operate, the company overview needs to provide background on the business.
Include answers to questions such as:
- When and why did you start the business?
- What milestones have you achieved to date? Milestones could include the number of security breaches determined, the amount of revenue earned, or reaching X number of clients served, etc.
- Your legal business Are you incorporated as an S-Corp? An LLC? A sole proprietorship? Explain your legal structure here.
Industry Analysis
In your industry or market analysis, you need to provide an overview of the cyber security industry.
While this may seem unnecessary, it serves multiple purposes.
First, researching the cyber security industry educates you. It helps you understand the market in which you are operating.
Secondly, market research can improve your marketing strategy, particularly if your analysis identifies market trends.
The third reason is to prove to readers that you are an expert in your industry. By conducting the research and presenting it in your plan, you achieve just that.
The following questions should be answered in the industry analysis section of your cyber security business plan:
- How big is the cyber security industry (in dollars)?
- Is the market declining or increasing?
- Who are the key competitors in the market?
- Who are the key suppliers in the market?
- What trends are affecting the industry?
- What is the industry’s growth forecast over the next 5 – 10 years?
- What is the relevant market size? That is, how big is the potential target market for your cyber security business? You can extrapolate such a figure by assessing the size of the market in the entire country and then applying that figure to your local population.
Customer Analysis
The customer analysis section of your cyber security business plan must detail the customers you serve and/or expect to serve.
The following are examples of customer segments: government contractors, for-profit corporations, securities businesses, private security services, and individuals.
As you can imagine, the customer segment(s) you choose will have a great impact on the type of cyber security business you operate. Clearly, government contractors would respond to different marketing promotions than individuals, for example.
Try to break out your target customers in terms of their demographic and psychographic profiles. With regards to demographics, including a discussion of the ages, genders, locations, and income levels of the potential customers you seek to serve.
Psychographic profiles explain the wants and needs of your target customers. The more you can recognize and define these needs, the better you will do in attracting and retaining your customers.
Finish Your Cyber Security Business Plan in 1 Day!
Don’t you wish there was a faster, easier way to finish your business plan?
With Growthink’s Ultimate Business Plan Template you can finish your plan in just 8 hours or less!
Competitive Analysis
Your competitive analysis should identify the indirect and direct competitors your business faces and then focus on the latter.
Direct competitors are other cyber security businesses.
Indirect competitors are other options that customers have to purchase from that aren’t directly competing with your product or service. Software companies, home or office hardware, and remote alarm services may be examples of indirect competitors. You will want to mention any direct competition, as well.
For each direct competitor, provide an overview of their business and document their strengths and weaknesses. Unless you once worked at your competitors’ businesses, it will be impossible to know everything about them. But you should be able to find out key things about them such as
- What types of customers do they serve?
- What type of cyber security business are they?
- What is their pricing (premium, low, etc.)?
- What are they good at?
- What are their weaknesses?
With regard to the last two questions, think about your answers from the customers’ perspective. And, don’t be afraid to ask your competitors’ customers what they like most and least about them.
The final part of your competitive analysis section is to document your areas of competitive advantage. For example:
- Will you provide discounts for major government contractors?
- Will you offer scan protection and management that your competition doesn’t?
- Will you provide better customer service?
- Will you offer better pricing?
Think about ways you will outperform your competition and document them in this section of your plan.
Finish Your Business Plan Today!
Marketing plan.
Traditionally, a marketing plan includes the four P’s: Product, Price, Place, and Promotion. For a cyber security business plan, your marketing strategy should include the following:
Product : In the product section, you should reiterate the type of cyber security company that you documented in your company overview. Then, detail the specific products or services you will be offering. For example, will you provide in-person and remote cyber security services for major corporations or will you offer compliance solutions for select clients?
Price : Document the prices you will offer and how they compare to your competitors. Essentially in the product and price sub-sections of your plan, you are presenting the products and/or services you offer and their prices.
Place : Place refers to the site of your cyber security company. Document where your company is situated and mention how the site will impact your success. For example, is your cyber security business located in a professional business district, a quiet corporate area, a standalone building or a remote, unnamed location? Discuss how your site might be the ideal location for your customers.
Promotions : The final part of your cyber security marketing plan is where you will document how you will drive potential customers to your location(s). The following are some promotional methods you might consider:
- Advertise in trade magazines
- Reach out to websites
- Engage in email marketing
- Advertise on social media platforms
- Improve the SEO (search engine optimization) on your website for targeted keywords
Operations Plan
While the earlier sections of your business plan explained your goals, your operations plan describes how you will meet them. Your operations plan should have two distinct sections as follows.
Everyday short-term processes include all of the tasks involved in running your cyber security business, including answering calls, planning and providing scan management, responding to emergency situations, billing clients and assisting with computer equipment, etc.
Long-term goals are the milestones you hope to achieve. These could include the dates when you expect to book your Xth client, or when you hope to reach $X in revenue. It could also be when you expect to expand your cyber security business to a new city.
Management Team
To demonstrate your cyber security business’ potential to succeed, a strong management team is essential. Highlight your key players’ backgrounds, emphasizing those skills and experiences that prove their ability to grow a company.
Ideally, you and/or your team members have direct experience in managing cyber security businesses. If so, highlight this experience and expertise. But also highlight any experience that you think will help your business succeed.
If your team is lacking, consider assembling an advisory board. An advisory board would include 2 to 8 individuals who would act as mentors to your business. They would help answer questions and provide strategic guidance. If needed, look for advisory board members with experience in managing a cyber security business or successfully running a data management business.
Financial Plan
Your financial plan should include your 5-year financial statement broken out both monthly or quarterly for the first year and then annually. Your financial statements include your income statement, balance sheet, and cash flow statements.
Income Statement
An income statement is more commonly called a Profit and Loss statement or P&L. It shows your revenue and then subtracts your costs to show whether you turned a profit or not.
In developing your income statement, you need to devise assumptions. For example, will you increase customer retention by 20% quarterly, offer reduced pricing for hardware maintenance contracts, or offer discounted packaged pricing for multiple services? And will sales grow by 2% or 10% per year? As you can imagine, your choice of assumptions will greatly impact the financial forecasts for your business. As much as possible, conduct research to try to root your assumptions in reality.
Balance Sheets
Balance sheets show your assets and liabilities. While balance sheets can include much information, try to simplify them to the key items you need to know about. For instance, if you spend $50,000 on building out your cyber security business, this will not give you immediate profits. Rather it is an asset that will hopefully help you generate profits for years to come. Likewise, if a lender writes you a check for $50,000, you don’t need to pay it back immediately. Rather, that is a liability you will pay back over time.
Cash Flow Statement
Your cash flow statement will help determine how much money you need to start or grow your business, and ensure you never run out of money. What most entrepreneurs and business owners don’t realize is that you can turn a profit but run out of money and go bankrupt.
When creating your Income Statement and Balance Sheets be sure to include several of the key costs needed in starting or growing a cyber security business:
- Cost of computer and software equipment
- Payroll or salaries paid to staff
- Business insurance
- Other start-up expenses (if you’re a new business) like legal expenses, permits, furnishings and travel expenses
Attach your full financial projections in the appendix of your plan along with any supporting documents that make your plan more compelling. For example, you might include the cyber security credentials of the CEO and COO or a list of client contracts.
Writing a business plan for your cyber security business is a worthwhile endeavor. If you follow the template above, by the time you are done, you will truly be an expert. You will understand the cyber security industry, your competition, and your customers. You will develop a marketing strategy and will understand what it takes to launch and grow a successful cyber security business.
Don’t you wish there was a faster, easier way to finish your Cyber Security business plan?
OR, Let Us Develop Your Plan For You
Since 1999, Growthink has developed business plans for thousands of companies who have gone on to achieve tremendous success.
Click here to see how a Growthink business planning consultant can create your business plan for you.
Other Helpful Business Plan Articles & Templates

Cybersecurity Business Plan Template
Written by Dave Lavinsky
Cybersecurity Business Plan
You’ve come to the right place to create your Cybersecurity business plan.
We have helped over 1,000 entrepreneurs and business owners create business plans and many have used them to start or grow their Cybersecurity businesses.
Below is a template to help you create each section of your Cybersecurity business plan.
Executive Summary
Business overview.
The Cyber Guardian business is a startup cybersecurity company located in Burlingame, California. The company was founded by Lynn Frederick, who has a fifteen-year history working in the cybersecurity industry, in increasingly responsible roles. This expertise positions him to start and effectively grow a successful cybersecurity company. Lynn believes his coding and managerial experience, coupled with a deep knowledge of cybersecurity practices will provide everything needed for long-term growth and profitability.
Cyber Guardian is a cutting-edge cybersecurity startup dedicated to providing robust cybersecurity solutions to small and medium enterprises (SMEs). Founded by cybersecurity expert Lynn Frederick, Cyber Guardian leverages advanced technologies and deep industry experience to protect clients’ digital assets.
Product Offering
The following are the services that Cyber Guardian will provide:
- Vulnerability Assessment
- Managed Security Services
- Incident Response
- Cybersecurity Training & Awareness
Customer Focus
The primary customers of Cyber Guardian are SMEs across various sectors such as finance, healthcare, and retail, which are increasingly vulnerable to cyber threats but often lack the resources to maintain a full-fledged internal cybersecurity team.
Management Team
Cyber Guardian is owned and operated by Lynn Frederick, who graduated from UC Berkely with a bachelor’s degree in Software Security. Since his graduation, Lynn has been working at a large cybersecurity company in increasingly responsible roles. Lynn’s knowledge, skill, and customer service orientation prompted several customers to encourage him to launch his own company, stating they trust him above all others, and would follow him to the new firm. As he considered starting his own company, Lynn began securing contracts from these clients, ensuring they will follow him to Cyber Guardian when the company fully launches.
Lynn Frederick has recruited Gloria Perlman, who also attended UC Berkeley, to be the Administrative Manager in the new company. In this role, Gloria will oversee and direct staff members in the execution of the company vision, as well as run the back office operation and bookkeeping.
Success Factors
Cyber Guardian will be able to achieve success by offering the following competitive advantages:
- Friendly, knowledgeable, and highly-qualified team of IT professionals
- Services that leverage cutting-edge technology and techniques for maintaining security
- Cyber Guardian offers the best pricing in town, with a comparatively cost effective pricing structure.
Financial Highlights
Cyber Guardian is seeking $175,000 in debt financing to launch its cybersecurity operation. The funding will be dedicated toward securing the office space and purchasing technology and setting up the necessary infrastructure. Funding will also be dedicated toward three months of overhead costs to include payroll of the staff, rent, and marketing costs for the print ads and marketing costs. The breakout of the funding is below:
- Office space build-out: $10,000
- Technology and infrastructure: $50,000
- Three months of overhead expenses (payroll, rent, utilities): $100,000
- Marketing costs: $5,000
- Working capital: $10,000
The following graph outlines the financial projections for Cyber Guardian.
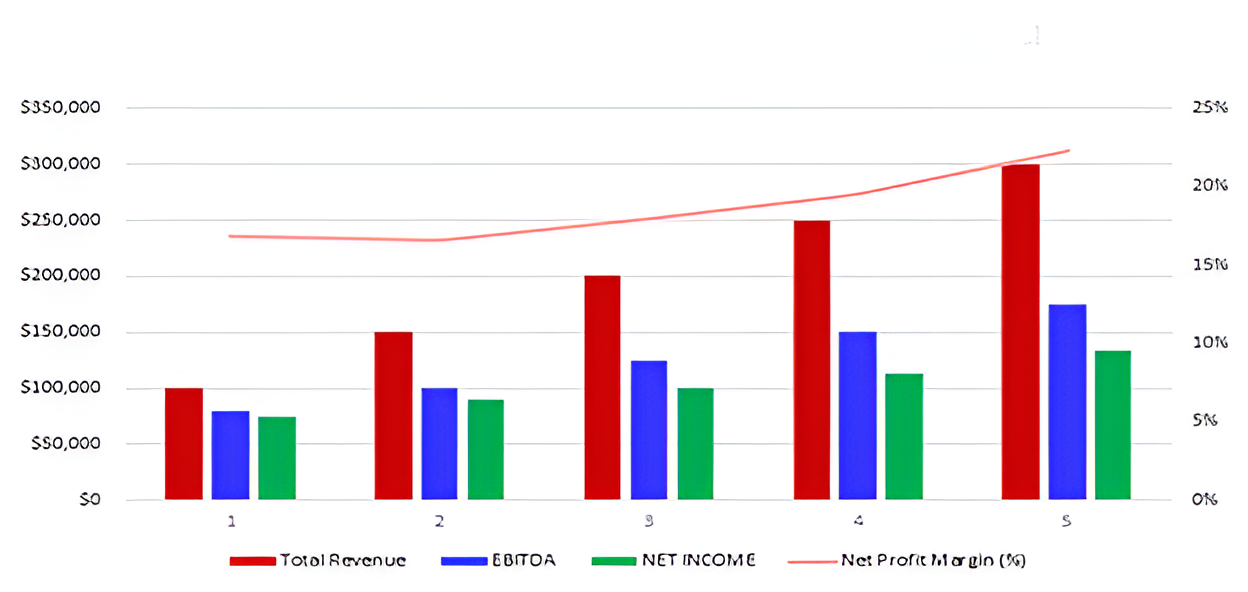
Company Overview
Who is cyber guardian.
Cyber Guardian is a newly established, full-service cybersecurity company in Burlingame, California. Cyber Guardian will be the most reliable, cost-effective, and efficient cybersecurity choice in the city and the surrounding communities. Cyber Guardian will provide a tailored menu of cybersecurity solutions designed to protect SMEs from the growing threats of cyberattacks, ensuring business continuity and regulatory compliance.
Lynn Frederick will serve as manager and mentor to each of his team members, all of whom are highly qualified in their own right, and experienced in the most important aspects of cybersecurity. Cyber Guardian offers peace of mind for all its clients and ensures all issues are taken care of expeditiously while delivering the best customer service.
Cyber Guardian History
Cyber Guardian is owned and operated by Lynn Frederick. As a former cybersecurity manager for several years, he developed a unique capability to design and implement cybersecurity solutions that clearly reflect his skills and abilities. The company is built on the foundation of its founder’s extensive industry expertise and a deep understanding of the cybersecurity challenges faced by SMEs. Furthermore, Lynn Frederick has gained the trust and commitment of several clients in advance of opening his business and has begun to sign contracts with each to provide tailored cybersecurity solutions once the company launches.
Since incorporation, Cyber Guardian has achieved the following milestones:
- Registered Cyber Guardian, LLC to transact business in the state of California.
- Has a contract in place for a 10,000 square foot office at one of the midtown buildings
- Reached out to numerous contacts to include Cyber Guardian in upcoming advertising and marketing programs.
- Began recruiting a staff of experienced IT professionals to work at Cyber Guardian
Cyber Guardian Services
Cyber Guardian offers end-to-end security services, from risk assessments and monitoring to incident response and recovery, alongside continuous updates and training to cope with evolving threats.
The following will be the services Cyber Guardian will provide:
- Performance reports and analytics: weekly reports to clients
- Superior day to day client management
Industry Analysis
The cybersecurity market is growing due to increasing internet penetration, a surge in cybercrime, and stringent regulatory requirements. The demand for cybersecurity solutions is expected to rise, especially among SMEs, which are typically less well-protected.
The cybersecurity industry is expected to reach $78.3 billion this year, and continue to grow at an annual rate of 7.7% over the next five years.
Cybersecurity is becoming increasingly important, as companies, governments, and individuals are more and more reliant on IT systems, which are vulnerable to malicious actions. This digital transformation has made security a priority for organizations of every size.
The cybersecurity software industry is growing due to increasing threats of hacking and malware. Rising sales, limited costs and a reliance on skilled labor have contributed to strong profits. Developers invest heavily in research and development to stay ahead of the game. Purchases costs vary depending on the developer, but are diminishing as cloud computing limits the need for hardware.
Customer Analysis
Demographic profile of target market.
Cyber Guardian will target companies that currently utilize cybersecurity and those that have a need for cybersecurity in Burlingame, California and, in the greater San Francisco region. The company will target small-to-medium sized businesses who have not yet acquired cybersecurity, as well as larger corporations without an effective cybersecurity solution.
| Total | Percent | |
|---|---|---|
| Total population | 1,680,988 | 100% |
| Male | 838,675 | 49.9% |
| Female | 842,313 | 50.1% |
| 20 to 24 years | 114,872 | 6.8% |
| 25 to 34 years | 273,588 | 16.3% |
| 35 to 44 years | 235,946 | 14.0% |
| 45 to 54 years | 210,256 | 12.5% |
| 55 to 59 years | 105,057 | 6.2% |
| 60 to 64 years | 87,484 | 5.2% |
| 65 to 74 years | 116,878 | 7.0% |
| 75 to 84 years | 52,524 | 3.1% |
Customer Segmentation
Cyber Guardian will primarily target the following customer profiles in the Bay Area:
- Finance SMEs: High-value transactions and regulatory compliance needs.
- Healthcare SMEs: Require protection of sensitive patient data.
- Retail SMEs: Need to secure consumer data and e-commerce platforms.
Competitive Analysis
Direct and indirect competitors.
Cyber Guardian will face competition from other companies with similar business profiles. A description of each competitor company is below.
IT Partners
Established in 2000, IT Partners is an IT managed services company that provides managed IT services throughout North America. IT Partners is equipped to offer a comprehensive range of IT solutions for businesses of all sizes. Solutions include cloud computing solutions, cybersecurity defense, network design and implementation, critical incident response, and 24/7 help desk support. The company uses a proactive approach to focus on prevention and designs customized strategies tailored to each client’s specific requirements and goals. IT Partners has over 250 IT professionals on its team and has served over 1,900 businesses. The company provides solutions for various industries, including accounting, architecture, engineering, construction, education, finance, healthcare, hospitality, insurance, legal, manufacturing, retail, recruiting/staffing, real estate, and non-profits.
Service Offerings Include:
- Managed IT Services
- Internal IT Support
- Virtual CIO
- Network Management
- Cybersecurity Protection
- Backup Monitoring/Remediation
- Device Management
- Patch Management
- Cloud Solutions
- Delmiaworks Support (IQMS)
- Amazon Web Services (AWS Cloud services, AWS Cloud migration, AWS managed cloud, AWS application modernization, AWS serverless architecture)
Bay Area Technology Solutions
Established in 1996, Bay Area Technology Solutions (BATS) is an IT services company that specializes in IT support and cybersecurity solutions for Bay Area businesses. BATS employs a team of highly credentialed technology professionals with expertise in a wide range of services, from remote help desk to on-site support, storage, server consolidation, virtualization, wireless, business continuity, archiving, POS systems, cybersecurity, and data center builds.
- Cybersecurity Services
- Application Support & Development
- Voice over IP (VoIP) Services
Miklos Technologies
Established in 1997, Miklos Technologies (Miklos IT) is a managed IT services company that serves businesses throughout the United States. Miklos IT supports numerous industries, including healthcare, logistics, finance, professional services, manufacturing, real estate, retail, ecommerce, construction, engineering, architecture, legal, private equity, education, non-profit, science, hospitality, and entertainment companies. Miklos IT provides four key service areas: technology consulting, IT, software, and marketing. The company offers business and technology consulting in various areas such as business transformation, growth & strategy planning, IT regulation compliances, mergers & acquisitions, technology risk assessments, operations, marketing brand strategy, sales, and recruiting & staffing.
- Managed IT Services & Security
- Software Development
- Ecommerce & Custom Websites
- Digital Marketing
- IT Consulting
- Support & Advance Custom Software
- Cybersecurity
- Systems Integration
- Cloud Computing & Migrations
Competitive Advantage
Cyber Guardian will be able to offer the following advantages over their competition:
- Friendly, knowledgeable, and highly-qualified team of experienced IT professionals
- Comprehensive menu of personalized, SME-focused solutions
- Cyber Guardian offers flexible pricing models designed to cater to the specific needs of smaller businesses.
Marketing Plan
Brand & value proposition.
Cyber Guardian will offer a unique value proposition to its clientele:
- Highly-qualified team of skilled employees who are able to provide a comprehensive cybersecurity program that brings peace of mind to their clients
- Experience with keeping abreast of evolving threats and security issues
- Flexible pricing models
Promotions Strategy
The promotions strategy for Cyber Guardian is as follows:
Word of Mouth/Referrals
The founder of Cyber Guardian has built an extensive list of contacts over the years by providing exceptional service and highly skilled and effective cybersecurity services. Many of these contacts and clients will follow the founder to the new company and help spread the word of Cyber Guardian.
Professional Associations and Networking
Industry associations and local networking will become a top priority for the team at Cyber Guardian. The management team will seek active leadership roles, which will expand its credibility within the industry.
Social Media Marketing
Cyber Guardian will focus primarily on marketing its services and on maximizing relationship opportunities via social media efforts.
Website/SEO Marketing
Cyber Guardian’s website will be well organized, informative, and list all the services that Cyber Guardian provides. Further, the company will engage in SEO marketing tactics so that anytime someone searches online for “cybersecurity company” or “cybersecurity company near me,” Cyber Guardian will be listed at the top of the search results.
Operations Plan
The following will be the operations plan for Cyber Guardian. Operation Functions:
- Lynn Frederick will be the owner and President of the company. He will manage client relations. Lynn Frederick has spent the past year recruiting the following staff:
- Gloria Perlman will be the Administrative Manager, and will oversee and direct staff members in the execution of the company vision, as well as run the back office operation and bookkeeping.
Milestones:
Cyber Guardian will have the following milestones completed in the next six months.
- 5/1/202X – Finalize contract to lease office space
- 5/15/202X – Finalize personnel and staff employment contracts for Cyber Guardian
- 6/1/202X – Finalize contracts for Cyber Guardian clients
- 6/15/202X – Begin networking at industry events
- 6/22/202X – Begin moving into Cyber Guardian office
- 7/1/202X – Cyber Guardian opens its doors for business
Financial Plan
Key revenue & costs.
The revenue drivers for Cyber Guardian are the fees charged for deployed solutions. Strong growth and a recurring revenue model, with client bases growing to generate a consistent revenue stream, also support profitability.
The cost drivers will be the overhead costs required to staff Cyber Guardian. The expenses will be the payroll cost, rent, utilities, technology and software costs.
Funding Requirements and Use of Funds
Key assumptions.
The following outlines the key assumptions required achieve the revenue and cost numbers in the financials and in order to pay off the startup business loan.
- Number of clients Per Month: 20
- Average revenue per Month: $200,000
- Office Lease per Year: $100,000
Financial Projections
Income statement.
| FY 1 | FY 2 | FY 3 | FY 4 | FY 5 | ||
|---|---|---|---|---|---|---|
| Revenues | ||||||
| Total Revenues | $360,000 | $793,728 | $875,006 | $964,606 | $1,063,382 | |
| Expenses & Costs | ||||||
| Cost of goods sold | $64,800 | $142,871 | $157,501 | $173,629 | $191,409 | |
| Lease | $50,000 | $51,250 | $52,531 | $53,845 | $55,191 | |
| Marketing | $10,000 | $8,000 | $8,000 | $8,000 | $8,000 | |
| Salaries | $157,015 | $214,030 | $235,968 | $247,766 | $260,155 | |
| Initial expenditure | $10,000 | $0 | $0 | $0 | $0 | |
| Total Expenses & Costs | $291,815 | $416,151 | $454,000 | $483,240 | $514,754 | |
| EBITDA | $68,185 | $377,577 | $421,005 | $481,366 | $548,628 | |
| Depreciation | $27,160 | $27,160 | $27,160 | $27,160 | $27,160 | |
| EBIT | $41,025 | $350,417 | $393,845 | $454,206 | $521,468 | |
| Interest | $23,462 | $20,529 | $17,596 | $14,664 | $11,731 | |
| PRETAX INCOME | $17,563 | $329,888 | $376,249 | $439,543 | $509,737 | |
| Net Operating Loss | $0 | $0 | $0 | $0 | $0 | |
| Use of Net Operating Loss | $0 | $0 | $0 | $0 | $0 | |
| Taxable Income | $17,563 | $329,888 | $376,249 | $439,543 | $509,737 | |
| Income Tax Expense | $6,147 | $115,461 | $131,687 | $153,840 | $178,408 | |
| NET INCOME | $11,416 | $214,427 | $244,562 | $285,703 | $331,329 |
Balance Sheet
| FY 1 | FY 2 | FY 3 | FY 4 | FY 5 | ||
|---|---|---|---|---|---|---|
| ASSETS | ||||||
| Cash | $154,257 | $348,760 | $573,195 | $838,550 | $1,149,286 | |
| Accounts receivable | $0 | $0 | $0 | $0 | $0 | |
| Inventory | $30,000 | $33,072 | $36,459 | $40,192 | $44,308 | |
| Total Current Assets | $184,257 | $381,832 | $609,654 | $878,742 | $1,193,594 | |
| Fixed assets | $180,950 | $180,950 | $180,950 | $180,950 | $180,950 | |
| Depreciation | $27,160 | $54,320 | $81,480 | $108,640 | $135,800 | |
| Net fixed assets | $153,790 | $126,630 | $99,470 | $72,310 | $45,150 | |
| TOTAL ASSETS | $338,047 | $508,462 | $709,124 | $951,052 | $1,238,744 | |
| LIABILITIES & EQUITY | ||||||
| Debt | $315,831 | $270,713 | $225,594 | $180,475 | $135,356 | |
| Accounts payable | $10,800 | $11,906 | $13,125 | $14,469 | $15,951 | |
| Total Liability | $326,631 | $282,618 | $238,719 | $194,944 | $151,307 | |
| Share Capital | $0 | $0 | $0 | $0 | $0 | |
| Retained earnings | $11,416 | $225,843 | $470,405 | $756,108 | $1,087,437 | |
| Total Equity | $11,416 | $225,843 | $470,405 | $756,108 | $1,087,437 | |
| TOTAL LIABILITIES & EQUITY | $338,047 | $508,462 | $709,124 | $951,052 | $1,238,744 |
Cash Flow Statement
| FY 1 | FY 2 | FY 3 | FY 4 | FY 5 | ||
|---|---|---|---|---|---|---|
| CASH FLOW FROM OPERATIONS | ||||||
| Net Income (Loss) | $11,416 | $214,427 | $244,562 | $285,703 | $331,329 | |
| Change in working capital | ($19,200) | ($1,966) | ($2,167) | ($2,389) | ($2,634) | |
| Depreciation | $27,160 | $27,160 | $27,160 | $27,160 | $27,160 | |
| Net Cash Flow from Operations | $19,376 | $239,621 | $269,554 | $310,473 | $355,855 | |
| CASH FLOW FROM INVESTMENTS | ||||||
| Investment | ($180,950) | $0 | $0 | $0 | $0 | |
| Net Cash Flow from Investments | ($180,950) | $0 | $0 | $0 | $0 | |
| CASH FLOW FROM FINANCING | ||||||
| Cash from equity | $0 | $0 | $0 | $0 | $0 | |
| Cash from debt | $315,831 | ($45,119) | ($45,119) | ($45,119) | ($45,119) | |
| Net Cash Flow from Financing | $315,831 | ($45,119) | ($45,119) | ($45,119) | ($45,119) | |
| Net Cash Flow | $154,257 | $194,502 | $224,436 | $265,355 | $310,736 | |
| Cash at Beginning of Period | $0 | $154,257 | $348,760 | $573,195 | $838,550 | |
| Cash at End of Period | $154,257 | $348,760 | $573,195 | $838,550 | $1,149,286 |
Cybersecurity Business Plan FAQs
What is a cybersecurity business plan.
A cybersecurity business plan is a plan to start and/or grow your cybersecurity business. Among other things, it outlines your business concept, identifies your target customers, presents your marketing plan and details your financial projections. You can easily complete your Cybersecurity business plan using our Cybersecurity Business Plan Template here .
What are the Main Types of Cybersecurity Businesses?
There are a number of different kinds of cybersecurity businesses, some examples include: Remote security center services, Cloud security services, Vulnerability scan & management, and Endpoint security services.
How Do You Get Funding for Your Cybersecurity Business Plan?
Cybersecurity businesses are often funded through small business loans. Personal savings, credit card financing and angel investors are also popular forms of funding.
What are the Steps To Start a Cybersecurity Business?
Starting a cybersecurity business can be an exciting endeavor. Having a clear roadmap of the steps to start a business will help you stay focused on your goals and get started faster. 1. Develop A Cybersecurity Business Plan - The first step in starting a business is to create a detailed cybersecurity business plan that outlines all aspects of the venture. This should include potential market size and target customers, the services or products you will offer, pricing strategies and a detailed financial forecast. 2. Choose Your Legal Structure - It's important to select an appropriate legal entity for your cybersecurity business. This could be a limited liability company (LLC), corporation, partnership, or sole proprietorship. Each type has its own benefits and drawbacks so it’s important to do research and choose wisely so that your cybersecurity business is in compliance with local laws. 3. Register Your Cybersecurity Business - Once you have chosen a legal structure, the next step is to register your cybersecurity business with the government or state where you’re operating from. This includes obtaining licenses and permits as required by federal, state, and local laws. 4. Identify Financing Options - It’s likely that you’ll need some capital to start your cybersecurity business, so take some time to identify what financing options are available such as bank loans, investor funding, grants, or crowdfunding platforms. 5. Choose a Location - Whether you plan on operating out of a physical location or not, you should always have an idea of where you’ll be based should it become necessary in the future as well as what kind of space would be suitable for your operations. 6. Hire Employees - There are several ways to find qualified employees including job boards like LinkedIn or Indeed as well as hiring agencies if needed – depending on what type of employees you need it might also be more effective to reach out directly through networking events. 7. Acquire Necessary Cybersecurity Equipment & Supplies - In order to start your cybersecurity business, you'll need to purchase all of the necessary equipment and supplies to run a successful operation. 8. Market & Promote Your Business - Once you have all the necessary pieces in place, it’s time to start promoting and marketing your cybersecurity business. This includes creating a website, utilizing social media platforms like Facebook or Twitter, and having an effective Search Engine Optimization (SEO) strategy. You should also consider traditional marketing techniques such as radio or print advertising.
Cybersecurity Business Plan Sample
This cybersecurity business plan sample is focused on the growing information technology (IT) security sector in Boston, Massachusetts . We hope this sample provides you with a brief foundation for starting your own cybersecurity company. Our cybersecurity business plan writers crafted this sample for your review.
Executive Summary
“ProSecure Squad Corporation” operating as “ProSecure Squad” (The Company) was first incorporated in September of 2016 in Massachusetts, Canada and subsequently incorporated in the State of Massachusetts on June 10 th 2020. Over the past years ProSecure Squad has developed and patented revolutionary Cyber- security products.
With digital transformation of industries being hastened by factors such as E-Commerce, Internet of Things (IoT), Connected Machines, Self-Driving vehicles, Cloud Computing, Artificial Intelligence (AI) and Coivd-19, there has been an enormous increase in the amount of electronic data.
Despite strong cyber-security defenses implemented, cyber-criminals have been getting past these defenses at an increasingly alarming rate and the cost for an organization to retain end-to-end cybersecurity professionals has become astronomical. This has made the Cybersecurity Market one of the fastest growing industries.
With patented products, an accomplished team of cybersecurity experts, and a clear strategy for product and service deployment, ProSecure Squad is ready to lead the next wave of cybersecurity. The company is focused on making its world class data security solutions accessible and inclusive; therefore, targeting wide-scale adoption from medium to large businesses, and government organizations across the globe.
What makes the company’s offering so unique is our focus on simplifying data resiliency; making it easy to protect your data from being spied on, stolen or held for ransom even if a hacker or malware gets past the current cyber-defenses.
With years of research and development, ProSecure Squad has refined our products and has garnered the interests of large corporations in the security and other Industries. With our offering being tailored to meet the current data security demands, ProSecure Squad is well positioned to become leaders in data security.
ProSecure Squad Corporation is seeking a 15 Million USD capital investment in return for a 15% equity and voting stake in the company. These funds will be allocated to taking the company’s products and services to market through direct sales, marketing, customer onboarding and customer support. With this investment the company will execute on established opportunities, further develop its capabilities, and forge a notable position in one of the fastest growing industry.
Business Overview
“ProSecure Squad International Holdings” a US based company is the parent company of two organizations including ProSecure Squad Corporation (USA) and ProTech (India).
These locations and corporate structure have been strategically chosen to tap into the strengths of the local markets in efforts to develop, deploy and maintain state of the art cyber-security products and achieve rapid market share growth.
Mission Statement
To create the most effective and accessible data security products.
Vision Statement
To quench the world’s thirst for data security.
Growth Formula
ProSecure Squad will lead our family of companies into rapid market share growth with the following junctures:
Accomplished Executive Team
- Levi Atif, Founder and Chief Executive Officer. A proven executive leader with experience in law enforcement, cybersecurity and senior management.
- Adib Waqar, Chief Administrative Officer. Southeast Asia’s foremost security, management, and talent development expert.
- Ali Reza, Head of Sales. Sales guru, with proven track record in both enterprise and startup sale hypergrowth.
- Omar Raja, Director of Security. Cyber Security Leader with years of experience in cyber-security, strategy, incident response, and engineering
- Dr. David Khan, Advisor. Professor of Information Engineering at MIT, leading expert in large-scale computation, cybersecurity and cloud computing.
Expert Security, Technical and Sales Team
- Our experts are some of the best in the industry and have been handpicked from organizations such as Deloitte, E&Y, Israel Defense Forces, Samsung, Oracle, GE, EDS, Kearney, to develop state of the art security products.
Teaming Partnerships
- Our Teaming Partnerships are strategic alliances with large and medium sized businesses possessing complementary, yet distinct, skills and resources with goals of our partners selling ProSecure Squad products along with their services and products to their customers.
- These partnerships increase the rate of customer acquisition while reducing the cost of the same.
Coveted Portfolio of Cybersecurity Products
- Over the last few years, ProSecure Squad has been quietly engineering and patenting revolutionary cybersecurity solutions, designed to give ProSecure Squad a formidable lead over key players, cybercriminals and malware.
- Our core products are focused on making it easy for our customers to protect their data, even if a hacker or malware penetrates their cyber defenses, thus ensuring the hacker cannot see, steal or hold their data for ransom.
- The cyber-security threat landscape is changing rapidly and ProSecure Squad will constantly innovate to meet the demands of the ever evolving threats.
Market Demand
- It has been said that timing is the biggest commonality between revolutionary companies.
- With the past unimpressive trends in data security innovation and implementation and the current increase in hacking, there has been a pent-up demand for data security products.
- The current increase in cyber-attacks is predicted to cost the world 6 Trillion dollars in 2021.
- There has been a 9,851% increase in cyber-attacks on health care sectors.
- Industries are starting to enforce data level security (Automotive Industry as an example through UNECE WP29 has mandated data level security for vehicles manufacturers and their suppliers)
- ProSecure Squad is well poised to capitalize on this growing market opportunity by providing its state-of-the-art products and services to a welcoming marketplace of medium to large businesses and government agencies.
Market Accessibility
- We define “Market accessibility” as “Ease at which our customers can consume our products to protect their data”. Technical, Procedural, Financial and Political factors are included when considering Ease.
- Market Accessibility and innovation are extremely important for ProSecure Squad to meet our goals of rapid market share growth.
- Our products have been designed and will continue to improve our Market Accessibility.
Goals and Objectives
- Secure a 10 Million USD capital investment, and ensure Hero, Noble, Shield are ready for deployment.
- Capture at least 500,000 active users by June 2022.
- Ensure our products are fully compatible with the UNECE WP29 Automotive Cybersecurity Regulation
- Increase brand recognition by leading our sector, increasing our presence on Linkedin, and executing a strong search engine optimization strategy.
- Ensure that progressing our company culture is of equal importance to business growth.
- Onboard at least 30 active or retired law enforcement professionals, servicemen and servicewomen by December 31, 2022.
- Receive Health Insurance Portability and Accountability Act (HIPAA) Certification.
- Receive ISO/IEC 27701 (ISO 27701) Certification, a privacy extension to ISO/IEC 27001 and ISO/IEC 27002, designed to help us protect and control the personal information we handle.
- Receive Cybersecurity Maturity Model Certification (CMMC) Certification.
Executive Team
Levi Atif,
Founder & CEO
A lifelong entrepreneur and hands-on CEO with strategic foresight, leadership and determination. As a leader and self-sufficient innovator, Levi is comfortable with any role, from the executive boardroom to the development lab, having managed teams of various sizes and functions.
Levi’s innate ability to adapt, improve, build and motivate high-performance teams has served as a growth catalyst to provide outstanding products. Having served and excelled in various capacities in North American law enforcement and recognized with multiple awards. This along with a background in computer systems and research, gives him a keen understanding of the current issues in the Cybersecurity space.
Levi has published multiple research papers and has developed innovative software that has increased efficiencies and security of systems, processes, which has led to multiple technology patents issued and pending in his name. Excellence is not an accident, but a by-product of meticulous planning and execution – True to this Levi is determined to achieve vertical market share growth for ProSecure Squad by creating excellence in People, Process and Product.
In an effort to give back to the community, Levi has been involved with multiple non-profit organizations such as the Ceres, Cradles to Crayons and has also been actively sponsoring education for children in underprivileged communities.
Adib Waqar,
Managing Director, ProTech
Adib is uniquely positioned to drive operations and talent as one of Southeast Asia’s foremost human rights, security, management, and talent development experts. His public sector strategy to transform the potential of human capital has been sought after and recognized internationally for Meritorious Service, leadership, and excellence, by national governments of multiple countries. Adib holds a BSC and an MA degree in Mathematics, Sociology, Criminology and Management. He also holds certification in Human Rights and Management from Durham University.
Adib was handpicked to advise the Prime Minister of Mauritius during a chaotic term in the country’s Corrections System. Subsequently he was then appointed as the Commissioner of Mauritius by a Parliamentary motion, where he oversaw the transformation of the Prison system from its state of turmoil into being recognized as its best government agency. For this achievement, he was bestowed with the Public Excellency Award in leadership.
For over 49 years Adib has been involved with many success stories regarding leadership, management and reformation. He served with distinction as the Deputy Inspector General of Prisons in India and has been awarded the “President of India Correctional Service Medal for Meritorious Services”, “Golden Jubilee Medal of Independence of India”, and “Silver Jubilee Medal of Independence of India”. Adib’s lean management style has been adorned by his superiors, colleagues and team members.
Head of Sales
Worked in Senior Management Capacity for fortune 500 companies and several successful startups, leading sales and marketing team, Ali holds an MBA from Michigan Technological University.
Over 30 years of experience selling complex IT, and supply chain software solutions, and products and services. Recognized for consistently achieving and exceeding sales and Revenue goals.
Extensive experience in building sales teams, and sales partnership programs that have beat or exceeded revenue goals for the company in both Startup and Growth phase.
Hypergrowth sales experience in enterprise and startup companies such as Xeeva Inc, Revolution Oil, Netlink IT, AT Kearney, GE, EDS Procurement consulting solutions, Market.com and Revolution Oil.
Omar Raja,
Director Security
Omar is a seasoned Cyber Security Leader with 15 years of experience with distinct focus in areas like Cyber Security Strategy, Cyber Forensics and Incident Response, Security Engineering and Implementations, and Cloud Security.
Omar brings in GD consulting and advisory experience in managing, executing and delivering complex and dynamic technology projects in the Cyber Security Space. Most recently, he managed and executed critical engagements like performing security reviews of GD data platforms for one of the leading global BFSI partners; defining and Implementing the connectivity baseline security for one of the leading global Automotive partners, and providing a strategic roadmap around consolidation of the HSM’s [Hardware Security Module] for one of the leading global BFSI firms.
As a GIAC Certified Forensic Examiner, Omar has over 1000+ hours of digital forensic hands-on experience including data imaging, forensic analysis, carving and harvesting. He also designed and deployed the next generation in intrusion prevention, with a revolutionary approach that completely re-thinks the cycle on how to detect and protect from adversaries. He also possesses strong business development, project and program management skills, leadership and interpersonal skills. He has worked with partners across a range of industries, including BFSI, Technology, Telecom and Manufacturing.
Dr. David Khan,
Dr. David Khan is a Professor of Information Engineering at MIT and a leading expert in large-scale computation, cybersecurity and cloud computing. He has been named one of the Top-50 Most Influential Persons in Computer Networks in the world.
Dr. Khan has published over 300 papers and 4 books. He served as Director of the MIT AutoID Laboratory from 2006-2010, where the “Internet of Things” was invented. He also served as Co-Director of the seven global AutoID laboratories, which developed the Electronic Product Code Information Systems (EPCIS)—a key software component used by industry and government to drive almost every supply-chain. He was a member of the EPC Global Architectural Review Committee for global standards.
In cyber-physical security, Dr. Khan was PI for impact analysis of large-scale cyberattacks and in collaboration with Lincoln Laboratories, where he designed a Cyber Range for the United States Department of Defense (DOD), which enabled his team to conduct experiments and model the cyber environment in a highly portable fashion.
In machine learning, he is working to address financial fraud for a $70 billion state enterprise. This Accenture-funded project designed a situational awareness framework to exploit different perspectives of the same financial data, and assigns risk scores to entities (payment documents) to improve false positive ratios, and to help identify fraudulent activity in huge and unlabelled financial data sets.
Dr. Khan consults for companies across the world including Accenture, Altria, Kajima, Simizu, SAP, Shell, Exxon, Aramco, Total, IBM, Microsoft. Along with Dr. Tan, he teaches online courses in Digital Transformation, Data Science, Computational Thinking, and Blockchain.
Core Products
Shield’s Patented technology is an easy to integrate, lightweight software that can be used by application developers to protect data as it is being moved from one device to another, or while it is being stored at endpoints such as Mobiles, Machines, IoT devices, etc.
As the volume of data that is being moved around and stored in the endpoints increases, it becomes critical to protect this data. While infrastructure security technologies like TSL, VPN, firewall, and others protect today’s data pipelines, the data itself remains vulnerable and unprotected.
Hackers have been extremely successful in spying and stealing such data and even use it to take over IoT devices and machines with disastrous consequences. Currently there is no easy and quick way for application developers to secure the application data in transit or when it is stored in the Levices.
Going to market rapidly is critical for the success of a company. Lack of rapidly deployable data protection products has led to the developers, either not implementing these security precautions or choosing to implement basic level security, often with little or no internal and third party security testing.
Hackers and malwares are exploiting these weaknesses which has resulted in an increase in hacking. As an example there has been a 9,851% increase in attempted attacks on health care endpoints.
Just to give a few examples of who can use Shield; (a) Companies with Mobile Application (b) IoT Manufactures (c) Air/Sea & Land Vehicle Manufactures (d) Machine Manufactures (e) Space Manufactures (f) Medical Machine Manufacturers (g) Robotics Manufacturers (h) Sensors Manufacturers (i) Entertainment Industry (ensuring videos or audios cannot be used without the application) etc.
Product Pricing
Ou r products are sold in a Security as a Service (SaaS) model, where our products will be licensed for use by our customers.
ProSecure Squad plans to onboards companies in the targeted verticals which has mobile application and sensitive data. Through these mobile applications, ProSecure Squad is planning to support 500,000 active monthly users.
If these 500,000 users encrypts data only 5 times daily using their mobile applications, ProSecure Squad is expecting 2,500,000 encryption each day for a daily revenue of $2,500 and a yearly revenue of $ 912,500.
Targeted Verticals
- Mobile Application Developers
- BFSI Mobile Application
- Betting Mobile Application
- Dating Mobile Application
- Defense Mobile Application
- Health Care Mobile Application
- Government Mobile Application
- Social Media Mobile Application
- Telecommunication Application
- Automobile Mobile Application
- Retail and e-commerce Mobile Application
- Entertainment Application
- Education Application
- Machine Manufactures
- IoT Manufactures
Hero’s Patented technology protects data and keep it safe from both internal and external threats. Despite strong security measures, major corporations, and governments have been increasingly susceptible to having their data stolen or held for ransom. ProSecure Squad protects data in storage by distributing it and hiding it so a hacker cannot see it, seal it or lock it.
Hero does not use access based system to protect data unlike most modern storage system, instead our patented product uses “doublelocks” (ie. Uses a user keys and users themselves) and “ledger-less distribution” which breaks the data into tiny pieces, encrypts and distributes it amongst hidden nodes. Only if the “doublelock” is unlocked can the data pieces can even be located.
With an increasing number of breaches in the cloud, despite strong infrastructure security technologies like TSL, VPN, firewall, and others which protect today’s data pipelines, the data itself remains vulnerable and unprotected.
Hackers have been extremely successful in spying, stealing and holding for ransom the data stored in the cloud with disastrous consequences. Having the data “doublelocked” and “ledger-less distributed” means that no one except the data owner can locate the file let alone try to decrypt it. This reduces the chances of advanced attacks and insider attacks on the customers data.
Even encrypted data stored in the cloud have been compromised multiple times in the recent past and they have also been held for ransom. The problem lies in the fact that even encrypted data can be decrypted with appropriate access, this weakness has been exploited by attackers successfully as evidenced in the recent breaches.
Just to give a few examples of who can use Hero; (a) Companies that store sensitive data and want to protect it (Trade secrets, customer information, secret formulas, financial information etc.) (b) Companies that want to back up sensitive data and have ransomware protection (c) Cloud data storage companies such as Dropbox.
- Banking, Financial, Securities and Insurance Industry (BFSI)
- Health Care
- Governments
- Information Technology
Our products are sold in a Security as a Service (SaaS) model, where our products will be licensed for use by our customers. The licensing cost for Shield is as below:

Over 80% of security breaches are credentials-related, Noble’s authentication is infused with advanced security features, such as multifactor (biometric, puzzle, location, Levice) multipoint, cross platform authentication to validate a user or data. The hassle free Biometrics is privatized, protected and kept in compliance, so you do not have to worry about it. Noble is more than just an user authentication module, our innovative use of this technology extends biometrics to data protection as well. Noble technology can readily integrate into your desktop or mobile device to provide unparalleled, hassle free user and data validation. The Noble is fast, reliable and can keep your bio-metrics protected, private and in compliance.

ProSecure Squad Hero, Shield and Noble will be targeted to the following verticals:
- Information Technology (IT)
- Manufacturing
- Banking, Financial Services and Insurance (BFSI)
- Government & Defense
Let's Get Started!
- Your Name *
- Email Address *
- Phone Number
Peripheral Products
Modernize and protect your business by exchanging and storing files through the most secure cloud platform for file transfer and storage. Your privacy is paramount, no one except the data owner will ever be able to access the data.

Managed Security Services
Providing state of the art enterprise level cyber-security services for your business, by assessing, managing, mitigating and responding to a multitude of cyber threats, so you can focus on your business.

Recurring Revenue +New Customer Acquisition
We plan to provide our core products to the following verticals:
- Small to medium-sized businesses (SMBs)
- Healthcare
- Energy & Utilities
Operational Model
ProSecure Squad’s operations will consist of a Hybrid Business Model where a portion of team members work remotely from home, and others meet at designated offices. This will be determined by two overriding factors: whether a team member resides near one of our offices, and whether their position is optimized for remote or in-person work. In situations that there is flexibility around this matter we will provide staff with the option to choose whether to work from home or in the office.
At the present time, ProSecure Squad is located in Massachusetts , Michigan and India. ProSecure Squad has a physical location in India and operates remotely in Michigan and Massachusetts. ProSecure Squad is looking for a space in Massachusetts and have embarked in negotiations. The following will determine the location for ProSecure Squad’s headquarters:
- Strong support by local government
- Lower cost of resources
- Robust Manufacturing, Health and Government Sector presence
Process Quality and Auditing
Security and quality are built into our DNA, ProSecure Squad is an ISO270001 certified company and working towards other certifications (ISO 27701, NIST, HIPPA, CMMC etc). On a regular basis, we audit ourselves and along with external parties to ensure security and quality.
Deloitte has been tasked with ensuring manning and operating a 24X7 Security Operations Center for ProSecure Squad.
Our External Audit is conducted by:
ProSecure Squad has the greatest businesses on the planet protecting us, and helping us grow. This can be shown by our external auditing process:
- Deloitte: 24/7 security monitoring, annual external audit
- KPMG: annual external audit
- International Organization for Standardization (ISO): process and security audits
Our internal auditing process consists of the following:
- Internal Auditing Team that is reviewed quarterly by management
- Cyber Governance Team that is reviewed every 6 months by management
- Process and Security Audits conducted weekly and quarterly
Process Quality
ProSecure Squad has developed and matured a robust software research, development, QA Testing and Security Testing which includes both internal and external testing partners. The process has been audited by Deloitte and during our ISO audit. Please find the process below:
Customer Journey Process
ProSecure Squad’s customer journey process is as below:
- LEAD STAGE: A lead is a potential buyer.
- PROSPECT & QUALIFYING STAGE:
- Prospect – A lead that is qualified or determined to be ready, willing, and able to buy.
- Qualified Prospect (QP) – A prospect who has been approved by ProSecure Squad for the sales agent.
- DISCOVERY MEETING: Strategic approach to the QP.
- DEMO/SOLUTIONING: Educating the customers on how we can enable their technology and security needs.
- PROPOSAL: Written documents where ProSecure Squad offers product and our service pricing to the potential customer. The proposal should demonstrate how we can serve the needs of the potential customer by showing the key benefits and value that ProSecure Squad can provide.
- NEGOTIATION: This is the strategic discussion between the buyer and the seller that will ideally lead to a deal being closed.
- CLOSE: This is the final agreement on both sides to complete the signing of the deal, and move forward on delivering the products, or services purchased.
Market Overview
The global cybersecurity market was worth $173B USD in 2020, growing to $270B USD by 2026. By 2026, 77% of cybersecurity spending will be for externally managed security services. While money spent on in-house or internal cybersecurity functions is expected to grow 7.2% each year to 2026, global spending on external cybersecurity products and services is projected to increase by 8.4% annually over the same period.

Cyber security and defense against online threats undertake greater significance in today’s digital changing landscape. It has become vital amid organization due to rapidly increasing frauds, cybercrimes, risk, threats, and vulnerabilities. Disruptive and emerging technologies in banking, retail, information technology, defense, and manufacturing sectors have offered new capabilities, facilitated automation, and offered ease of working in the recent past. However, these technologies have also emerged as a potent factor in the development of the global threat landscape of exploits, vulnerabilities, and malware. The emerging threat landscape is observed with an increased number of cybercrime activities in the global digital era.
Market Trends
Expanding Cyber-Attack Surface (Remote Work, IoT, Supply Chain)
According to cybersecurity ventures, t he world will store 200 zettabytes of data by 2025 . This includes data stored on private and public IT infrastructures, on utility infrastructures, on private and public cloud data centers, on personal computing devices.
The digital transformation was rapidly pushed by Covid-19 and the need to move individuals working in offices to working remotely from their homes. That led to essentially millions of connected offices. It is estimated that nearly half the U.S. labor force is working from home , and that it is greater in many other countries due to lockdowns. Home offices are not as protected as the fortified office sites that have more secure firewalls, routers, and access management run by Its security teams. Remote work has created new opportunities for hackers to exploit vulnerable employee devices and networks. Dorit Dor, vice president of products, Check Point Software elaborated on how the digital transformation. “Businesses globally surprised themselves with the speed of their digital initiatives in 2020: it’s estimated that digital transformation was advanced by up to seven years. But at the same time, threat actors and cyber criminals also changed their tactics so that they could take advantage of these changes, and the pandemic’s disruption, with surges in attacks across all sectors.”
The 2021 Director of National Intelligence (DNI) report estimates that IoT will reach 64 billion objects all monitored in real time. “Looking forward, a hyperconnected world could support up to 1 million devices per square kilometer with next generation cell phone systems (5G), compared with the 60,000 Levices currently possible with current cell networks, with even faster networks on the horizon.” Office of the Director of National Intelligence – Global Trends (dni.gov)
The Internet of Things (IoT) is related to supply chain vulnerabilities. IoT’s exponential connectivity is an ever-expanding mesh of networks and devices. Supply chain cyber-attacks can be perpetrated from nation state adversaries, espionage operators, criminals, or hacktivists. Their goals are to breach contractors, systems, companies, and suppliers via the weakest links in the chain. This is often done through taking advantage of poor security practices of suppliers, embedding compromised (or counterfeit) hardware and software, or from insider threats within networks. Please see my FORBES article: Cybersecurity Threats: The Daunting Challenge of Securing the Internet Of Things Cybersecurity Threats: The Daunting Challenge Of Securing The Internet Of Things (forbes.com)
Protecting such an enormous attack surface is no easy task, especially when there are so many varying types and security standards on the Levices.” One way to address the expanding attack surface is to use an automation tool chest that can now utilize horizon scanning technologies, analytics, audits, incident alert tools, diagnostics, and even self-repairing software. Artificial intelligence and machine learning technologies can also provide for more efficient decision making by prioritizing and acting on threats, especially across larger networks with many users and variables.
Ransomware as a Cyber Weapon of Choice
Ransomware has been around for almost two decades and has grown in popularity because it can more easily bring financial rewards to hackers. It is estimated that there are now 124 separate families of ransomware and hackers have become very adept at hiding malicious code. Success for hackers does not always depend on using the newest and most sophisticated malware. It is relatively easy for a hacker to do. In most cases, they rely on the most opportune target of vulnerability, especially with the ease of online attacks.
Last year, ransomware made up nearly a quarter of the incident-response engagements for IBM Security’s X-Force threat intelligence group. Fifty-nine percent of the ransomware incidents involved cybercriminals exfiltrating, before encrypting, the data — so-called “double-extortion” attacks. Ransomware, Phishing Will Remain Primary Risks in 2021 (darkreading.com)
The reason is that ransomware became a weapon of choice for hackers in the COVID-19 induced digital landscape. The transformation of so many companies operating in a mostly digital mode had created more targets for extortion. According to a research study by Deep Instinct, ransomware increased by 435% in 2020 as compared with 2019. And the average ransomware payout has grown to nearly $234,000 per event , according to cybersecurity firm Coveware. Malware increased by 358% in 2020 – Help Net Security
The trend in 2021 is that criminal hacker groups are becoming more sophisticated in their phishing exploits with use of machine learning and more coordinated sharing on the dark web and dark web forums. Hackers are also able to get paid via cryptocurrencies that can be difficult to trace making ransomware more a priority in their exploit tool chests. With the advent of cryptocurrencies in ransomware, it became a profit motive for a lot of the criminal enterprises. They replaced brick and mortar crime with digital crime.
The estimated cost of ransomware was $20 billion in 2020, a rise from $11.5 billion in 2019 and $8 billion in 2018. That trend will continue to grow. 22 Popular Types of Cyber Attacks in 2021 – CyberExperts.com The likely impact for the near-term future is that there will be more ransomware attacks against institutions and corporations who are less cyber secure and cannot afford to have operations impeded such as health care, state & local governments, and educational institutions. Preventing ransomware requires cybersecurity awareness and preparation based on anti-malware programs, secure passwords, updating patches and having secure routers, VPNs, and Wi-Fi. Most important of all, do not fall for the Phish and be sure to back up sensitive data.
Threats Against Critical Infrastructure; ICS, OT/IT Cyber-Threat Convergence
The 2020 World Economic Forum’s Global Risks Report listed cyberattacks on critical infrastructure (CI) as a top concern. WEF noted that “attacks on critical infrastructure have become the new normal across sectors such as energy, healthcare, and transportation.” The Global Risks Report 2020 | World Economic Forum (weforum.org) Dragos Inc. “Year in Review 2020” report of industrial control systems (ICS) and operational technology (OT) cyberthreats, vulnerabilities, assessments and incident response insights determined that threats have increased threefold in the past year. Dragos: ICS security threats grew threefold in 2020 on February 24, 2021 at 12:00 am SearchSecurity (itsecurity.org)
The threats are growing along with the attack surfaces associated with CI. The types of cyber threats include phishing scams, bots, ransomware, and malware and exploiting software holes. The global threat actors are many including terrorists, criminals, hackers, organized crime, malicious individuals, and, in some cases, adversarial nation states. Hackers often seek out unsecured ports and systems on industrial systems connected to the internet. IT/OT/ICS supply chains in CI can be particularly vulnerable as they cross pollinate and offer attackers many points of entry and older Legacy OT systems were not designed to protect against cyber-attacks.
In the U.S., most of the critical infrastructure, including defense, oil and gas, electric power grids, health care, utilities, communications, transportation, education, banking, and finance, is owned by the private sector (about 85 percent) and regulated by the public sector. The energy sector stands out as being particularly vulnerable. This ecosystem of insecurity includes power plants, utilities, nuclear plants, and The Grid. A reason for why the sector has become more vulnerable is that hackers have gained a deeper knowledge of control systems and how they can be attacked and can employ weaponized malware against power stations and other energy related CI assets.
The recent Solar Winds Cyber-attack can also be viewed as a wake-up call for the interactive nature of OT/IT infrastructures. According to Grant Geyer, chief product officer of Claroty the advanced capabilities and backdoors in use by the attack “should put any organization that includes nation-state actors as part of their threat mode on alert, including critical infrastructure, industrial control systems (ICS) and SCADA operators.” SolarWinds: Why OT should worry (controlglobal.com)
Protecting critical Industrial Control Systems (ICS), Operational Technology (OT), and IT systems from cybersecurity threats is a difficult endeavor. They all have unique operational frameworks, access points, and a variety of legacy systems and emerging technologies. The explosion of connected devices comprising the Internet of Things and The Internet of Industrial Things is challenging. The trends of integration of hardware and software combined with growing networked sensors are redefining the surface attack opportunities for hackers across all digital infrastructures.
To help ameliorate threats, critical infrastructure operators should apply a comprehensive risk framework to implement or to address vulnerabilities to OT/IT convergence including “security by design”, defense in depth, and zero trust to counter cyber threats. It is especially important for the public and private sectors to coordinate and apply and enforce industry security protocols, especially related to Supervisory Control and Data Acquisition (SCADA). The Internet was not built for security at its inception; it was built for connectivity. Following industry and government protocols derived from lessons learned is essential for protecting vital infrastructure.
Other mitigation efforts can be done by employing new technologies that monitor, alert, and analyze activities in the network. Emerging technologies such as artificial intelligence and machine learning tools can help provide visibility and predictive analytics. It is also good to have diversification and multiple sourcing for suppliers in the event of a breach. Preparation and redundancy are advantageous in crisis scenarios. But like most issues in cybersecurity, it comes down to people, vigilant processes, and technologies coupled with risk factors constantly being reviewed.
Competitive Advantages
Technical Advantages: Our products are revolutionary, making it near impossible for an attacker to even stand a chance. What truly sets us apart is our proprietary technology which protects our customers’ data. We understand the importance of continuing to be pioneers in the cyber-resiliency space.
These technical advantages offer a strategic advantage not only because of the patents, but also because of the diversity of clients we can onboard.
- Advanced Transit Protection – By breaking the data into tiny pieces and “doublelocking” it with receiver information, we can ensure that no one expect the receiver can see the data. The encryption, changes every time there by evading advanced attacks.
- Endpoint Data Protection – The data which has been protected by Shield cannot be viewed or used by any application other than the actual application that put the data there. Thereby increasing security of the data.
- Multi-Platform – The above protections can be done in mobile, desktop, cloud, machines, IoT Levices etc., thereby giving ProSecure Squad an unique advantage over our competition.
- Low Code – Integrating our products only needs a minimum level of coding, in fact ProSecure Squad is planning to embark on a journey to automate the process of integration of our products into applications. This will further enhance our capability and improve the speed at which we can deploy.
- Ledger less Distributed Data Protection – By distributing the broken pieces of data across hidden storage without a ledger, we can ensure no one except the data owner can access the data.
- Double Lock Protection – We lock the data with the owners keys and the owners information to ensure the distributed data cannot be pulled out without the data owner.
Business Advantages
- Teaming Partnership – Our Teaming Partnerships are strategic alliances with large and medium sized businesses possessing complementary, yet distinct, skills and resources with goals of our partners selling ProSecure Squad products along with their services and products to their customers. This partnership increases the rate of customer acquisition while reducing the cost of the same.
- Accessibility – Our products will become more and more easy to use and also affordable.
Sales & Marketing Plan
ProSecure Squad is planning to sell to customers using both Direct sales and Teaming Partners. Teaming partners will be used as power resellers while direct sales will primarily be done through our sales team and it will be supported by commission only contractors. ProSecure Squad will also work with social media marketing agencies to market directly to customers.
Targeted Verticals
- Information Technology,
- Banking, Financial Services and Insurance (BFSI),
- Healthcare,
- Media and Entertainment,
- Manufacturing,
- Health care,
- Government & Defense.
Key Channels
Direct Sales
- Outbound emailing
- Sponsored Linkedin Messaging
- Outbound Calling
Teaming Agreements
- Deloitte, KPMG, Wesco, EY
- Will utilize this model with future clients, where they can upsell our products
Social Media Marketing
- Linkedin Content and Engagement
- Facebook Marketing to build awareness
- Targeted pay per click advertising
Financial Plan
Pro Forma Income Statement

Pro Forma Cash Flow Statement

Pro Forma Balance Sheet

Have Questions? Looking To Get Started?
How can we help you.
Get in touch with us or visit our office

Cybersecurity Business Plan (CBP)
Maximum file size is 15000KB , file types are bmp, gif, jpg, jpeg, jpe, jif, jfif, jfi, png, wbmp, xbm, tiff
Cybersecurity Business Plan (CBP) Template
Product walkthrough video.
This short product walkthrough video is designed to give a brief overview about what the CBP is to help answer common questions we receive.
|
|
What Is The Cybersecurity Business Plan (CBP)?
The Cybersecurity Business Plan (CBP) is a business plan template that is specifically tailored for a cybersecurity department, which is designed to support an organization's broader technology and business strategies. The CBP is entirely focused at the CISO-level, since it is a department-level planning document.
Our products are one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product! The CBP contains a template and guidance to develop organization-specific mission, vision, strategy, objectives, etc. in an editable Microsoft Word format. The following content is what you will have in the CBP with examples that you can easily modify for your specific needs:
- Organizational description
- SWOT analysis
- Definition of success
- Value proposition
- Department-level "elevator pitch"
- Prioritized objectives
- Concept of Operations (CONOPS)
- Mid-term planning
- Long-term planning
- Marketing plan
- Financial plan
- Capability Maturity Model (CMM) target definitions
The CBP can serve as a foundational element in your organization's cybersecurity program. It can stand alone or be paired with other specialized products we offer.
What Problems Does The CBP Solve?
- Lack of In House Security Experience - Writing security documentation is a skill that many good cybersecurity professionals simple are not proficient at and avoid the task at all cost. On top of that, writing a cybersecurity-specific business plan is a skill that not many CISOs have experience with, so it is an often outsourced or neglected activity.
- Budget Justification - Having a coherent plan is a valuable tool for a CISO to defend budgets, since it enables the CISO to paint a long-term picture for the cybersecurity department and why the investment makes good business sense.
- CISO Career Protection - Having a documented business plan is valuable from a CISO's perspective more than just in defending staffing and budget requests. In cases where a viable business plan is rejected from a funding perspective by senior management, a CISO at least has evidence of appropriate due care on their part. In the event of a breach/incident where the CISO is "on the hook" for the blame, a CISO can demonstrate how the CIO/CEO/CXO that rejected the CISO's recommended practices and funding request(s) that could have prevented the incident now own that risk. It is a way to pass risk up the chain of command.
Our customers choose the Cybersecurity Business Plan (CBP) because they:
- Have a need for a timely and cost-effective solution to document their cybersecurity strategy and roadmap.
- Need to be able to edit the document to their specific needs.
- Have documentation that is directly linked to best practices, laws and regulations
- Need an affordable solution
How Does the CBP Solve These Problems?
- Clear Documentation - The CBP provides comprehensive cybersecurity business planning documentation to prove that your security strategy and roadmap exists. This equates to a time saving of considerable staff time and tens of thousands of dollars in either lost productivity or consultant expenses!
- Time Savings - The CBP can provide your organization with a semi-customized solution that requires minimal resources to fine tune for your organization's specific needs.
Being a Microsoft Word document , you have the ability to add/remove/edit content, as needed. We've provided an "80-90% solution" from the perspective of formatting and content, where you merely polish off the specifics that only you would know about your organization and its culture. While we did the heavy lifting in the research and development of this cybersecurity planning document, we estimate that a mid-sized organization should be able to finalize the CBP in about 5-10 hours . That final customization focuses on "owning" the document where you wordsmith the example statements that we provide so that the content of the document is specific to your organization and relates to specifically what you do.
Ideally, your organization's CISO is the individual who will edit/finalize the CBP. Fortunately, the CBP is written in a format that it can be "ghost written" for the CISO by their subordinates (we understand the time constraints many CISOs experience and planning functions are often delegated). In these instances, the CBP can easily be edited and finalized based on the CISO's existing guidance to subordinates. It is important to understand that goals are not the same thing as a strategy! It is often the case where there are a lot of good ideas and "shopping lists" for products/initiatives, but there is a lack of a formalized strategy to accomplish a set of goals. This is where the CBP is a valuable resource, since it creates a formal cybersecurity strategy and roadmap!
Product Example - CBP - Cybersecurity Business Plan Template
The CBP is a fully-editable Microsoft Word document that you can customize for your specific cybersecurity business planning needs. You can see the table of contents below to see everything the CBP covers. Due to the concise nature of the document, we are limited to what content we can share publicly for examples.
View Product Example
Cost Savings Estimate - Cybersecurity Business Plan (CBP) Template
The CBP is affordable when compared to alternatives. The cost is equivalent to about five (5) hours of a cybersecurity professional's time, which is a fraction of the time it would take to create a similar document on its own. When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save over a hundred hours of staff time and the associated cost of lost productivity. Purchasing the CBP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 120 internal staff work hours , which equates to a cost of approximately $9,000 in staff-related expenses. This is about 1-2 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 80 consultant work hours , which equates to a cost of approximately $24,000 . This is about 2-4 weeks of development time for a contractor to provide you with the deliverable.
- The CBP is approximately 8% of the cost for a consultant or 22% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the CBP the same day you place your order.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.

Template For Creating A Cybersecurity Strategy & Roadmap
ComplianceForge provides businesses with exactly what they need to for cybersecurity planning at a very affordable cost. Similar cybersecurity business planning documentation can be found in Fortune 500 company that have dedicated cybersecurity staff. The architect for the CBP is a former military officer and MBA who has years of experience building cybersecurity business plans and has extensively written on the subject.
Learn More About Cybersecurity & Data Privacy
Nist 800-171 r2 to r3 transition guide.
Sooner, rather than later, the US Government's global supply chain will have to transition to NIST 8...
NIST 800-171 R3 Kill Chain
The CMMC 2.0 & NIST 800-171 R2 version of the CMMC Kill Chain introduces the theory of constrain...
NIST 800-171 R3 In A Nutshell
It is worthwhile to take a look at NIST 800-171 R3 through a People, Process, Technology, Data &...
NIST 800-171 R3
NIST 800-171 Rev 3 was released on 14 May of this year, and it contains significant changes from the...
VISIT OUR FAQS
Questions about our products?
CUSTOMER SERVICE
Our customer service is here to help you get answers quickly!
WHY CYBERSECURITY?
Find out the importance of these documents for your business.
Read exclusive information about cybersecurity from Compliance Forge.

Cyber Security Business Plan Template [Updated 2024]
Cyber Security Business Plan Template
If you want to start a cyber security business or expand your current cyber security business, you need a business plan.
The following Cyber Security business plan template gives you the key elements to include in a winning Cyber Security business plan. In addition to this template, a solid plan will also include market research to help you better understand market trends, your competitive advantage and your target customers. It will also help you craft your marketing plan and strong financial projections.
You can download our business plan template (including a full, customizable financial model) to your computer here.
Cyber Security Business Plan Example
Below are links to each of the key sections of your Cyber Security business plan: I. Executive Summary II. Company Overview III. Industry Analysis IV. Customer Analysis V. Competitive Analysis VI. Marketing Plan VII. Operations Plan VIII. Management Team IX. Financial Plan
Comments are closed.
Cyber Security Business Plan Home I. Executive Summary II. Company Overview III. Industry Analysis IV. Customer Analysis V. Competitive Analysis VI. Marketing Plan VII. Operations Plan VIII. Management Team IX. Financial Plan


Starting A Security Company Business Plan (PDF)

Starting a security company can be a highly profitable venture in today’s world, where the need for security is ever-increasing. This industry, characterized by its robust demand and attractive profit margins, offers a unique opportunity for entrepreneurs looking to establish a sustainable and financially rewarding business. The rising concerns over personal and corporate safety have fueled a surge in the demand for security services, making it an opportune time to enter this market. The security sector’s appeal lies in its wide-ranging services, from residential security to corporate safety measures, catering to a diverse clientele. This versatility not only broadens the potential customer base but also allows for considerable flexibility in tailoring services to specific market needs. With the right approach and understanding of the market, a security company can achieve significant profitability. This is bolstered by the industry’s inherent scalability, where businesses can start small and expand their offerings as they grow, maintaining healthy profit margins throughout. This article will outline how to start a security company business and the security company business plan (PDF, Word & Excel).
Market Research
Market research plays a pivotal role in the process of launching a security company business. It serves as the compass that guides entrepreneurs through the complex terrain of the security industry. Begin by analyzing the overall security industry. Look into various segments like residential, commercial, event security, and cybersecurity. Evaluate the size of these markets, growth trends, and the major players. Understanding where the industry is headed can help you spot opportunities and potential gaps in the market. Not all security companies are the same. Some focus on physical security guards, while others specialize in advanced technological solutions like surveillance systems or cybersecurity services. Your market research should help you identify a niche that aligns with your expertise and market needs. Whether it’s a specific sector like retail security or a type of service like risk assessment, finding your niche is key to standing out.
A critical part of market research is analyzing your competitors. Who are they? What services do they offer? What are their strengths and weaknesses? This analysis will help you understand your competitive advantage. Pay attention to their customer service, pricing strategies, technological adoption, and client feedback. Knowing what potential clients want and need is paramount. Conduct surveys, interviews, or focus groups with potential customers to gather insights. Look into what businesses or individuals in your target market are looking for in a security service, what they feel is lacking in current offerings, and what would make them choose a new provider. Every industry has its regulations, and security is no exception. Research the legal requirements for starting and operating a security company in your region. This includes licenses, certifications, and any specific laws that pertain to security operations. Budgeting and financial planning are indispensable components of market research. Accurate financial projections, encompassing startup costs, operational expenses, and revenue estimations, are key to securing funding and maintaining financial stability.
Location & Premises
Centrality in area covered and proximity to clients.
The things to consider here for a security company business depends on the nature of your services. Typically you will be deploying guards to certain spots e.g. commercial, industrial, or residential properties. This can be during the day, overnight, or both. The heart of a security company business is a command centre or centre of operations. This means its location must be central to the area you make deployments in. The thrust is to also be generally as close as possible to your deployments or areas you cover. This is of critical importance especially when rapid responses are needed.
Spacious Enough, Secure Enough And Accessible Enough
Consider a security company with a substantial fleet of vehicles – which should be the goal anyways. You would need adequate space for parking and easy access. You also need to consider that a security company’s centre of operations tends to be segmented. There is need for office space, locker room(s), briefing room, and an armory – at the very least. Regardless, the footprint of a command centre need not necessarily be that big. A potential target by organized crime gangs can be your command centre. Thus it is important to ensure the place is secure. If possible, make your centre of operations as inconspicuous as possible. It should also be easy to access and exit in case of rapid response situations. The costs of purchasing or leasing the premises should be included in your security company business plan.

Vehicles And Equipment
Transportation vehicles are required e.g. bicycles, motorbikes, and light motor vehicles. In some cases vehicles might need to be armored. Vehicles are required for patrolling and transporting valuable goods. There is some basic equipment needed for a security company business but it all boils down to the scale and sophistication of your operations. Examples of basic security company equipment are wireless communication devices (e.g. walkie-talkies), uniforms (or apparel), firearms, and defence equipment. Surveillance equipment such as CCTV cameras, drones, binoculars, and the like may be needed. Ancillaries such as baton sticks, hand cuffs, flashlights, and stun guns (or tasers) are needed. Office equipment and supplies are necessary for administrative procedures. The security company business plan should include the costs of purchasing the vehicles and equipment.
Products & Services
The services you can offer as a security company business depend on the type of clients you intend to serve.
Guard & Patrol
This is the easiest and most common security company service to provide. The approaches to this are many and can be tailored to suit client needs. You have residential security where there can be guards stationed somewhere and doing periodic sweeps. The same can also be done for industrial and commercial properties. This can be done overnight mostly or even any time of the day depending on the circumstances. This service is best accompanied by CCTV surveillance monitoring. This can be done from the depot or there can be a command post onsite.
Access Control
This is yet another common security company service. It takes on various forms but the core focus is security personnel controlling access to a property. For instance, guards can be stationed at entrances or inside places such as shopping outlets, banks, and government buildings. It is also common for areas or buildings with restricted access. Access control as a security company service can also be provided at important events. This service also morphs into crowd control where applicable.
Close Protection
This is also known as VIP protection. This entails providing security services for high profile people such as celebrities, politicians, and business moguls. It can also span to anyone who feels they need and can afford close protection. Close protection is a high stakes service but is highly profitable. The service can be provided as once-off or on a retainer basis.
Other Security Products And Services
Other security services that you can offer include Mobile Patrol, K9 security, Cash Handling and Armed Escort Services. The other security products that you can offer include Security Alarms, CCTV Systems, Access Control Systems, Gate Automation and Tracking Systems. Your security services business plan should outline all the products and services that you are going to offer.
Staff & Management
The model of personnel doubling up duties can be employed for a security company business. It is not always the case that everyone is in the field. This means a security guard can also perform administrative or secretarial duties. This goes a long way in keeping your human resources tight to minimize operating costs. You basically need the security guards and office or administrative staff to begin with. The salary costs of all your personell should be included in the security company business plan.
Budgeting and Financial Planning
Budgeting and financial planning form the cornerstone of a prosperous security company business. Irrespective of whether you’re embarking on a startup venture or seeking to expand an existing operation, meticulous financial management is a non-negotiable aspect of success. The process commences with estimating startup costs, meticulously accounting for licensing fees, equipment purchases, marketing expenses, legal and insurance fees, and office space rentals. A well-structured budget serves as a financial road map, facilitating secure funding acquisition and preempting unforeseen financial challenges. Moving forward, the realm of financial planning encompasses a meticulous assessment of operational expenses. Anticipating costs related to employee salaries, insurance premiums, utility bills, vehicle maintenance, and other overheads is vital for financial stability. Accurate revenue projections, based on a thorough understanding of pricing strategies, target market size, and competitive positioning within the security industry, further fortify the financial planning process. These projections provide guidance for budgeting efforts and the establishment of realistic financial objectives.
Cash flow management is equally vital, ensuring that your security company maintains sufficient working capital to cover daily expenses, compensate employees, and seize growth opportunities. Additionally, comprehensive financial planning incorporates contingency measures for unexpected events, a crucial component for safeguarding business operations in the face of unforeseen challenges. When seeking expansion or diversification, the financial plan becomes a strategic tool for evaluating investment opportunities and assessing the sustainability and profitability of growth initiatives. Moreover, tax planning strategies, devised in consultation with tax professionals, can optimize deductions and credits, ultimately enhancing your company’s financial well-being. Periodic reviews and adjustments of the financial plan ensure alignment with evolving market conditions and business objectives, securing the financial health of your security company for the long term.
Marketing Strategies
Marketing Strategies are the backbone of a thriving security company business. In an industry as competitive as security services, it’s vital to employ a diverse range of strategies to attract and retain clients while establishing a robust brand presence. First and foremost, building a compelling online presence through a professional website and employing digital marketing techniques, such as SEO and social media engagement, is imperative. This not only enhances your visibility but also allows you to connect with potential clients and share your expertise. Content marketing is equally crucial, as it positions you as an industry authority. Regularly producing informative blog posts, articles, videos, and infographics related to security topics not only educates your audience but also boosts your website’s SEO and strengthens your brand.
In addition to these digital marketing strategies, don’t underestimate the power of offline tactics like flyers, billboards, and physically approaching potential customers. Flyers can be distributed strategically in local neighborhoods or at community events to raise awareness of your security services. Billboards strategically placed in high-traffic areas can grab the attention of passersby and serve as a constant reminder of your presence. Physically approaching potential customers through door-to-door outreach or participation in local safety workshops and seminars allows for a personal connection and helps build trust within your community. Networking and forming strategic partnerships within the security industry can open doors to collaborative opportunities, such as bundled services or referrals, enhancing your reach. Leveraging customer testimonials and case studies builds trust by showcasing your track record of success. Implementing a referral program encourages satisfied clients to bring in new business. By combining these traditional marketing methods with digital strategies, your security company can create a well-rounded marketing approach that reaches a wider and more diverse audience.
Identifying and catering to potential customers is pivotal for the success of your security company business, as different client segments have distinct security needs. Residential clients, including homeowners and renters, seek services like alarm system installation and home monitoring to protect their families and properties. Meanwhile, commercial businesses, spanning small enterprises to large corporations, require comprehensive security solutions such as access control systems, surveillance, and alarm monitoring to safeguard their premises, assets, and employees. Retail stores also constitute a significant market, seeking services like surveillance systems and loss prevention to address security challenges related to theft prevention and employee safety.
Corporate offices and educational institutions prioritize security as well, with demands for advanced solutions like access control, biometric systems, and security consulting services. Healthcare facilities, including hospitals and clinics, rely on security services encompassing access control, video monitoring, and security personnel to ensure the safety of patients, staff, and sensitive medical information. Financial institutions, including banks, require stringent security measures to protect assets and customer data, necessitating services such as bank security consulting, alarm systems, and security personnel. Government agencies, with their unique security needs, require specialized services that cater to public facility protection and sensitive data security, ensuring compliance with security regulations.
Industrial and manufacturing facilities seek security solutions like access control, surveillance, and security assessments to protect their equipment, facilities, and intellectual property. Event management companies may require security personnel for crowd control, access management, and emergency response during large gatherings, concerts, or festivals. Construction sites also need security services to prevent theft and vandalism, which may include surveillance, on-site security guards, and access control. Property management companies overseeing apartment complexes, gated communities, or commercial buildings often seek security services to ensure the safety of residents and tenants. By understanding and addressing the diverse needs of these potential customer segments, your security company can effectively tailor its services, attracting and retaining clients in a competitive industry while building strong relationships across various sectors.
Keys To Profitability
Unlocking profitability in the security company business requires a multifaceted approach that integrates several key strategies and considerations. First and foremost, effective cost management is crucial to minimize unnecessary expenditures without compromising the quality of our services. This involves optimizing staffing levels, negotiating favorable supplier contracts, and leveraging technology for efficiency gains. Additionally, pricing strategies must strike a balance between competitiveness and profitability, reflecting the value provided while ensuring healthy profit margins. Maintaining strong client relationships through exceptional service and loyalty programs is another pivotal factor. Customer retention is not only cost-effective but also contributes significantly to long-term profitability. Diversifying our service offerings and exploring opportunities for complementary services can open up additional revenue streams.
Efficient marketing and lead generation strategies, tailored to target ideal clients, must be consistently assessed for effectiveness to allocate resources wisely. Furthermore, investing in employee training and development is crucial, as skilled and motivated staff enhance service quality and efficiency. Embracing technology solutions that improve security operations and client experiences is also essential. Rigorous quality control measures, combined with a culture of continuous improvement, ensure consistent service delivery and client satisfaction. Efficient cash flow management safeguards financial stability, while market expansion into underserved areas or niche segments can lead to new revenue streams. Legal and regulatory compliance is imperative to avoid costly penalties or reputational damage.
Pre-Written Security Company Business Plan (PDF, Word And Excel): Comprehensive Version, Short Funding/Bank Loan Version and Automated Financial Statements
For an in-depth analysis of the security services business, we encourage you to purchase our well-researched and comprehensive security services business plan. We introduced the business plans after discovering that many were venturing into the security business without enough knowledge and understanding of how to run the business, lack of understanding of the financial side of the business, lack of understanding of : the industry, the risks involved , costs and profitability of the business; which often leads to disastrous losses.
The StartupBiz Global security business plan will make it easier for you to launch and run your security company business successfully, fully knowing what you are going into, and what’s needed to succeed in the business. This is a complete business plan for a security company business. It will be easier to plan and budget as you will be aware of all the costs involved in setting up and running the security business.
Uses of the Security Services Business Plan (PDF, Word And Excel)
The security company business plan can be used for many purposes including:
- Raising capital from investors/friends/relatives
- Applying for a bank loan
- Start-up guide to launch your security company business
- As a security company business proposal
- Assessing profitability of the security company business
- Finding a business partner
- Assessing the initial start-up costs so that you know how much to save
- Manual for current business owners to help in business and strategy formulation
Contents of the Security Company Business Plan (PDF, Word And Excel)
The business plan for security company includes, but not limited to:
- Marketing Strategy
- Financial Statements (monthly cash flow projections, income statements, cash flow statements, balance sheets, break even analysis, payback period analysis, start-up costs, financial graphs, revenue and expenses, Bank Loan Amortization)
- Industry Analysis
- Market Analysis
- Risk Analysis
- SWOT & PEST Analysis
- Operational Requirements
- Operational Strategy
- Why some people in the security company business fail, so that you can avoid their mistakes
- Ways to raise capital to start your security company business
The security company business plan package consists of 4 files
- Security Company Business Plan – PDF file (Comprehensive Version – 72 Pages)
- Security Company Business Plan – Editable Word File (Comprehensive Version – 72 Pages)
- Security Company Business Plan Funding/Bank Loan Version- Editable Word File (Short version for applying for a loan/funding – 42 pages)
- Security Company Business Plan Automated Financial Statements – (Editable Excel File)
The business plan can be used in any country and can be easily edited. The financial statements are automated. This implies that you can change eg the costs, salaries etc, and all the other financial statements will automatically adjust to reflect the change.
Click below to download the Contents Page of the Security Company Business Plan (PDF)

Testimonial 8
Just wanted to say I am very happy with the business plan and I will gladly recommend your products, thank you very much and have a great day.
Testimonial 1
StartupBiz Global provided a very professional and comprehensive business plan which I used for my business. The business plan was easy to edit, and I was able to get the funding which I wanted. I highly recommend their business plans.
Testimonial 3
I was extremely lucky to come across StartupBiz Global. Their business plan exceeded my expectations, and most importantly I was able to secure a loan from my bank. Thank you guys, now my dreams are coming true!
Testimonial 2
Many thanks for your incredibly efficient service and thorough business plan. I am very impressed with the business plan. Before I bought the business plan, I tried to do my own business plan – it was such a nightmare and it turned out badly, also not to mention the stress it caused me. I wish I knew about your website earlier!
Testimonial 7
I found Startupbiz Global online when I was in desperate need of a business plan. I was overwhelmed by the quality of the business plan, it’s comprehensive and well researched! I did not have to wait to get the business plan, I got it instantly after payment. I highly recommend Startupbiz Global, and would happily use them again in the future.
Testimonial 5
I was able to understand the business side of farming because of your business plan. You did extensive research; the business plan was well prepared and fully detailed. It made everything clear, and I have somewhere to start now. I am confident that I am going to succeed in my business because of the guidance from your business plan.
Testimonial 4
The business plan which I purchased from your website saved me TIME and MONEY! The layout of the business plan was excellent. The financial statements were detailed and easy for me to edit. I will come back to purchase another business plan soon.
Testimonial 6
I purchased a business plan from you, and I’m glad to inform you that I was able to get my loan, and I’m starting my poultry farming business on the 1 st of July. This was made possible because of your business plan. Thank you very much, you made my dream come true.
Get the Security Company Business Plan (PDF, Word And Excel)
Click Buy Now below to purchase using Paypal, Credit Card, or Debit Card. After you have purchased, you will immediately see the download link for the business plan package on the screen. You will also immediately get an email with the business plan download link. The Pre-written business plan package (PDF, Word, and Excel) costs $30 only!

If you want to purchase multiple business plans at once then click here: Business Plans Store.
The business plan package is a zipped compressed file containing the PDF, Word and Excel documents. To open the package after downloading it, just right click, and select Extract All. If you have any problems in downloading and opening the files, email us on [email protected] and we will assist you.
We wish you the best in your security company business! Check out our collection of business plans , and more business ideas .
Related Posts

Starting a Car Wash Business Plan (PDF)

Starting Pharmacy Business Plan (PDF)

Starting Quail Farming Business Plan (PDF)

Latest Innovations In Poultry Farming

Join our mailing list to receive the latest posts and updates from our website.
You have Successfully Subscribed!

Cyber Security Business Plan [Sample Template]
By: Author Tony Martins Ajaero
Home » Business ideas » Security Industry » Cyber Security

Are you about starting a cyber security company? If YES, here is a complete sample cyber security business plan template & feasibility report you can use for FREE .
Okay, so we have considered all the requirements for starting a cyber security business . We also took it further by analyzing and drafting a sample cyber security business marketing plan template backed up by actionable guerrilla marketing ideas for cyber security businesses. So let’s proceed to the business planning section.
Suggested for You
- Fire Protection Equipment Business Plan [Sample Template]
- Can You Work in Cyber Security With a Felony?
- How to Sell Cyber Security Services to Individuals and Companies
- How to Get Clients for your Cyber Security Company
- Ammunition Manufacturing Business Plan [Sample Template]
The internet is one innovation that has changed the world; and yet as helpful as the internet has been, it has also caused a lot of problems, as cyber crimes are being committed daily by either individuals or groups of people. The cyber crimes being committed range from financial, personal to national security issues and so many more.
They attack individuals, businesses and even the government by tapping calls, monitoring emails or hacking websites to extract sensitive information, which is why more efforts are being put in place to secure data from those seeking to use them for purposes that are against what the owner intends.
Starting a cyber security business is therefore a lucrative business to go into because individuals, businesses and the government need their data protected. However, to start this kind of business, you will need to have technical skills that will be needed to secure data or stop an ongoing attack for your client.
Due to the technical nature of this business and the need to understand what you will be getting into from the business aspect, it would be wise to consult a business consultant in the area where you intend starting the business.
This is to enable the business consultant go through your business concept and advise you on whether to proceed with the business or not. If your business concept is a great one, the business consultant would offer you tips and suggestions on the way forward.
Another important aspect that you would need to take care of before starting your business is writing a comprehensive business plan. A business plan is a document that shows holistically where your business is headed and if you will likely succeed with the business you intend to start.
Writing a business plan is however not an easy task especially the financial aspect, but it is important for your business. You can either hire the services of a business plan writer or go online to get a free business plan template to use as an aid in writing a business plan for your business. Below however is a sample cyber security business plan template for you.
A Sample Cyber Security Business Plan Template
1. industry overview.
According to Ponemon Institute, within the year 2015, the costs associated with cyber crime was 19% higher than it was in 2014. Globally, a hack in 2014 cost companies on the average $7.7 million. This has led 20% of companies globally to create cyber crimes budget between $1 million and $4.9 million depending on the scale of the company and ensure its strict implementation.
This has also led to huge investments in cyber security firms, as the first half of 2015 saw investors pumping nearly $1.2 billion into start-ups in this industry. According to forecasts, the investments were likely to reach $77 billion as at the end of 2015. The industry has also been pegged to reach $170 billion by the year 2022.
According to PricewaterhouseCoopers (PwC), globally, 58 percent of companies have an overall security strategy; 49 percent conduct periodic threat assessments, 48 percent monitor and analyze security intelligence actively. However, according to KPMG, 50 percent of CEOs globally with more than $500 million in revenue are usually not prepared as they should for a cyber attack.
However worrisome the threat of an attack externally is, companies now also have to worry about internal attacks from employees. According to a survey by SANS 2015, 74 percent of Chief Information Security Officers, CISOs are more worried about internal than external cyber attacks. According to a survey conducted by PwC, 34 percent of cyber attacks in 2015 were from current employees and 28 percent from former employees.
The damage caused by cyber crime is estimated to hit $6 trillion by the year 2022. This has led to a forecast that there will be an estimated increase in spending by companies for cyber security between the periods of 2017 and 2022 to $1 trillion. According to Gartner, as at 2016, more than $80 billion was spent on products and services related to cyber security. This is however expected to exceed $1 trillion globally within a five year period.
The cyber security industry is one that is fast paced as there is zero percent unemployment rate in this industry. The industry in fact has unfilled positions that are expected to reach 1.5 million by the year 2019. This shows that there is severe shortage of talent especially as more cyber crimes are being committed almost every other day as breaches continue to rise, with security incidents in 2015 at a 38 percent increase than as at 2014.
It has been estimated that by 2022, more than 4 billion people will be susceptible to attacks over the internet. The united states Government between the periods of 2006 and 2016 has spent over 0 billion. It also budgeted a whopping $14 billion in 2016 for cyber security.
According to Intel, the number of devices that will be connected might reach 200 billion in 2023; this is from the 15 billion connected devices in 2015. However, Microsoft and Cisco has countered the report claiming that only 50 billion devices will have been connected by 2022. Regardless of the estimated number, the report points to the same fact that more people will be online and will be vulnerable to cyber attacks.
2. Executive Summary
Kaboosh Tech is a standard and leading cyber security firm that is based in Mountain View – California here in the United States of America. We are in business to design cyber security solutions for our various clients – domestic and corporate. Asides from our core services, we also offer consultancy, training and technical support to our numerous clients.
Our location here in Mountain View – California is a very strategic one as we are in one of the most engaging tech communities in the whole United States of America, which therefore means that we are close to all the relevant tech companies, and other assorted stakeholders.
Our vision is to ensure that we are amongst the top five cyber security firms within three years of starting our business. We also intend to be known for our innovativeness in the cyber security world. We also intend to ensure that we are engaged in fair practices, which means that for the kind of business we would run, we intend to hold ourselves to a high standard so that our clients’ confidence in us won’t be misplaced.
In view of this, we are prepared to go the extra mile in ensuring that we build a solid business structure. We are prepared to source for and recruit only the best employees that will help grow and sustain our cyber security business.
Our management team is comprised of individuals with the best skills and experience. All those in the management team know what it means to ensure that a business such as ours is able to attain all its intended goals and objectives. Our management team believe in our values and philosophies and are fully committed to ensuring that we are a force to reckon with.
Due to the fact that we are in a very competitive industry, where being proactive is one of the factors that allows a business exist for long, we are always on the know about the trends in the industry and even intend to create a few trends as well within our one year of operation.
Finally, our Chief Executive Officer, Mr. Kab Oshe is one of the top cyber security men in the industry and has worked in several stints. He is known for not only for being innovative but for his business acumen as well. We are confident that with him at the helm we will be able to achieve all our set goals and objectives.
3. Our Products and Services
At Kaboosh Tech we intend to offer our customers forward thinking cyber security services that will enable them to remain ahead in whatever industry they are in.
However, because we are established to not only offer services but also generate revenue as well, we intend to increase our sources of income by offering additional services such as consultancy service and training. We intend to make as much profit as is legally permissible under the laws of the United States of America.
Below therefore are some of the services we intend to offer our various customers;
- Cryptography
- Programming
- System Hardening
- Consultancy and Advisory Services
- Technical Support
4. Our Mission and Vision Statement
- Our vision is to ensure that we are amongst the top five cyber security firms within three years of starting our business. We also intend to be known for our innovativeness in the cyber security world.
- In order for us to achieve our vision, we intend to build the best business structure that will see us employing only the best here at Kaboosh Tech.; our intention is to not only meet but exceed the expectations of our customers.
Our Business Structure
Due to the fact that we intend to build a standard cyber security firm here in Mountain View – California, we have put in place, plans and processes that would ensure that we get it right from the beginning as we intend to go the extra mile in picking the best employees to come and work with us at our firm.
Our management team is comprised of the best hands who have not only had several experiences in the industry that would be of huge benefit to our business but also has been attuned to our corporate goals and objectives and are willing to work to ensure that we are able to attain these goals and objectives.
Due to the fact that we would not be running a conventional cyber security firm especially in regards to the different services that we would be offering, we would be hiring more employees than necessary to handle the various roles and objectives that will crop up.
Below therefore is the business structure which we intend to build for our cyber security firm.
Chief Executive Officer
Administrative Manager
Human Resources Manager
Chief Information Security Officer
Security Administrator
Customer Service Executive
Marketing and Sales Team
Security Guard
5. Job Roles and Responsibilities
- Creates the right policies and strategies that will lead the direction of the firm
- Assembles the right management personnel and delegates certain responsibilities to them for the benefit of the firm
- Meets and negotiates with high level clients on behalf of the firm
- Ensure that the administrative functions are performed smoothly
- Ensures that other management staff are aligned with company policies at all times
- In charge of the day-to-day affair of the firm
- Prepares financial information, statements and reports on behalf of the firm
- Carries out internal audit and financial forecast
- Prepares tax documents and ensures that it is submitted to the right authorities
- Sources for, interviews and recruits competent and experienced employees to work for the firm
- Creates human resource policies and ensures that they are strictly adhered to
- Ensures that employees undergo training as at when due and that periodic performance appraisals are also conducted
- Responsible for establishing the vision of the organization and creates strategy to ensure that the organization’s information and technologies are protected
- In charge of developing strategies and policies that will handle security related incidents
- Allocates security resources efficiently and for the overall benefit of the organization
- Responsible for creating system defense against unauthorized access or modifications from external threats
- Configure the right security tools such as anti-virus software, firewalls and patch management systems on behalf of the firm
- Performs on behalf of the firm, vulnerability and networking scanning assessments
- Responds correctly to customers inquiries and orders
- Remains aware and informed of company policies as well as industry trends in order to give customers accurate information
- Keeps an updated customer database for the firm
- Responsible for conducting market survey that would determine new target markets for the firm
- Meets with and negotiates with clients on behalf of the firm
- Conducts direct marketing and sales with a view to generating revenue and attaining the corporate sales goals of the firm
- Ensures that the premises remains clean at all times
- Ensures that cleaning stock are always in supply and that depleted stock are replenished
- Carry out any other duty as might be assigned by the management
- Patrols the premises and ensures that it is free from any form of trespassers
- Watches the surveillance camera in order to forestall any suspicious activity or person
- Carries out any other duty as might be determined by the management
- Runs official errands on behalf of the firm
- Ensures that traffic rules and regulations are obeyed and a logbook kept on behalf of the firm
- Carries out preventive maintenance on the vehicle on behalf of the firm
6. SWOT Analysis
Our intention to build a standard and world class cyber security firm here at Mountain View – California has led us to seek the services of a reputable business consultant who understands the market thoroughly to take a look at our business concept and determine if we are likely to survive in the industry we intend going into.
Using four major attributes to analyze our business – strengths, weaknesses, opportunities and threats – the business consultant was able to bring our some facts that we are going to use in determining how well placed we are to start this business.
Therefore the results of the SWOT analysis conducted on behalf of Kaboosh Tech are;
Our strength lies in the fact that we are offering various services to all our customers, which has made us get a huge share of the market and to effectively compete against our competitors. Our employees are not only creative but very capable in ensuring that we are not only able to meet the demands of our customers but that we are able to surpass them as well.
Our employees are amongst the best paid in the industry of cyber security and especially amongst start-ups, this has led to our brand becoming well known in the short while that we have started. Our chief executive officer has a vast experience in this industry and has worked in various capacities in other cyber security firms and will therefore bring the right experience to bear for our firm, thereby allowing us to attain our goals and objectives.
The cyber security business is a crowded one and so it will not be so easy for us to break into this market, even as strategic as our location is. Also, because we are basically a new business, we do not have the staff strength and financial resources that will enable us effectively compete against our competitors.
- Opportunities
The cyber security market is one that has plenty of opportunities both at making a name or at making money and we fully intend to explore both. We will conduct a market research that will enlighten us more on the opportunities available to us and how we can use that to our advantage.
There are several threats that we are likely to face when starting or running the business and the first is the fact that we are going to face competitors with similar services coming to our location to start up their business. Another threat we are likely to face is with changing trends, but we will ensure that we do all we can to always be proactive so that we can easily adapt to trends.
7. MARKET ANALYSIS
- Market Trends
The healthcare sector was not spared in 2015 as it was struck by major breaches that saw 80 million records being compromised. This didn’t just start in 2015, because since 2009, close to one-third of Americans have been victims of breaches in several healthcare companies. This act has led many healthcare companies to invest more in cyber security so as to protect the data of their customers.
There are majorly two types of threats that companies face, and there are inside and outside threats. Inside threats are usually carried out by a company’s current or former employee. According to PricewaterhouseCoopers (PwC), more than 34 percent of the cyber attacks that occurred in 2015 were from current employees who were still working with the firm while about 28 percent were from former employees.
Outside cyber attacks however are often carried out by hackers, activists, government agencies and organized crime outfits amongst other kinds of people and they are usually carried out within minutes while using several methods such as RAM scraping, phishing, spyware or credential theft.
8. Our Target Market
Almost everyone who has connected devices is susceptible to cyber attacks, which would be basically everyone in the United States of America. However, in order to have an accurate data as regarding those who we would be focusing on, we intend to conduct a market research that will allow us know who our true target market are and who might be our target market in the near future.
The market research we intend to conduct however will allow us identify what is expected from us by the target market and what we should expect from them as well. In view of this, we are therefore in the cyber security market to offer our services to the following groups of people and businesses;
- Healthcare companies
- Financial institutions
- Government agencies
- Tech Companies
- Celebrities
- Small businesses
- Educational institutions
- Political organizations
Our competitive advantage
Our intention of starting Kaboosh Tech is to ensure that we offer our clients cyber security services that will allow them remain proactive ahead of their attackers. We intend to be amongst the top five preferred brands by our target market and among the top three cyber security firms in the United States of America. However, in order for us to achieve this feat, we have come up with several competitive strategies that will allow us to favorably compete against our competitors.
We understand the cyber security market and most of our products are preventive in nature, which causes more companies to prefer our security designs that will allow them remain proactive in business.
We have a vast number of experienced people on board who understand the cyber security market and who know how to bring our start-up from scratch to become a major force to be reckoned with in the industry and amongst consumers. We are constantly ensuring that our employees remain stimulated enough in order to not only meet but exceed the expectations of our clients; both corporate and domestic.
We have ensured that not only is our facility strategically located here in Mountain View – California but also that we create an environment that is not only conducive but one that mentally stimulates and brings out the creative juices for the sustainability and growth of our business.
Our employees are also well paid better than what similar start-ups here in Mountain View, Palo Alto, and Silicon Valley are paying their employees. Also, we are in tune with trends and ensure that all our employees go through training and attend seminars every now and then so as to enhance their skills, thereby boosting productivity for our company.
9. SALES AND MARKETING STRATEGY
- Sources of Income
Kaboosh Tech is a cyber security firm that has been established with the sole intention of generating revenue and maximizing profit in the cyber security industry here in Mountain View – California. We intend to ensure that we make as much profits as we can not only in the United States of America but all over the world as well.
Kabbosh Tech will therefore generate income by offering the following services;
10. Sales Forecast
Cyber crimes have led to a lot of companies and individuals investing more in cyber security in order to protect their data and sensitive information.
Our location in Mountain View – California is very strategic as we are in one of the tech communities and so have a lot of opportunity to generate the necessary revenue that will not only sustain our business but have us making enough profits in our first six months of operation.
We however carried out a critical examination of the cyber crime market cum software and tech industry in order to determine our chances in the market and what our sales forecast is likely to be. In conducting our sales forecast, we made use of information and assumptions from similar start-ups not only here in Mountain View but also in other tech communities here in California.
Therefore, the sales projections for Kaboosh Tech based on the data and information gathered are as follows;
- First Fiscal Year-: $500.000
- Second Fiscal Year-: $950,000
- Third Fiscal Year-: $2,000,000
N.B : Our projected sale is very moderate compared to what we are actually going to make but we chose to be on the safe side. The assumptions used in this instance were that there won’t be any competitor within the time period and that we would not change locations too. Should however any of the assumptions change, the sales projected figures would either increase or decrease.
- Marketing Strategy and Sales Strategy
Marketing is a very important aspect for any business either new or existing as this is where revenue for the business is not only generated in order to sustain and grow the business, but awareness for both existing and new customers for the business is created as well. The importance of marketing has seen businesses keeping a separate budget and creating marketing policies and strategies that will allow it to stand out in the market place.
In view of this, we are conducting a thorough marketing strategy that will enable us know who our target market is, what it is they want from us, and what we should expect from them. The marketing research is also essential because it would allow us know what strategies would be effective in the short and long run and how much we would need to set aside as a marketing budget that will allow us compete favorably against our competitors.
In this regard, we have engaged the services of a reputable marketing consulting firm here in Mountain View who have dealt with firms such as ours and created marketing strategies that were effective for them. Our choice of using a marketing consulting firm rose from the fact that as this is an intensely competitive industry, we would need all the help we can get to position our business to a standard that will allow us to achieve all our goals and objectives.
We also intend to empower our marketing and sales team to ensure that marketing strategies created for the firm are in line with our core values, goals and philosophies and will seek to promote our brands at all times. Our marketing team has the right therefore to modify or remove ineffective strategies that might harm the firm in the long run.
Therefore, the following are the marketing strategies that we will adopt at Kaboosh Tech;
- Formally introduce our cyber security firm by sending introductory letter to healthcare companies, financial institutions, government agencies, tech companies and other stakeholders in the cyber security market
- Throw an elaborate party to launch our cyber security firm in such a way as to generate awareness about our firm
- Place adverts in local and national newspapers and tech magazines as well as on radio and television stations about our cyber security firm
- Engage in direct marketing and sales by negotiating with clients
- Install billboards in strategic locations all around Mountain View and around California as well
- Use our social media platforms and other tech platforms to vigorously market our cyber security firm
11. Publicity and Advertising Strategy
Due to the intense competition in this industry, cyber security firms that do not engage in the right publicity are bound not to survive long in the business. While publicity and advertising is very important for any business, knowing the right strategies to use due to the nature of the business will ensure that corporate goals and objectives are easily adhered to.
In regards to this, we have engaged the services of a reputable publicity consulting firm here in Mountain View – California with the right knowledge and expertise to help us draft strategies that will not only promote the brand of our company, positively communicate our brand and allow us stand out but one that will allow us to compete favorably against our competitors.
Therefore, some of the publicity and advertising strategies that we would use to promote Kaboosh Tech are;
- Attend seminars and relevant tech and software conferences in order to network and increase awareness about our brand
- Develop trial versions of our cyber security products for users and have them buy the original as soon as they are satisfied with the services from our products
- Use social media platforms such as Facebook, Linkedin, Google Plus and Twitter to vigorously promote our brand
- Create an interactive website and promote contests from our brand or from other brands
- Participate in and sponsor relevant community programs here in Mountain View – California
- Distribute handbills and fliers in strategic locations here in Mountain View
12. Our Pricing Strategy
Determining the right price for our products and services here at Kaboosh Tech will depend on a whole lot of factors such as how strong our products are, what category of products and services our customers will be demanding, how unique the products are, what our competitors are offering and what our overhead and running expenses would be.
Because of how competitive the market is, we intend to offer discounted price on some of our products as well as other incentives for the first two months of operation in order to increase the awareness for our product and attract more customers to purchase from us. Even though we would be offering a discounted price, our analysis has shown that while we might be having a low gross margin, we would not be running at a loss.
- Payment Options
Due to the high value we have for our customers and how sweet we want their experience at our company to be, we at Kaboosh Tech have come up with different payment options that will suit all our various customers and whatever preferences they might have.
Therefore, the payment options that we intend to make available to our various clients are;
- Cash payment
- Payment via check
- Payment via online payment portal
- Payment via Point of Sale (POS) Machine
- Payment via bank draft
- Payment via credit card
- Payment via crypto-currency
The above payment options were deliberately chosen to be able to cater to the diverse needs of our clients and they suit our business too. We intend to assure our customers that these platforms will work smoothly without hitches of any sort.
13. Startup Expenditure (Budget)
The cyber security business is not such a hard business to start but if however you intend setting up a business that is standard then you would need to spend a bit more in ensuring that the most important aspects are well covered. Mostly the bulk of the capital would be used in procuring equipment, leasing a facility, buying a van and paying the salaries of employees for a defined period of time.
Therefore the key areas where we intend to spend our start-up capital on are;
- Total fee for registering Kaboosh Tech in the United States of America – $750
- Obtaining of the necessary licenses, permits, accounting and customer software as well as other legal expenses – $2,250
- Insurance policy (general liability, workers’ compensation and property insurance) – $2,000
- Leasing of a facility for use for at least five years and carrying out renovations – $100,000
- Cost of hiring a business consultant – $2,000
- Operational cost for the first 3 months (salaries of employees and payment of utility bills) – $150,000
- Other start-up expenses which includes (virus detection software, bug tracking, anti-viruses, software subscription and cable broadband) – $15,000
- Marketing promotion expenses (general marketing expenses and promotion activities towards the grand opening ceremony of Kaboosh Tech – $5,000
- Administrative expenses (stationery, phone, computers, printers, furniture, business cards, office supplies, and stamps) – $30,000
- Cost of purchasing an official fairly used van – $20,000
- Cost of launching a website – $1,000
- Cost of throwing a grand opening party – $5,000
- Miscellaneous – $8,000
From the above analysis, it is apparent that we need an estimate of $341,000 if we intend to start and run a standard and successful business here in Mountain View – California. It should be noted that the bulk of the capital will go into leasing a facility for a period of five years, paying the salaries of employees as well as utility bills for a period of three months, purchasing a van for official errands as well as getting the necessary equipment to start our cyber security business here in Mountain View – California.
Generating Funding/Startup Capital for Kaboosh Tech Business
Kaboosh Tech is fully owned and run by Mr. Kab Oshe. Due to the fact that we do not intend to seek for an external investor to be part of our business, we will therefore source for funding from other sources. The following are the different areas where we intend to source our start-up capital from;
- Generate part capital from personal savings and sale of stocks
- Source for part capital from online crowdfunding sites
- Apply for loan from commercial bank
N.B : We got the sum of $100,000 from our personal savings and sale of stocks. We registered in a crowdfunding site and were able to generate the sum of $100,000 for our cyber security business. We have been able to secure the sum of $141,000 from our commercial bank after signing several documents. The loan is to be repaid in 7 years at the rate of 3% per annum.
14. Sustainability and Expansion Strategy
Ensuring that our business not only exists but is sustained for as long as we want to remain in business is a priority to us and we have therefore concentrated on the factors that we know will enable us sustain and expand our cyber security business here in Mountain View – California. The factors that we intend to concentrate on are ensuring that we build the right business structure, engage in effective publicity and advertising strategies, as well as ensure that we retain a high percentage of our clients.
Finally, we understand that without our customers, our business is going to fail, and so we pay a high amount of attention to our customers. We understand how important they are to our business and we will ensure that all employees adopt an excellent customer culture.
Check List/Milestone
- Business Name Availability Check: Completed
- Business Registration: Completed
- Opening of Corporate Bank Accounts: Completed
- Securing Point of Sales (POS) Machines: Completed
- Opening Mobile Money Accounts: Completed
- Opening Online Payment Platforms: Completed
- Application and Obtaining Tax Payer’s ID: In Progress
- Application for business license and permit: Completed
- Purchase of Insurance for the Business: Completed
- Conducting feasibility studies: Completed
- Generating capital from family members: Completed
- Applications for Loan from the bank: In Progress
- Writing of Business Plan: Completed
- Drafting of Employee’s Handbook: Completed
- Drafting of Contract Documents and other relevant Legal Documents: In Progress
- Design of The Company’s Logo: Completed
- Graphic Designs and Printing of Packaging Marketing/Promotional Materials: In Progress
- Recruitment of employees: In Progress
- Creating Official Website for the Company: In Progress
- Creating Awareness for the business both online and around the community: In Progress
- Health and Safety and Fire Safety Arrangement (License): Secured
- Opening party/launching party planning: In Progress
- Establishing business relationship with vendors – wholesale suppliers/merchants: In Progress
- Purchase of trucks: Completed

Home » How to Start a Cybersecurity Business: Building a Secure Future
The Yale Ledger is a student-led magazine showcasing content from around the Yale community.
If you are affiliated with the Yale student community and have an article you want to share, please email Layla Winston .
If you notice any spam or inappropriate content, please contact us so we can remove it.
- August 2024
- February 2024
- January 2024
- December 2023
- November 2023
- October 2023
- September 2023
- August 2023
- February 2023
- January 2023
- December 2022
- November 2022
- October 2022
- September 2022
- August 2022
- February 2022
- January 2022
- December 2021
- September 2021
- August 2021
- February 2021
- January 2021

How to Start a Cybersecurity Business: Building a Secure Future
As the digital landscape continues to expand, the importance of cybersecurity has become paramount. With increasing cyber threats and data breaches, the demand for robust cybersecurity solutions is on the rise. If you have a passion for technology and a desire to protect individuals and businesses from cyber threats, starting a cybersecurity business can be a rewarding and lucrative venture. A cyber security consultant can help protect systems and networks against cybercrime. In this article, we will outline essential steps to help you embark on the path of launching your cybersecurity business successfully.
1. Acquire Expertise and Knowledge
Cybersecurity is a complex field that requires a deep understanding of information security, network infrastructure, risk assessment, and threat intelligence. Obtain relevant certifications, such as Certified Information Systems Security Professional (CISSP) or Certified Ethical Hacker (CEH), to demonstrate your expertise and credibility. Continuously invest in your knowledge by staying updated with the latest security trends, technologies, and best practices.
2. Identify Your Niche and Target Market
The cybersecurity industry encompasses various areas, including network security, data protection, incident response, vulnerability assessment, and more. Determine your specialization based on your skills, interests, and market demand. Research and identify your target market, whether it’s small businesses, healthcare organizations, financial institutions, or government agencies. Understanding your niche and target audience will enable you to tailor your services effectively.
3. Develop a Comprehensive Business Plan
Create a detailed business plan that outlines your goals, target market, competition analysis, pricing strategies , marketing approach, and financial projections. A well-crafted business plan serves as a roadmap and helps attract investors or secure funding if needed. It also helps you establish a clear direction for your business and sets you up for long-term success.
4. Establish Legal and Operational Frameworks
Set up your business legally by registering it as a legal entity, obtaining necessary licenses and permits, and complying with data protection and privacy regulations. Consult with legal professionals specializing in technology and cybersecurity to ensure your business adheres to all legal requirements. Additionally, establish operational frameworks, including cybersecurity policies and procedures, employee contracts, and service level agreements (SLAs) to provide structure and accountability.
5. Build a Talented Team
Assemble a team of skilled professionals with expertise in different cybersecurity domains. Seek individuals who possess relevant certifications, industry experience, and a passion for cybersecurity. Invest in ongoing training and professional development to keep your team updated with the latest threats and technologies. A competent and well-rounded team will help you deliver comprehensive and effective security solutions to your clients.
6. Offer Comprehensive Services
Cybersecurity encompasses a wide range of services, including risk assessments, penetration testing, incident response, secure network design, security awareness training, and compliance audits. Determine the services you will offer based on your expertise and target market. Start by offering a core set of services and gradually expand your offerings as your business grows.
7. Invest in Infrastructure and Tools
To provide reliable and efficient cybersecurity services, invest in robust infrastructure and cutting-edge tools. This includes secure network architecture, advanced threat detection systems, vulnerability scanning tools, encryption software, and secure communication platforms. Cyber security is a booming market. Choose tools that align with your service offerings and provide the highest level of protection for your clients’ data.
8. Develop Strong Partnerships
Forge strategic partnerships with other technology service providers, such as IT companies, managed service providers (MSPs), or cloud service providers. Collaborating with complementary businesses can help you expand your reach, access new clients, and provide comprehensive solutions. Additionally, consider joining industry associations and participating in cybersecurity communities to network with peers and gain industry visibility.
9. Market Your Business
Develop a robust marketing strategy to promote your cybersecurity business. Create a professional website that highlights your services, expertise, and client success stories. Utilize digital marketing techniques such as search engine optimization (SEO), content marketing, social media, and targeted online advertising to reach your target audience. Leverage thought leadership by publishing insightful content, speaking at industry events, and engaging with cybersecurity communities.
10. Focus on Client Relationships and Trust
Building strong client relationships based on trust and reliability is vital in the cybersecurity industry. Deliver exceptional service, prioritize proactive communication, and consistently exceed client expectations. Focus on long-term partnerships and emphasize the importance of cybersecurity to your clients’ businesses. Word-of-mouth referrals and positive testimonials can significantly contribute to the growth of your business.
Starting a cybersecurity business requires expertise, dedication, and a commitment to staying ahead in an ever-evolving landscape of threats. By acquiring the necessary knowledge, identifying your niche, developing a comprehensive business plan, assembling a skilled team, offering comprehensive services, investing in infrastructure, building strong partnerships, and implementing effective marketing strategies, you can position your cybersecurity business for success. Remember, cybersecurity is an ongoing battle, and your business’s ability to adapt, innovate, and protect clients will determine its long-term viability.
Powered by WordPress / Academica WordPress Theme by WPZOOM
Creating a comprehensive cyber security plan template for small businesses: A step-by-step guide for protecting your business from cyber attacks

A cyber attack is disastrous for businesses. This is even more true for small businesses without the proper security strategies in place.
Luckily, you can protect your business from unwanted threats with a cyber security plan template for small business success.
Keep reading to learn about the importance of strong cyber security practices and find out how you can create your own plan.
What is a cyber security plan template for small business?
A cyber security plan template for small business outlines everything you need to protect your business from cyber security threats.
Our research indicates that any effective cyber security plan includes both preventative and reactionary measures for cyber-attacks and breaches.
What is the purpose of the cyber security plan template for small business?
There are many reasons behind a cyber security plan template for small businesses. As per our expertise, preparing against security threats is crucial to reduce risk as your company grows.
In general, a cyber security plan takes three factors into account.
- Technologies: Downloading protection software for your devices.
- Processes: Educating your team and enforcing security policies.
- Access controls: Segmenting your business information, and giving access to only those who need it.
Focusing on these three factors, a cyber security template clarifies the different kinds of security risks you need in order to protect your company.
Why you need a cyber security plan
Every day, your team relies on business data to keep operations moving. This includes:
- Customer information.
- Financial data.
- Sales history.
If you lose this data to a cyber security breach, you risk losing your business.
Unfortunately, no business is immune to cyber security threats! Our findings show that even organizations at the forefront of their industry have fallen victim to this.
But it’s a lesser known fact that small and medium businesses are the prime targets for cyber attacks.
“43% of cyber attacks target small businesses.” – Cybint , 2022.
A cyber security strategy is your first line of defense against these attacks. A complete security plan prevents cyber attacks, and provides quick solutions when required.
Based on our firsthand experience, the more secure your organization, the more trust customers have in your product or service. And more trust leads to more sales .
For example, companies with log-in websites often implement two-factor authentication for their users. This adds an additional level of security, as it requires more than just a password for access to your system.
Without proper security procedures, both your physical computers and online accounts are at risk of security breaches. And through our practical knowledge, if you don’t take advantage of antivirus resources, for example, entire operating systems can crash on you.
Usually, companies that thrive in cybersecurity have systems in place that prevent and solve security issues. And drawing from our experience, you can achieve both with an incident response plan.
Planning for the worst saves you time and stress. More importantly, it clarifies exactly what actions you need to take in the event of an emergency.
The more concise your plan, the better your business will be at handling cybersecurity responsibilities.
Local network security devices like firewalls are key in filtering the connection between your private network and the public Internet.
Encryption of sensitive files on your computer, or within applications, is another key factor to consider. Any file or program that contains customer data is important to protect.
Let’s take a look at the cyber threats that can affect your business below.
Common cyber threats for small businesses
Of course, one of the requirements for creating a cyber security plan template for small business protection is to understand your business’ risk.
To identify your possible vulnerabilities, you need to know what threats are out there. Our research indicates that these are the most common cyber security threats for small businesses.
Malware attacks
Malware is the biggest cyber threat for small businesses today.
The term itself is broad and refers to all categories of malicious software meant to harm devices or networks.
Three common types of malware attacks include:
- Ransomware.
Let’s dive deeper into each one.
In short, a virus is a piece of computer code meant to harm your technological equipment. Computer viruses affect your devices in many ways, including:
- Corrupting or deleting files.
- Damaging computer programs.
- Slowing down device performance.
- Causing excessive pop-up windows.
In your cyber security plan template for small business, there are several benefits to highlighting the signs when a device has become infected with a virus.
What’s more is that there are several ways that your devices can catch a virus, such as:
- File sharing.
- Downloading harmful software.
- Infected emails.
Viruses used to be the only cyber threat that businesses worried about, but cyber security has evolved and now includes other attack strategies.
Ransomware attacks
Ransomware is malware where hackers access your data and hold it for ransom by encrypting it. You then pay them to decrypt your data and regain access.
So, if your business experiences a ransomware attack, your products or services provided will likely come to a screeching halt.
A surprising statistic:
“Ransomware is the third most popular type of malware used in data breaches.” – Verizon , 2020.
Our findings show that this will do more than just affect your numbers. Depending on the information that the hacker gathers, a ransomware attack can be tragic for your small business. It could cost you everything to pay off the hacker.
Unfortunately, even if you comply with the hacker, there’s a chance that they won’t keep up their end of the deal. They may ask for additional payments, or cut communications once they have what they want.
Spyware is a type of malware that collects information from your device without your knowledge. Based on our observations, it’s difficult to detect, and many people never know that they’ve been subject to a spyware attack!
With spyware, cyber criminals can not only oversee your business operations. Data privacy and data security become a pipe dream as well.
Since it’s invisible, once spyware has been downloaded to a device, there is little you can do to restore your network security.
One of the most common ways spyware hackers install spyware is through phishing emails.
Phishing scams
Unlike the other attacks on this list, phishing isn’t software. Phishing is a technique used to gather sensitive information through deception.
The act of convincing someone to disclose information to a hacker is called social engineering.
The most common case of phishing involves sending emails with links that lead to a website infected with malware. These scams can affect consumers and businesses alike.
A common social engineering strategy is to trick recipients to reply to emails with personal information by pretending to be a credible source, such as a colleague.
Our findings show that cyber criminals often claim to have management roles in the businesses they target. A similar strategy involves impersonating a company that has a strong reputation.
As per our expertise, it’s important to include strategies to prevent phishing attacks in your cyber security plan template, most of which surrounds employee education (more on this later).
The state of your cybersecurity hinges on making a plan. Let’s jump into how to create a cyber security plan for small business.
How to create your business cyber security plan
Creating a security plan requires you to look at your current business processes to figure out your vulnerabilities.
From there, you can put together a plan to eliminate those vulnerabilities and reduce your risk.
You might think as a relatively unknown “small biz” that you’re safe against cyberattacks. In reality, it’s small business cybersecurity that cybercriminals target most. This is because a small organization tends to have much weaker cyber security than a larger enterprise.
It’s a good idea to use a cyber security plan template for small business through this process. Through our practical knowledge, templates for your business’ cybersecurity plan are useful tools as they eliminate internal confusion over protocols and best practices.
To guide you, here are 5 key steps to creating your plan.
1. Identify your biggest threats
Of course, drawing from our experience, protecting your company from cyber threats requires more than just filling out a planner.
Creating a cyber security plan is similar to setting your sales goals . For example, both involve taking every aspect of your business into account.
You can’t create a line of defense if you don’t know what you need defending from.
This is why the first step in creating a cyber security plan for small business is to understand your business risk.
The most common threats for small businesses include:
- Ransomware.
- Weak passwords.
Our research indicates that identifying your risks helps you find ways to prevent these risks from happening. This includes solutions, such as:
- Antivirus software.
- Newer devices with updated security features (i.e., fingerprint scanning).
- Password parameters.
If you have an IT team, this is a job for them. If not, consult an IT professional to identify your exposure and create a plan.
2. Prioritize your assets
Cyber security asset assessment involves identifying your IT assets and potential security risks. Your assets include traditional devices as well as digital assets.
Here are some examples of common business assets to consider:
- PCs and mobile devices.
- Networks and servers.
- Cloud-based data.
In reality, any part of your IT infrastructure is at risk of cyber security threats, so be sure to create a comprehensive list.
From there, decide which assets are the most important. That way you can determine the most vulnerable ones to begin creating your security plan.
3. Set your goals
The goal of your security plan is to protect your small business. However, several smaller goals play into this larger objective.
In a perfect world, creating a plan to prevent cyber attacks, and including a network security device like a firewall, would be enough. However, solely relying on prevention is unrealistic.
As much as you try to prevent cyber security attacks, there’s always a risk of cyber attackers getting through your defense. So, as per our expertise, your goals should also include optimal readiness to respond to threats.
If you’ve already made the plans to handle unauthorized users in your system, then you’ll greatly reduce the amount of damage they can do.
Of course, malware detection is the first step once your cybersecurity is breached. So planning the ways to detect threats is as important as planning how to deal with them.
Better yet, our research indicates that you should have a goal for your recovery time to minimize your exposure and damage to your assets.
4. Document your plan
Once you’ve determined your current cyber security risks and created a business plan to improve your response readiness, it’s time to document your plan.
Based on our firsthand experience, documenting is easy if you use a cyber security plan template for small business, as you just have to fill in the sections in the template.
There are several reasons why documenting cybersecurity plans is important.
For starters, you don’t want anything to slip through cracks when it comes to a cyber security plan for small business. It only takes one small slip-up for a hacker to access your information.
Thoroughly documenting your plan minimizes the risk of overlooking an aspect of your business, and removes the possibility for any intrusion into it.
Sometimes, you’ll have conversations with your customers that are difficult . But nothing’s harder than explaining that your cyber security has been compromised. A well-documented plan softens the blow and reduces a breach’s impact.
What’s more, employee training plays a huge part in your cyber security strategy. So, document your plan in a way that’s easy to understand.
5. Do a test run
Once you have the proper cyber security infrastructure in place that your employees are trained on, test your plan.
Don’t forget to test your employees’ ability to recognize threats by sending test phishing emails. You can also simulate a ransomware attack through encryption of your own files.
It’s important to note that cyber security is always evolving. Once you confirm that your new plan works, set up a schedule to conduct regular tests to ensure up to date strategies.
Now that you know how to create your plan, let’s explore what to include in your template.
What to include in your cyber security plan template for small business
Making a cyber security strategy is no small task. There are two points to remember about your plan:
- It’s a document your team regularly references.
- The security of your business depends on it.
Organizations that acknowledge these points always have the most robust security strategy, making them the most cyber secure. To address these two factors, you want to ensure that you include as much detail in your plan as possible.
Using a cyber security plan template for small business simplifies the process and ensures that your plan captures every aspect of your business.
Since this plan will be included in the core employee resources of your organization, a template ensures that you’ve covered all your bases in a way that’s still easy to follow.
Here’s what to include in your template.
Your objectives
To kick things off, your cyber security plan for small business protection should open with your goals.
Your goals guide your plan, so clearly stating them at the start gives context to your proposed strategies.
As a result, the reader sees the bigger picture and better understands the importance of cyber security strategies.
Common threats
To fully understand your cyber security strategies, you need to outline your business’ security threats.
Make sure that your plan describes each threat to your business. This means associating each common threat with an asset.
For example, one common threat to small business security is password hacking, and one of the assets at risk is your company’s data. Knowing this, you can strengthen your employee passwords to prevent data breach.
Identifying threats specific to your business is a crucial step in protecting your staff and your customers from cyber attacks.
Security policies
Cyber security policies serve as the framework of your plan.
Policies outline how you expect your team to protect your business assets. Some basic security practices include:
- Limiting who accesses information.
- Restricting internet browsing on your network.
- Implementing a plan of action for suspicious emails.
There are also companies that offer products or services, like antivirus software to ward off security threats.
Your security policies are mainly preventative, so you should consider how to react to security breaches.
Breach response plan
Prevention is the best tool to protect your business, but it shouldn’t be your only tool. If your business does become the victim of a cyber attack, you should have a plan of how you’ll react.
When unauthorized users infiltrate your business systems, panic sets in. It becomes difficult to think clearly and act accordingly.
Without an established breach response plan, you’ll lack the tools to quickly restore your business.
A breach response process allows you to identify an attack and shut it down as soon as possible. This reduces damage to your business data and ensures that you’re back up and running in no time.
Your breach response plan should include clear steps and a timeline of how long you have to shut down an attack before your business is at risk.
Employee education plan
You can have the tightest cyber security policies in place, but if your employees don’t know them, your business is still exposed.
So, it’s important to implement a system that educates your employees. A cyber security plan for small business isn’t complete without employee training.
To be successful, your employees need to be up to speed on your business’ cyber risks and security policies. Design a cyber security training program to walk your employees through these.
A complete employee education plan results in your employees:
- Creating strong passwords.
- Recognizing phishing emails.
- Resisting other social engineering techniques.
- Knowing what to do if they accidentally disclose information.
Highlight your training plan in your cyber security plan template for small business.
For best results, conduct a cyber security training at least once a year and test employees’ knowledge monthly.
Wrap up: Cyber security plan template for small business success
The truth is that if you don’t have a solid cyber security plan for small business, you risk losing your business completely.
With this in mind, it’s important to prioritize cyber security policies and implement them into your business process. The applications of this plan will guarantee longevity for your business.
The key content of a complete plan includes:
- Clear goals.
- Potential threats.
- Security policies.
- A breach response plan.
- Employee training.
The health of your cyber security depends on these five factors for a number of reasons. Establishing each of these now means that you can quickly shut down unauthorized user or activities within your business down the road.
The quality of your product or service means nothing if your cyber system is unsecure.
With the support of a template, your cybersecurity plan is clear, concise, and comprehensive. It allows you to draft and organize all the content that your plan requires.
Free cyber security plan template for small businesses
Protect your business from cyber attacks by drafting a robust cyber security plan.
If you don’t see the download form, download template here .
Brush up on other technology trends for your small business in this blog !
Cyber security plan template for small business FAQs
How do i implement a cyber security plan for small business.
To implement a cyber security plan for your small business, the most important step is educating your employees. Once your plan has been created, the hard part is done.
Make your cyber security plan customary and accessible so that your employees know about your business’ strategies in the event of a cyber threat.
If you’re unfortunate enough to experience a cyber threat, remind your staff of your plan– then follow each step closely.
How do I choose the right cyber security products for my small business?
To choose the right cyber security products for your small business, first identify all your company’s potential cyber threats. Once those are established, there are many security products to choose from.
There is not a one-size-fits all solution to cyber security. You can choose which products suit your needs, but it’s important to note that you can never be too secure.
Many cyber security companies offer free trials, so consider experimenting with different products to find the perfect fit for your business.
Where can I find a cyber security plan template for small business?
For a comprehensive cyber security plan template for small businesses plus more, simply:
- Follow this link .
- Fill out your business’ basic information.
- Click download.
Keep your data more secure with a free trial of Method:CRM.
Image credit: cottonbro via Pexels .
About The Author
Shana Cesaire
Related posts.

3 ways you win with QuickBooks mobile access

Conference Travel Tips to Get You There Energized
Streamline your business with method.
Start your free trial — no credit card, no contract.

Cyber Security Plan Template

What is a Cyber Security Plan?
A cyber security plan is a structured approach to protecting an organization's data, systems, and networks from malicious cyber threats. It outlines the processes, procedures, and technologies in place to protect the organization's digital assets from unauthorized access, theft, and malicious damage. It also outlines the steps to take in the event of a security breach.
What's included in this Cyber Security Plan template?
- 3 focus areas
- 6 objectives
Each focus area has its own objectives, projects, and KPIs to ensure that the strategy is comprehensive and effective.
Who is the Cyber Security Plan template for?
The Cyber Security Plan template is designed to help IT security teams in organizations of all sizes and industries create a cyber security plan company-wide. It provides a comprehensive structure to define objectives, set measurable targets (KPIs), and implement related projects to achieve those objectives.
1. Define clear examples of your focus areas
A focus area is a broad topic that you want to address in your security plan. Examples of focus areas include increasing cyber security, reducing data loss, and strengthening authentication.
2. Think about the objectives that could fall under that focus area
Objectives are the goals that you want to achieve within each focus area. They should be well-defined and measurable to ensure that the security plan is effective and trackable. Examples of some objectives for the focus area of Increase Cyber Security could be: Develop organizational cyber security plan, and Implement security protocols.
3. Set measurable targets (KPIs) to tackle the objective
Key performance indicators (KPIs) are the metrics that you will use to measure progress towards objectives. They should be relevant, measurable, and achievable in order to ensure successful completion of objectives. An example of a KPI for the focus area of Increase Cyber Security could be: Increase security assessment score from 65/100 to 90/100.
4. Implement related projects to achieve the KPIs
Projects (actions) are the steps that need to be taken to achieve objectives. Each project should have a defined timeline and a designated person responsible for its completion. An example of a project related to Increase Cyber Security could be: Conduct security assessment.
5. Utilize Cascade Strategy Execution Platform to see faster results from your strategy
Cascade is a strategy execution platform that helps organizations stay on track with their strategic plans. It helps teams visualize goals, track progress, and identify areas of improvement to increase efficiency and effectiveness.

IMAGES
COMMENTS
consult this cybersecurity company business plan so as to get an idea. Sinq Tech is a standard and leading cybersecurity firm that is based in Mountain View - California here in the United States of America. We are in business to design cybersecurity solutions for our various clients - domestic and corporate.
Traditionally, a marketing plan includes the four P's: Product, Price, Place, and Promotion. For a cyber security business plan, your marketing strategy should include the following: Product: In the product section, you should reiterate the type of cyber security company that you documented in your company overview.
If you are planning to start a new business in the cybersecurity space, the first thing you will need is a business plan. Use our sample cyber security business plan created using upmetrics business plan software to start writing your business plan in no time.. Before you start writing your business plan for your new cybersecurity business, spend as much time as you can reading through some ...
The Cyber Guardian business is a startup cybersecurity company located in Burlingame, California. The company was founded by Lynn Frederick, who has a fifteen-year history working in the cybersecurity industry, in increasingly responsible roles. This expertise positions him to start and effectively grow a successful cybersecurity company.
This cybersecurity business plan sample is focused on the growing information technology (IT) security sector in Boston, Massachusetts. We hope this sample provides you with a brief foundation for starting your own cybersecurity company. Our cybersecurity business plan writers crafted this sample for your review.
A cyber security business plan is a strategic document outlining the objectives, strategies, and operations of a company focused on providing security solutions for digital assets. It serves as a ...
CYBEROAM: Cyber Security Business Plan - Free download as PDF File (.pdf), Text File (.txt) or read online for free. This is an in-detail B-Plan for a cyber security firm expanding its operations to IT and security audit. Financial outlay for the same has also been provided in the report.
What Is The Cybersecurity Business Plan (CBP)? The Cybersecurity Business Plan (CBP) is a business plan template that is specifically tailored for a cybersecurity department, which is designed to support an organization's broader technology and business strategies.The CBP is entirely focused at the CISO-level, since it is a department-level planning document.
The following Cyber Security business plan template gives you the key elements to include in a winning Cyber Security business plan. In addition to this template, a solid plan will also include market research to help you better understand market trends, your competitive advantage and your target customers. It will also help you craft your ...
Cyber Security Business Plan Example - Free download as PDF File (.pdf), Text File (.txt) or read online for free. Sinq Tech is a cybersecurity startup company being launched by John Gleeker, who has a Master's degree in Information Security and 10 years of experience working in cybersecurity. The company will provide cybersecurity solutions and services to business owners, government agencies ...
This article will outline how to start a security company business and the security company business plan (PDF, Word & Excel). Market Research. ... Look into various segments like residential, commercial, event security, and cybersecurity. Evaluate the size of these markets, growth trends, and the major players. Understanding where the industry ...
The document is a business plan template for a cyber security company that provides various cyber security services and products to corporate customers, institutions, and individuals. It includes sections on the business overview, management team, customers, marketing analysis, and sales strategy. The template guides the user through writing each section and includes examples and financial ...
Thank you for using the FCC's Small Biz Cyber Planner, a tool for small businesses to create customized cyber security planning guides. Businesses large and small need to do more to protect against growing cyber threats. As larger companies take steps to secure their systems, less secure small businesses are easier targets for cyber criminals.
Cyber Security Business Plan Example - Free download as PDF File (.pdf), Text File (.txt) or read online for free. Sinq Technology will be owned by John Gleeker and aims to secure clients' data from cyber threats. John has obtained experienced engineers and will rent an office near Mountain View, California. The startup costs will include equipment, software, and office expenses totaling ...
A Sample Cyber Security Business Plan Template. 1. Industry Overview. According to Ponemon Institute, within the year 2015, the costs associated with cyber crime was 19% higher than it was in 2014. Globally, a hack in 2014 cost companies on the average $7.7 million. This has led 20% of companies globally to create cyber crimes budget between $1 ...
Determine the services you will offer based on your expertise and target market. Start by offering a core set of services and gradually expand your offerings as your business grows. 7. Invest in Infrastructure and Tools. To provide reliable and efficient cybersecurity services, invest in robust infrastructure and cutting-edge tools.
White Paper: Your usiness Cybersecurity Plan 2 Introduction The frequency of news reports about cyber hacks and data breaches demonstrates that the threats to your IT infrastructure are never-ending—and that IT security is a moving target. IT security must be a priority for every business leader, no matter the size of their organization.
3. Set your goals. The goal of your security plan is to protect your small business. However, several smaller goals play into this larger objective. In a perfect world, creating a plan to prevent cyber attacks, and including a network security device like a firewall, would be enough.
The Cyber Security Plan template is designed to help IT security teams in organizations of all sizes and industries create a cyber security plan company-wide. It provides a comprehensive structure to define objectives, set measurable targets (KPIs), and implement related projects to achieve those objectives. 1.
Limit damage and quicken restoration of normal operations. The strategy for responding to and recovering from compromise: plan, prepare for, and conduct drills for cyberattacks as you would a fire. Make your reaction to cyberattacks and system failures an extension of your other business contingency plans.
1.2.4 Phase 4: Monitor the Strategy. In Phase 4, the cyber security strategy is assessed based on audits and/or cyber security exercises. The goal of this phase is to ensure that the mitigation strategies continue to be effective. This is done by evaluating each activity against the KPIs and identifying gaps.
1.1. Increase visibility into, and ability to mitigate, cybersecurity threats and campaigns. 1.2. Coordinate disclosure of, hunt for, and drive mitigation of critical and exploitable vulnerabilities. 1.3. Plan for, exercise, and execute joint cyber defense operations and coordinate the response to significant cybersecurity incidents. GOAL 2.